Report that millions of ``copies of existing repositories embedded with malicious code'' were uploaded to GitHub

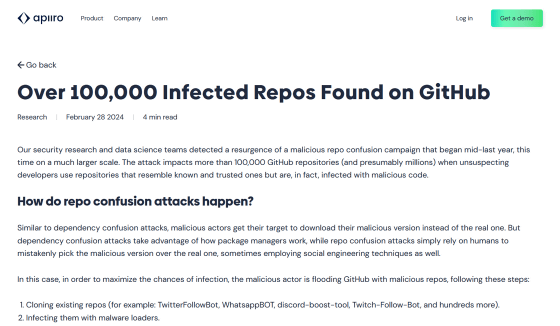
Over 100,000 Infected Repos Found on GitHub
https://apiiro.com/blog/malicious-code-campaign-github-repo-confusion-attack/
GitHub besieged by millions of malicious repositories in ongoing attack | Ars Technica
https://arstechnica.com/security/2024/02/github-besieged-by-millions-of-malicious-repositories-in-ongoing-attack/
GitHub under attack — millions of malicious cloud repositories bombard website | TechRadar
https://www.techradar.com/pro/security/github-under-attack-millions-of-malicious-cloud-repositories-bombard-website
In a repository disruption attack, an attacker clones an existing repository, injects it with malicious code, and uploads it to the platform. If another user downloads and executes a malicious repository, mistaking it for an existing repository, the embedded malicious code will be executed.
According to Gilady et al., attackers flood GitHub with malicious repositories using the following steps.
1: Clone existing repositories (TwitterFollowBot, WhatsappBOT, discord-boost-tool, Twitch-Follow-Bot, etc.).
2: Embed a malware loader .
3: Upload the malicious repository back to GitHub with the same name as the existing repository.
4: Fork a malicious repository thousands of times using automated systems.
5: Covertly promoting malicious repositories on forums and Discord.
When a tricked developer inadvertently runs a malicious repository, it unpacks seven layers of obfuscation and receives malicious Python code to execute the attack. The malicious code mainly consists of a modified version of the open source information stealing tool ``BlackCap-Grabber,'' which collects authentication cookies and login credentials from various apps and sends them to the attacker's server. is.

It seems that a repository disruption attack campaign has been underway on GitHub since May 2023, but in the first stage in May and the second stage from July to August, the targets were limited to a relatively small number of repositories. However, over 100,000 malicious repositories were detected between November and February 2024, and Gilady et al. estimate that the number of malicious repositories actually uploaded is in the millions. I am.
GitHub has tools to identify and remove uploaded repositories through an automated process, so most malicious repositories are removed within hours of upload. However, some malicious repositories are overlooked by the tools, and even if only 1% survive, there will be thousands to tens of thousands of malicious repositories on GitHub.
Gilady et al. wrote, 'The scope of this campaign is so wide that it can lead to secondary social engineering network effects, with naive users forking malicious repositories, sometimes without realizing that they are disseminating malware.' 'It's ironic that malware is spread by humans at a later stage that relies heavily on automation.' Attackers are targeting relatively niche repositories, making it easy for unsuspecting developers to make mistakes.
Mr. Gilady and his colleagues have already notified GitHub of the problem, and it seems that most of the malicious repositories have been deleted, but Mr. Gilady and his colleagues warn that the repository disruption attack campaign is still continuing.

According to technology media Ars Technica, supply chain attacks targeting software development platform repositories have existed since at least 2016. The software supply chain continues to be a promising target for attackers, with widely used libraries and packages being hijacked and attacks targeting software dependencies releasing malicious versions. Masu.
GitHub did not respond to Ars Technica's questions, but said in a statement: 'GitHub hosts over 420 million repositories and over 100 million developers, providing a safe and secure platform for developers. At GitHub, we have a team dedicated to detecting, analyzing, and removing content and accounts that violate our Acceptable Use Policy. We use machine learning and manual control to respond to ever-evolving adversarial tactics. We employ reviews and detection at scale, and we encourage our customers and community members to report abuse and spam.'
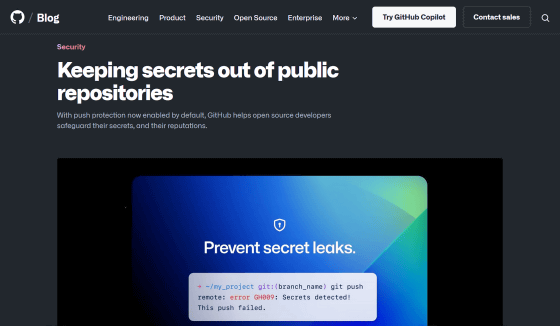
Additionally, GitHub reported in a blog post on February 29th that it has enabled push protection by default for all users. As a result, if it is detected that a commit contains confidential information such as an API key or token, the commit will be automatically blocked, preventing the accidental leakage of confidential information.
Keeping secrets out of public repositories - The GitHub Blog
https://github.blog/2024-02-29-keeping-secrets-out-of-public-repositories/
GitHub enables push protection by default to stop secrets leak
https://www.bleepingcomputer.com/news/security/github-enables-push-protection-by-default-to-stop-secrets-leak/
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik