What kind of scars did the vulnerabilities 'Specter' and 'Meltdown' that shook the IT industry leave on CPU performance?

by
The CPU vulnerabilities revealed in early 2018, Specter and Meltdown , were serious problems rooted in most of the mainstream CPU designs at the time, and the entire IT industry has addressed them. It caused great confusion such as being pressed . The impact of these two vulnerabilities on CPU performance is highlighted by a thorough benchmark measurement by Linux-related news site Phoronix.
A Look At The CPU Security Mitigation Costs Three Years After Specter / Meltdown --Phoronix
https://www.phoronix.com/scan.php?page=article&item=3-years-specmelt
3 Years CPU Security Mitigations Performance --OpenBenchmarking.org
https://openbenchmarking.org/result/2101067-HA-MITIGATIO26
Both 'Specter' and 'Meltdown' pointed out that 'all processors have a problem that both safety and speed cannot be achieved' when a problem is found because it was caused by a method related to CPU speedup. it was done.
It is pointed out that the root of the vulnerability problem inherent in Intel CPUs is deeply rooted, 'all processors have a problem that both safety and high speed cannot be achieved' --GIGAZINE
In the third year since the vulnerability was discovered, Phoronix will run various benchmark tests on Intel and AMD CPUs to determine the impact of the security measures they have taken on their CPUs. I decided to. This time, Phoronix conducted a benchmark test on the following 11 CPUs in total.
・ Intel
Core i7 4770K
Core i7 5775C
Core i7 7700K
Core i7 8700K
Core i9 9900K
Core i9 10900K
Core i9 10980XE
・ AMD
Ryzen 7 1800X
Ryzen 9 3950X
Ryzen Threadripper 3970X
Ryzen 9 5950X
For the CPU test environment, Ubuntu 20.10 and Linux 5.10, which is the latest Linux kernel at the time of writing the article, are used. Benchmark tests were executed in two parts, the default state with security measures enabled and the state with security measures disabled, and the results were summarized for each CPU.
◆ Browser (Mozilla Firefox)
According to Phoronix, browser performance is the most noticeable impact of security measures. Therefore, Phoronix first conducted a benchmark in Firefox 84 to measure the execution time and processing power of JavaScript functions.
' ARES-6 ' is a JavaScript-based benchmark. In each bar graph, the red color shows the default state with security measures enabled, and the blue color shows the result with security measures disabled (mitigations = off). The lower the value, the better the result. Click the image to enlarge it.
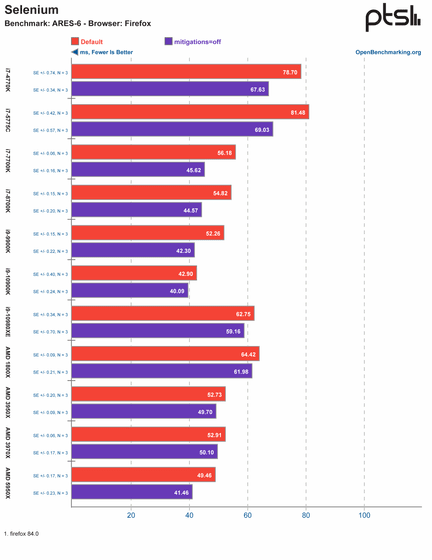
'
'
JetStream is a JavaScript benchmark developed by Apple's WebKit team. The higher the number, the better.

'

'

'We've seen performance degradation on all CPUs, but the impact was especially noticeable on older CPUs that hadn't been redesigned,' Phoronix points out.
◆ Browser (Google Chrome)
Similar benchmarks have been tested on Chrome 87. In addition, 'JetStream' is excluded.
'ARES-6'

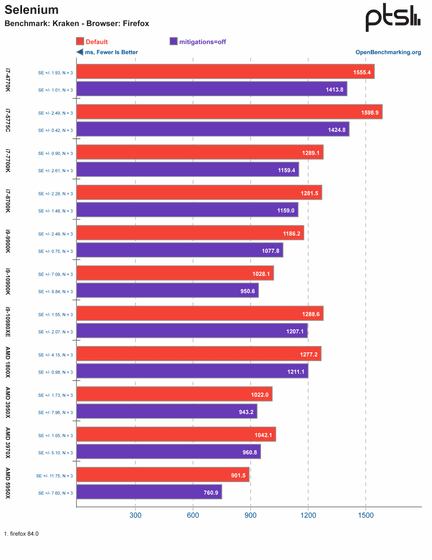
'Kraken'

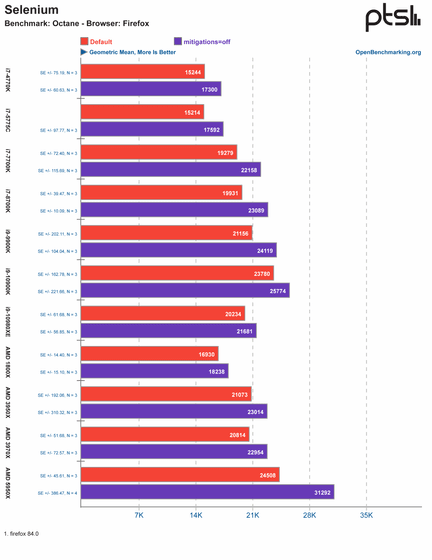
'Octane'

'Jet Stream 2'

'Speedometer'

Chrome tended to perform better than Firefox overall, but like Firefox, older CPUs had a significant performance impact, Phoronix said.
◆ Encryption / decryption
Phoronix then performed benchmark tests using
First, the test result of the encryption speed at 256 bits is as follows. The unit is mebibyte per second, and the higher the number, the better.

Then the result of decoding is as follows.

Similarly, with 512-bit encryption ...

This is the result of decryption.

'On older Intel CPUs and all AMD CPUs used for testing, improvements in kernel drivers tended to give better performance, at least in AES-XTS format encryption algorithms,' Phoronix said. It was.
Also, the time it took to compile the code made little difference except for older CPU models.

◆ Input / output
The test results of transaction processing speed using ' PostMark 1.51 ' are as follows. The higher the number, the better.

Phoronix said, 'In I / O, the result is that performance degradation tends to occur mainly in old Intel CPUs that have surpassed the emergency with
In addition, the following is a test result of data transfer speed using the network performance measurement tool ' Ethr ' written in Go language , and the higher the number, the better.

Throughput test results using '


◆ AI performance
Next was a benchmark test using Alibaba's
' SqueezeNet '

'

'

'

Regarding this result, Phoronix commented, 'We found that security measures also affected the performance of MNN, but fortunately it did not make a difference on new CPUs with hardware measures.' did.
◆ Summary
Below is a graph of the results of all the tests conducted by Phoronix, and the higher the number, the better.

Phoronix commented on the results of this benchmark test, 'If you look at Intel's CPU, the performance of Core i7 7700K and 8700K has dropped to about 75% due to security measures, but Core i9 10900K with hardware measures built in. You can see that the performance is maintained up to about 95% or more, and in AMD, the strong protection of the Zen 3 architecture increases the overhead, so even the latest Ryzen 9 5950X tested. Fortunately, the AMD Zen 3's CPU is so fast that it's minimal compared to the performance degradation expected in January 2018 when the example vulnerabilities were revealed. I can say. '
Related Posts: