NSA releases report summarizing safety of video conferencing tools such as Zoom and Microsoft Teams
Selecting and Safely Using Collaboration Services for Telework
https://media.defense.gov/2020/Apr/24/2002288652/-1/-1/0/CSI-SELECTING-AND-USING-COLLABORATION-SERVICES-SECURELY-LONG-FINAL.PDF
Here's the NSA's guide for choosing a safe text chat and video conferencing service | ZDNet
https://www.zdnet.com/article/heres-the-nsas-guide-for-choosing-a-safe-text-chat-and-video-conferencing-service/
The tools evaluated are Cisco Webex , Dust , G Suite , GoToMeeting , Mattermost , Microsoft Teams , Signal , Skype for Business , Slack , SMS , WhatsApp , Wickr , Zoom . NSA evaluates the security of each tool with the following 8 points.
◆ 1: Do you implement end-to-end encryption?
NSA says it's important not only to encrypt everything from the sender to the recipient, but also to carefully exchange encryption keys. Note that large video chats do not implement end-to-end encryption due to performance issues.
◆ 2: Is communication encryption based on strong and well-known testable encryption standards?
Even when there is no end-to-end encryption, the NSA recommends the use of strong cryptographic standards and states, 'It is preferable to use publicly available protocol standards such as TLS , DTLS , SRTP. ' I will.
◆ 3: Is multi-factor authentication available?
To use each tool, NSA requires a mechanism that allows access to existing accounts using multi-factor authentication such as code, token, biometric authentication.

◆ 4: Can the user see and control who connects to the session?
The NSA said, 'Whether features such as login passwords and waiting rooms can be used to limit access to sessions to only invited people, and joining a session should support reasonably strong authentication.' is.
◆ 5: Does the privacy policy allow sharing of information with third parties or affiliates?
Meeting tools are required to protect sensitive data such as contact details and content. Various information that may endanger the organization, such as metadata related to user identities, device information, session history, etc. should not be shared with third parties and should be specified in a privacy policy if it is. there is.
◆ 6: Can users safely delete data from services and repositories as needed on both clients and servers?
NSA said, 'I don't think there is a service that fully supports the secure overwriting / deleting of data, but users can delete data such as shared files and session content, and permanently delete obsolete accounts. You should be given the opportunity to remove it. '
◆ 7: Is it developed with open source?
◆ 8:
And the table below summarizes the evaluation. The second 'Basic Functionally' from the left summarizes the functions of each tool, including text chat (a), voice chat (b), video chat (c), file sharing (d), screen sharing (e). I will. And the answer to each question is written as 'Yes (Y)' or 'No (N)'.
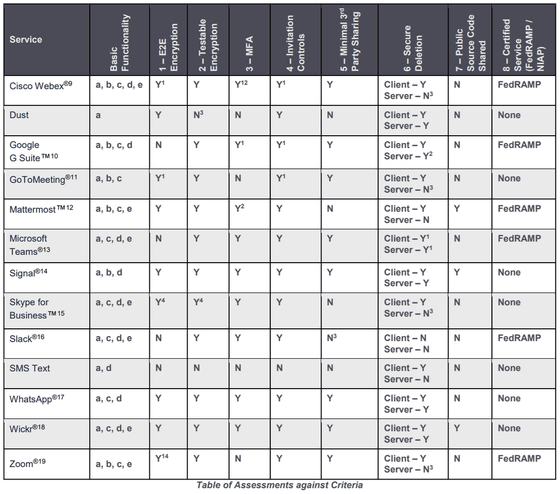
Although Microsoft Teams and Google G Suite meet the standards required by NSA in various points such as strong encryption, multi-factor authentication, FedRAMP compliance, personal data is shared with third parties and development companies, and it is specified in the policy. I am. Slack, which is widely used in Japan, cannot freely delete data on either the client side or the server side.
Also, while Zoom is FedRAMP compliant, it does not use multi-factor authentication for user authentication. In addition, Zoom is reported to leak personal information of users and security problems.
It turns out that a part of the encryption key of the online video conferencing application `` Zoom '' is issued from `` China server '', vulnerable to `` waiting room '' function-GIGAZINE

The reason why NSA published the security assessment report of each tool was 'To inform military organizations, public institutions, and private companies about the characteristics of each of the major tools collectively, and to establish appropriate security systems in each organization, To prepare for threats such as attackers with attacks. '
Related Posts:
in Software, Web Service, Security, Posted by log1i_yk