Potential for Windows patches for CPU vulnerability "Meltdown" in January and February 2018 may lead to another situation worse

Bylaboratorio linux
Revealed at the beginning of January 2018Intel, AMD and ARM CPU related vulnerabilities "Spectre" and "Meltdown"Is a problem that the mechanism of "speculative execution" technology for speeding up the CPU becomes a security hole that leads to information leakage as it is, after this case was reported with shockThe situation where each company is chased by responsehave become. A patch that dealt with the problem after January has been released from Microsoft, but from security expert's investigation, by applying January and February patch, another problem in Windows 7 and Server 2008 R2 It is obvious that there is a possibility that the situation may get worse.
Security | DMA | Hacking: Total Meltdown?
http://blog.frizk.net/2018/03/total-meltdown.html
This problem is a security expert Ulf Frisk (@ UlfFrisk) I found out by Mr. and made it clear on my own blog.
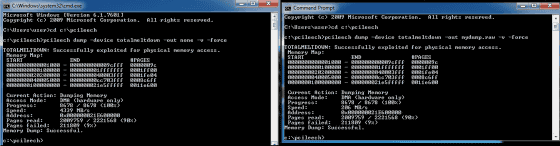
According to Ulf Frisk, indeed the patch of January 2018 has succeeded in halting the Meltdown problem, but every process accesses the contents of the memory at a speed of several gigabytes per second, and at any address It is said that it is possible to write information. There are no special APIs or system calls required to perform this problem, and it is provided with Windows 7Virtual MemoryJust use the function to read and write memory.
Screen capture when Ulf Frisk actually vulnerable has been released. On the left screen, the access speed is displayed as "4339 MB / s", which shows that you can access at speeds of 4 GB / sec or more, while the speed of dumping data to the disk depends on the transfer speed It is said that it is becoming a bottleneck and becoming late.
The cause of this problem is that the user or supervisor authority bit is included in the entry of PML 4, he said. This makes page tables that should normally only be accessible by the kernel available to user mode code of all processes.
In Windows 7, the self-referencing destination of PML 4 is fixed to "position 0 × 1 ED, offset 0 × F 68", which means that when it is replaced with virtual memory it is mapped to "address 0 × FFFFF 6 FB 7 DBED 000". Normally, it is a memory address that only the privileged kernel can use, but by setting a bit indicating permission incorrectly to the user, it becomes possible to see an address which should not be originally seen, so that it can be accessed internally It is said that it will become.
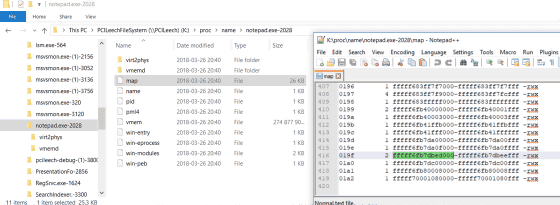
This problem has been published in GithubPCILeech direct memory access attack toolkitBy using, it is possible that anyone can reproduce oneself. Just download the program and execute it with the device type "-device totalmeltdown" on the vulnerable Windows 7 machine.
The following screen shows the situation when actually executing, and it shows that the memory map and the state where access is done to PML 4 are shown.
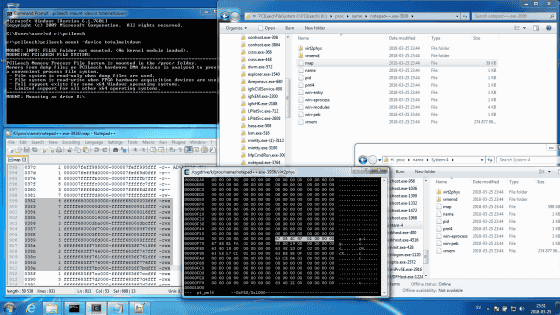
Affected by this problem is a 64-bit version of Windows 7 and Server 2008 R2 machines that patched January 2018 and February. If you do not apply the patch after December 2017 or if the patch after March 2018 is hit, no problem will occur, so if you are aware of it, It is better to introduce it.
To solve this problem, Intel announced that CPU will be released at the hardware level in the second half of 2018 to solve the problem of "Specter" and "Meltdown".
Intel announced that CPU will be released at the hardware level for vulnerability "Spectre" "Meltdown" in late 2018 - GIGAZINE
Related Posts: