Security researchers point out that more than 1.5 billion iPhones and Macs are vulnerable to leaking phone numbers and email addresses
Apple AirDrop shares more than files – Computer Science – Technical University of Darmstadt
https://www.informatik.tu-darmstadt.de/fb20/ueber_uns_details_231616.en.jsp
AirDrop makes it easy to send and receive data such as photos and videos between Apple devices. By default, the people who can exchange data with AirDrop are limited to those who the user knows the contact information, but in order to find out 'which device belongs to the person who knows the contact information', A mutual authentication mechanism works between Apple devices to identify which device you know.
According to a research team called ENCRYPTO, which conducts cryptography and privacy-related research at the Technische Universität Darmstadt, there are serious privacy-related vulnerabilities in this AirDrop mutual authentication mechanism.

The vulnerability discovered by ENCRYPTO is related to the mutual authentication mechanism between Apple devices when using AirDrop. In this mutual authentication mechanism, information such as telephone numbers and email addresses associated with terminals is obfuscated using a
Therefore, it seems that an attacker will be able to extract personal information such as phone numbers and email addresses from strangers' Apple terminals. All you need to do is a Wi-Fi-enabled device and an Apple device with iOS or macOS, just physically close to the Apple device user who has the AirDrop detection process open and the AirDrop setting turned on. You can attack.

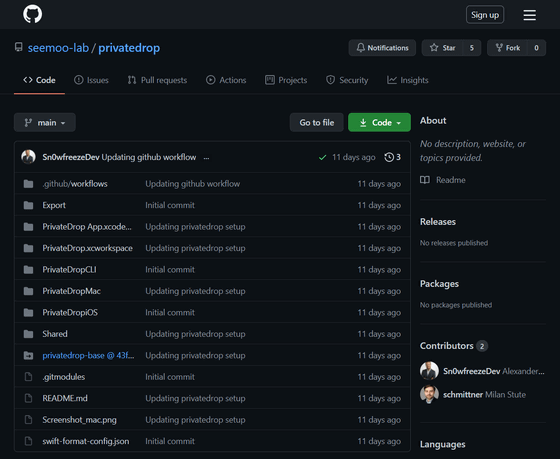
ENCRYPTO is developing its own file sharing tool ' PrivateDrop ' that fixes the AirDrop vulnerability. With PrivateDrop, it will be possible to safely run the mutual authentication mechanism between terminals without exchanging weak hash values. Also, since there is little delay when running the mutual authentication mechanism, it seems that it is 'sufficiently efficient' even if it is adopted for the existing AirDrop.
The source code for Private Drop is available on GitHub.
GitHub --seemoo-lab / privatedrop
https://github.com/seemoo-lab/privatedrop
In May 2019, ENCRYPTO reported to Apple about the AirDrop vulnerability. However, at the time of writing the article, Apple has not worked on fixing the vulnerability, so 'more than 1.5 billion Apple devices worldwide are at risk of privacy invasion,' ENCRYPTO points out.
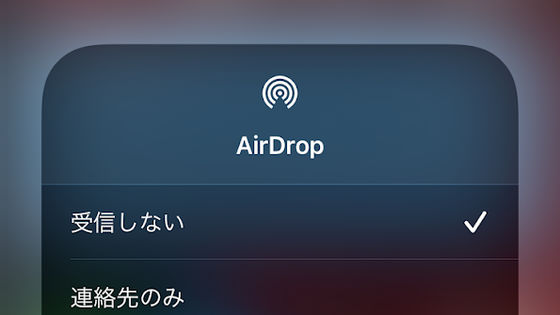
Therefore, ENCRYPTO recommends that Apple terminal users change the AirDrop setting to 'Do not receive'.
Related Posts: