A method to send and receive data for free on a network built with Apple devices is devised

On April 30, 2021, Apple's genuine
Send My: Arbitrary data transmission via Apple's Find My network | Positive Security
https://positive.security/blog/send-my
◆ Mechanism
According to Positive Security, AirTag will generate a public / private key pair during initial setup. AirTag sends the public key to the outside using the broadcast function of Bluetooth Low Energy every 2 seconds. When an Apple device operating around AirTag detects the data of the public key sent by AirTag, it encrypts its own location information (approximate location information of AirTag) with the public key and sends it to Apple. Users looking for AirTag can confirm the location information of AirTag by asking Apple for the public key of AirTag and decrypting the 'location information encrypted with the public key' returned from Apple with the private key. It is a mechanism.
What is the mechanism of the 'Find My' function that can be located even on offline terminals announced by Apple? --GIGAZINE

At this time, Apple does not hold information about 'which AirTag is associated with which public key'. For this reason, Positive Security thought that by generating a 'public key in the same format as the public key generated by AirTag' with embedded data, it would be possible to send and receive data for free on the 'search' network.
◆ Sender
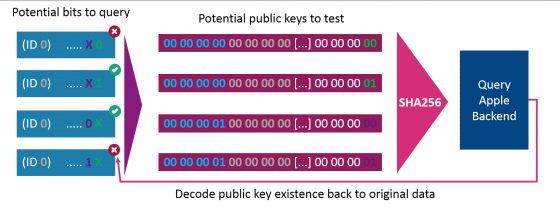
The data transmission / reception method created by Positive Security looks like this. The data sender divides the data into bits, and 'the first bit of data XX is XX (0 or 1)', 'the second bit of data XX is XX', '...', 'data'. The nth bit of ○○ is processed into the format of ○ ”. The public key that is actually completed is 'a value indicating the order of 4-byte bits', '4-byte data ID', '4-byte sender-specific ID', '
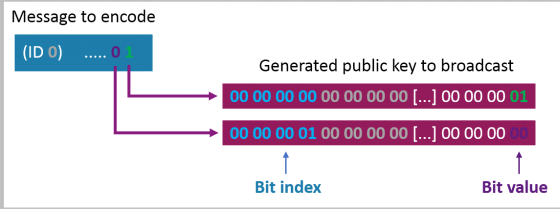
Once the data has been processed, it will be sent externally as the AirTag public key, following the
◆ Receiving side
The data receiving side adds 'a value indicating the order of 4-byte bits' and 'a value of 0 or 1' to the '4-byte data ID' and '4-byte sender-specific ID' that are known in advance. The data is received by requesting the added public key from Apple and arranging the values of the one for which the location information is returned from Apple.
In other words, request Apple for location information encrypted with the public keys '○○○ …… 0' and '○○○ …… 1', and the location encrypted with '○○○ …… 0'. When the information is returned, it is known that 'the XXth bit of data XX is 0', so by repeating this, it is possible to receive up to 16 bytes of data such as '001011010 ...'.
◆ Implementation
Positive Security has developed hardware that transmits data using the above method based on the
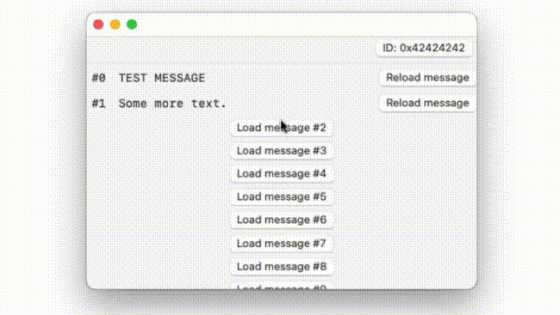
As a result of actually sending and receiving data, it was said that it succeeded in transmitting data at a speed of 3 bytes per second and receiving 16 bytes of data in a maximum of 5 seconds. Positive Security says, 'The data transmission / reception method we have created this time can be used for uploading data from small devices and sensors that are not connected to the Internet.' 'Apple uses this method because of the' search 'network mechanism. It can be difficult to prevent. '
In addition, Positive Security has named the devised method 'Send My' and publishes the source code of the developed firmware and software on the GitHub repository.
Related Posts:
in Hardware, Web Service, Posted by log1o_hf