Hacking the HDD controller enables interception of data and installation of Linux on the HDD board

In addition to components such as platters that store data and magnetic heads that read and write data, HDDs are made up of various components such as hard disk controllers and cache chips. Among them, although hard disk controller is the part that the manufacturer does not publish the details, the controller portion of such HDD Spritesmods Sprite_tm (real name: Jeroen Domburg), which operates the Mr. hacked, describes the process.
Sprites mods-Hard disk hacking-Intro
http://spritesmods.com/?art=hddhack
HDDs are usually assigned a serial number called LBA for each 512-byte sector , and the computer reads and writes data on the HDD for each sector. Sprite_tm points out that the mechanical operation of the HDD is a 'very simple' structure in which the magnetic head reads and writes data from and to the platter. However, HDD has a function to handle information such as bad sector and SMART management, and this ability leads to the possibility of hacking. Due to his interest in hacking, Sprite_tm started a study for hacking that breaks through HDD software security.
◆ Printed circuit board
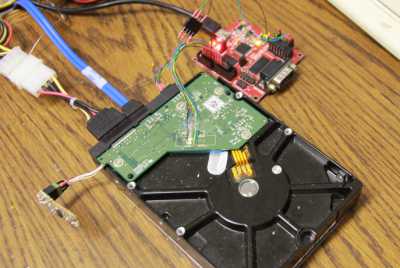
The WD HDD 'WD20EARX' was used for this survey. Although the mechanical parts of HDD such as magnetic heads and platters are known areas, Mr. Sprite_tm is not interested in such mechanical parts but in the printed circuit board with SATA connector and power connector. The printed circuit board built into the HDD looks like this.

There are several chips mounted on the printed circuit board, one of which is DRAM . The DRAM installed in the HDD is not special, and it can be confirmed on the data sheet. The capacity is 8MB to 64MB, which is equivalent to the HDD cache size.

The second tip is the spindle motor controller, a special tip that is difficult to see in the datasheet. It is a chip that controls power supply as well as motor control. Sprite_tm says ST 's 'SMOOTH' chips are the most used.

The third chip is 64KB to 256KB of flash memory. It seems that this flash memory stores the program that the hard disk controller starts, but depending on the model of HDD, it may be written directly to the hard disk controller instead of implementing the flash memory for the program. ..

Although it is not a chip, a piezoelectric shock sensor is also mounted on the printed circuit board. It can be used to retract the head when the HDD receives a mechanical shock due to falling, etc., but in fact it can only be flagged when the HDD falls to show that the warranty is invalid It is highly likely, Sprite_tm pointed out.

The fourth chip is the hard disk controller, 'where all the fun happens', says Sprite_tm. In addition to LSI manufacturers such as Marvell and ST, hard disk controllers may be manufactured in-house by HDD manufacturers such as Samsung and Western Digital (WD) . Sprite_tm says it's the most important part, but it's one that doesn't give us much information when looking for a chip datasheet.

◆ Controller operation by JTAG port
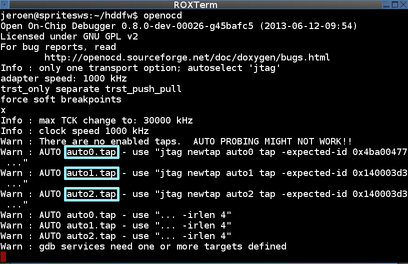
Mr. Sprite_tm decided to investigate the hard disk controller by referring to the information posted in the thread on the HDD Guru forums , 'You can freely operate the hard disk controller by using the JTAG port'. The red board is a USB serial conversion module called FT2232H, and this board is connected to the JTAG port of the HDD. He used OpenOCD as his debugging software.
Debugging revealed that Marvell's ARM compatible core 'Feroceon' has 2 cores, 'Cortex-M3' has 1 core, and the hard disk controller has 3 ARM cores. The first Feroceon core controls physical reading and writing, and the second Feroceon core operates the SATA interface. It seems that Cortex-M3 did not affect the operation of the HDD even if it stopped operating.
Sprite_tm's ultimate goal is to break through HDD security. Mr. Sprite_tm speculates that the DMA on the HDD may be accessing the data on the platter by relying on the DRAM cache. The cache is controlled by the second Feroceon core, so Sprite_tm decided to examine the memory map of the second Feroceon core.
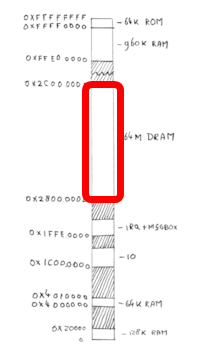
The memory map of the second Feroceon core is fragmentary, with scattered RAM, IO, IRQ space, and internal boot ROM space. Sprite_tm found a large segment of 64MB in the memory map of the Feroceon core, which seems to be a DRAM chip with a built-in cache.
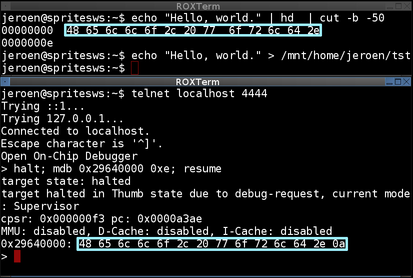
When I mounted the DRAM and wrote 'Hello World!', I could confirm the data corresponding to 'Hello World!' from the Feroceon core.
◆ Cache dump and code insertion
In order to know the behavior of the cache, it is necessary to dump and investigate the entire cache memory, but this is not a straightforward matter, Sprite_tm. Traditional ARM instructions and Thumb instructions are mixed, and the code that issues error messages was not included. However, since WD did not obfuscate the firmware and the chip can be operated by the JTAG port, Sprite_tm managed to reach the core of the cache function. Below is a RAM table that Sprite_tm calls a 'cache descriptor table'. Each element in the table holds the first LBA of the data to be cached, the length of the data, the cache status, etc. The DMA accesses the data on the platter based on the information in these caches.

Sprite_tm says that in order to intercept the data exchange between the HDD and the computer, it is necessary to execute its own code on the hard disk controller at the appropriate time. HDD data is sent and received via the SATA port, but since the second Feroceon core performs SATA control, the SATA hardware initialization process of the Feroceon core cannot be used as the timing of code execution. Kato Sprite_tm is pondering. After trial and error, he found the timing of initialization and succeeded in embedding his own code in an appropriate place.
This is the assembler code before Mr. Sprite_tm modified it.
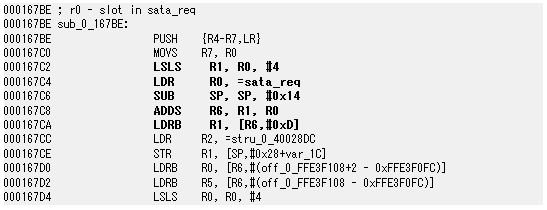
Below is the code modified by Sprite_tm. It executes a routine called changeThingsInCache, then jumps to the address where the original code is and performs the same process as the original code. This will allow you to bypass the HDD read/write process.
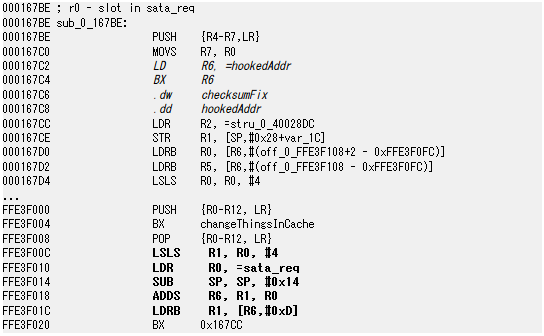
For example, it is possible to rewrite the value of the sector in the cache by using the initialization of the SATA device as a hook.
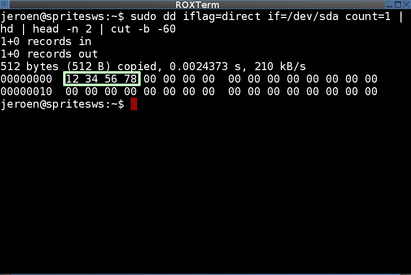
◆ Permanence of code modification
HDD hacking is now complete, but Sprite_tm is also particular about program persistence. The code exists in RAM, so even if you change it, it will be restored when you restart the HDD. To solve this problem, Sprite_tm decided to place the program in flash memory. Flash memory is ported on the Vero board to make it easier to insert and remove memory.
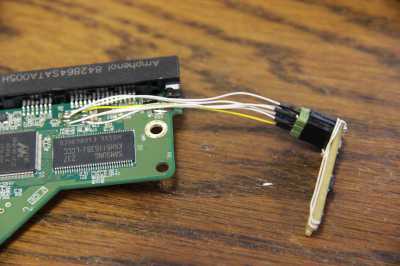
The data format to write to flash was clear, but the code itself was compressed with an unknown algorithm, so I couldn't insert the code that would hook directly. So Sprite_tm added a block of flash memory and reassembled the flash memory binary with his own tool 'fwtool' so that the additional block is executed before other blocks. After writing the modified binary to the flash memory, it seems that the program was made persistent.
◆ Achieved hacking
However, Mr. Sprite_tm has not yet been able to execute the 'hacker scenario I imagined'. Removing the flash memory from the board seems to be the reason why it is out of the scenario, and it is necessary to find a way to write the binary while the flash memory is soldered to the board, Sprite_tm said.
The scenario that Sprite_tm envisions was made possible by WD's firmware upgrade tool for DOS and idle3-tools , a group of tools for HDD made by WD using the Linux SCSI driver. By incorporating this code into fwtool, it seems that the flash memory of the HDD can be read and written via SATA.
By doing the operations so far, Sprite_tm, if a malicious hacker got root authority of the server with the drive used this time, modify the HDD flash memory with fwtool and intercept the server data itself. It will be possible to modify. For example, an attacker can change the password by operating '/etc/shadow', which stores password information in Linux. In addition, Sprite_tm says that this method can be used not only for misuse, but also for data protection such as creating a complete clone disk.
Below is a demo movie that actually modifies '/etc/shadow' to change the root password.
The hard disk controller is equipped three ARM cores, for the serial port UART and at least two SPI because there are interesting with Mr. Sprite_tm as controller boards. We have also released a movie that attempts to boot Linux by writing the Linux kernel and initrd on the controller board. The kernel and initrd are packaged in a size of 1 sector, and the Linux kernel is read by the trigger of writing 'HD, lnx!'. Since the hard disk controller does not have an MMU , it needs a bit of user space formatted in a special format, but it could not be built into the kernel and Linux failed to boot. However, Sprite_tm seems to be a little proud of having installed Linux on the controller board.
Mr. Sprite_tm pointed out that although hard disk controllers have many unknown areas, it is possible to write reverse engineering and custom code, and the board itself can still be used even with a broken HDD. “Publishing the source code of a security project is always a nuisance,” said Sprite_tm, who is cautious about exposing all the source code used for hacking, and only the incomplete code. It is open to the public.
(tgz file) hddhack.tgz
http://spritesmods.com/hddhack/hddhack.tgz
Related Posts:







