Procedures for reading the protected area of the microcomputer using 'processor exception handling' are available, and source code is also available

Important data of microcomputers is usually protected by a “read protection function” that restricts data reading, but ways to avoid this function are being researched and developed daily by security researchers and others. Embedded engineers Marc Schink and Johannes Obermaier have posted on their blog how to bypass the protection of one of the microcontrollers, the
Exception (al) Failure-Breaking the STM32F1 Read-Out Protection | blog.zapb.de
https://blog.zapb.de/stm32f1-exceptional-failure/
In the STM32F1 series, an attacker can use the debug function if physical access is possible. When an exception occurs in the program, the processor also reads the exception processing address indicated on the vector table to the program counter (PC) at the same time.To make this reading possible, the read protection function of the STM32F1 series It targets only the DCode bus and does not block memory access from the ICode bus. By using the processing of the ICode bus, read-protected information can be read.
It seems that the method of 'adding an exception to the vector table' is a method that exploits a general vulnerability, but this method can not be used because there is no space in the vector table in the STM32F1 series.
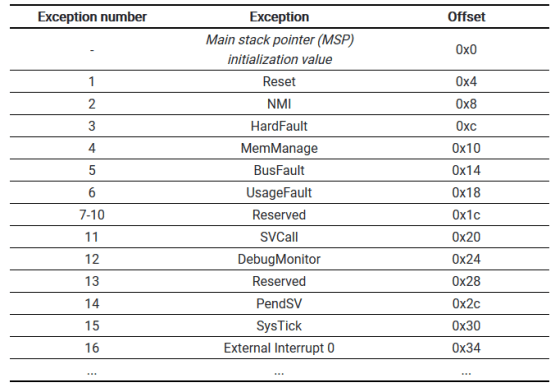
An alternative to the 'add exception to vector table' method is to 'use vector table offset'. Since the attacker can enter the debug state, the vector table can be replaced using the 'vector table offset registration function (VTOR)' included in the STM32F1 series CPU 'ARMv7-M'.
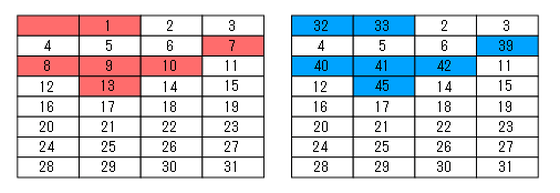
For special exceptions and reserved data shown in red in the figure in the vector table, data cannot be extracted even by replacement with VTOR, but this limitation is set to 'Exception replacement with an exception number larger than the size of the vector table. 'It can be avoided by doing. In this case, the table size is 32, so if you replace exceptions with exception numbers of 32 or more, you can extract data for all exceptions in the vector table.
Explains how to raise an exception. First, it is necessary to use an
[code] cortex_m maskisr off [/ code]
To generate one of the exceptions, “BusFault” exception and extract data, execute the unallocated memory space “0xf0000000” in STM32F1 series. Then, a BusFault occurs, and the exception processing address is saved on the PC.
[code] mwh 0x20000000 0x0868
reg r1 0xf0000000
reg pc 0x20000000 [/ code]
The 'MemManage' exception that occurs when trying to execute an execution-prohibited memory area can be raised by executing the following command.
[code] reg pc 0xe0000000 [/ code]
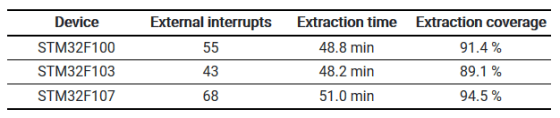
According to a test that used this vulnerability to attack the STM32F1 series, it was found that approximately 90% of data in flash memory could be extracted. Marc and Johannes have concluded that 'the read protection feature of the STM32F1 series has been breached,' and argue that the use of the feature should be avoided.
A movie that actually hacks the STM32F1 series has also been released.
The script used in the movie can be confirmed from the following.
zapb / stm32f1-firmware-extractorGitLab
https://gitlab.zapb.de/zapb/stm32f1-firmware-extractor
Related Posts: