It turns out that some of the encryption keys of the online video conferencing application `` Zoom '' are issued from `` China server '', vulnerable to `` standby room '' function

With the spread of the new coronavirus infectious disease (COVID-19) widespread, many countries are making recommendations to refrain from unnecessary and urgent outings, and 'working from home' has become popular. With the growing demand for online video conferencing apps used for working from home, one of the online video conferencing apps,
Move Fast & Roll Your Own Crypto: A Quick Look at the Confidentiality of Zoom Meetings-The Citizen Lab
https://citizenlab.ca/2020/04/move-fast-roll-your-own-crypto-a-quick-look-at-the-confidentiality-of-zoom-meetings/
Zoom's Flawed Encryption Linked to China
https://theintercept.com/2020/04/03/zooms-encryption-is-not-suited-for-secrets-and-has-surprising-links-to-china-researchers-discover/
Zoom has previously been pointed out with security and privacy issues such as ' vulnerabilities that could launch a Mac webcam without permission ' and ' sending data to Facebook without user permission .' If you read the following article, you can see that Zoom had several problems.
`` Zoom '' of online video conferencing application with security & privacy related issues in succession-gigazine

A new problem emerged in such Zoom. On April 3, 2020, the academic institution Citizen Lab belonging to the University of Toronto of Canada regarding network neutrality and security says that the encryption key is passing through a Chinese server `` vulnerability in the ' waiting room ' function Exists. '
According to Zoom's official commentary, when you start an online video conferencing ( meeting ) with Zoom, a server belonging to Zoom's cloud infrastructure generates an encryption key. Each user who attends the meeting is given the same encryption key via the encryption system Transport Layer Security (TLS) .
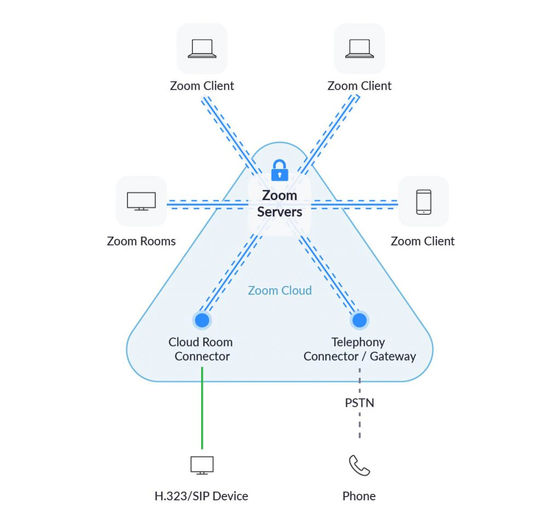
Citizen Lab points out that this encryption key 'may be stored on a Chinese server.' Depending on the meeting setup, a copy of the encryption key is stored on Zoom's server called a 'connector'. There are 73 servers belonging to the key management system, but according to a survey by Citizen Lab, five of them are located in China. It seems that the encryption server is stored in which connector server does not depend on the user's area of use, Citizen Lab researchers living in the United States and Canada said, `` Clearly the encryption key was sent from the connector server in Beijing '
Citizen Lab noted that if encryption keys were stored on a server hosted in China, server owners had a

In addition, Citizen Lab points out that Zoom's 'encryption' itself is vulnerable. Zoom makes use of the
The second problem is a defect in ECB mode. Since ECB mode always applies the same encryption to the same encryption key, there is an encryption 'pattern'. Below is an image that visually describes the ECB mode encryption. Since there is a pattern in the encryption in ECB mode, the image (center) encrypted in ECB mode retains the outline of the original image (left side). On the other hand, an image (right side) encrypted by a mechanism other than ECB mode is sufficiently encrypted so that the original image cannot be recognized. Citizen Labh explained that encryption in the ECB mode has a pattern, so it is possible to decipher the pattern by a replay attack or the like.

In addition, Citizen Lab noted that there is a vulnerability in Zoom's 'waiting room' feature. The waiting room feature allows the host to control who joins the meeting. For meetings with the Waiting Room feature enabled, users who join the meeting first enter the Waiting Room. Only after the host authorizes the user can the user join the meeting.
Citizen Lab claimed that it discovered that there was a security vulnerability in this waiting room function, and notified Zoom of the vulnerability. In addition, Citizen Lab wrote, 'To prevent abuse,' 'we will not publish the details of the vulnerability.' Citizen Lab encouraged users to 'don't use the waiting room feature, just password the meeting.'
Responding to security and privacy concerns, Zoom said in an official announcement , 'The government has not specifically created tools to assist law enforcement to spy on users, and it has been hidden from users. There is no way to intercept the content of the meeting. ' In addition, Zoom has not disclosed how much data government agencies have been required to disclose or how much they have actually responded to. However, in response to Access Now , an international non-profit organization on the public interest of the Internet, requesting to publish those data in an open letter , it promised to `` publish a transparency report within three months '' It was done.
Related Posts:
in Software, Web Service, Posted by darkhorse_log