What is the impact of the patch for CPU vulnerability issues on substantial CPU performance?
by
In January 2018, a 'meltdown' vulnerability that exists as a design flaw in Intel CPUs and a 'spector' that could affect all CPUs were discovered , causing a great deal of confusion. Microsoft and other companies have responded by applying a patch, but the results of testing the effect of this patch on Intel and AMD CPU performance have been published.
The Performance Impact Of MDS / Zombieload Plus The Overall Cost Now Of Specter / Meltdown / L1TF / MDS-Phoronix
https://www.phoronix.com/scan.php?page=article&item=mds-zombieload-mit&num=10
Intel Performance Hit 5x Harder Than AMD After Specter, Meltdown Patches-ExtremeTech
https://www.extremetech.com/computing/291649-intel-performance-amd-spectre-meltdown-mds-patches
'Meltdown' and 'Spector', which are CPU vulnerability issues, were dealt with as very serious issues, and companies were forced to respond. It is pointed out that while security is secured by the patch for vulnerability handling, speed is sacrificed at the same time.
The root of the vulnerability problem inherent in Intel CPUs is deeply pointed out that 'all processors have problems in which security and speed can not be compatible'-GIGAZINE
Under these circumstances, a news site ' Phoronix ' that provides hardware reviews and related news for Linux performs performance tests using CPUs made by Intel and AMD, and 'How does the vulnerability patch affect performance?' It measured about.
The CPUs used were a total of five CPUs: Intel Core i7-6800K , Core i7-8700K , Core i9-7980XE , and AMD Ryzen 7 2700X , Threadripper 2990WX . We measured when the patch was turned on and when the patch was turned off, respectively, and examined the decline in performance.
This is an image that is graphed by geometric averaging the results measured using many benchmark tools. From the top of the image, Intel's Core i7-6800K, Core i7-8700, Core i9-7980XE, and AMD's Ryzen 7 2700X, Threadripper 2990WX. Performance when the pink bar does not apply the patch, the brown bar shows the performance when the patch required for each CPU is turned on, and the gray bar uses the simultaneous multithreading (SMT) Intel CPU It is the performance when SMT is turned off to disable the attack that exploits the vulnerability. Note that there is no gray bar for AMD CPUs, as AMD CPUs do not have to be turned off to disable the vulnerability.
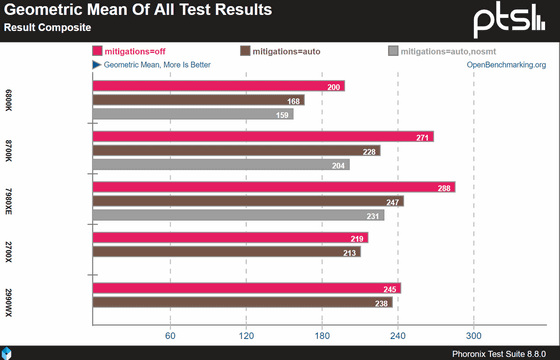
The graph shows that all CPUs perform well when vulnerability countermeasure is turned off, and applying patch or turning off SMT shows that the performance is lowered. When the patch is turned on, the performance reduction width is larger for Intel CPUs and is about 15 to 16% even with SMT turned on, 20.5% for Core i7-6800K when SMT is turned off, Core i7-8700 The performance was reduced by 24.8% on Core i9-7980XE and by about 20%. On the other hand, the performance degradation of AMD CPUs is not as large as that of Intel CPUs, and is less than 3% for both Ryzen 7 2700X and Threadripper 2990WX.
If no vulnerability measures are taken, Core i9-7980XE has the highest performance, followed by Core i7-8700 and Threadripper 2990WX. However, in terms of performance when Intel's CPU vulnerability measures have been thoroughly implemented, it can be seen that Threadripper 2990WX, which has a small reduction in performance, is at the top of the performance. Since the results of this time are averages of several test results, there are variations depending on the benchmarking tools, but turning on vulnerability measures will substantially change the actual CPU performance.
However, despite this result, AMD did not advertise that 'the substantial performance is higher than Intel CPU', and there are signs that vulnerabilities such as meltdown and spector had a positive impact on AMD's business. I can not see it. In this regard, Technology Media's Extreme Teck does not guarantee that a critical vulnerability will not be found in AMD CPUs in the future. It is because it may be regarded as a problem at the time of discovery and it may lead to danger such as getting a lawsuit. '
However, Extreme Teck has stated that CPU performance will obviously be affected by the fact that fixes from vulnerabilities will continue to overlap, regardless of whether the semiconductor manufacturer itself is appealing.
Related Posts:
in Hardware, Posted by log1h_ik