A cyber attack striking a vulnerability present in all versions of Windows 2000 and later is ported to Metasploit

In April 2017, a hacker organization "Shadow Brokers" claimed that cyber attack tools developed by the National Security Agency (NSA) were stolen, and tools have been released several times since then. Security researchers transplanted some of the attacks into the penetration tool "Metasploit".
NSA Exploits Ported to Work on All Windows Versions Released Since Windows 2000
https://www.bleepingcomputer.com/news/security/nsa-exploits-ported-to-work-on-all-windows-versions-released-since-windows-2000/
A hacking tool that Shadow Brokers stole from the NSA has caused a situation where some malicious hacker has improved the hacking tool and a new kind of malware is created and exploited when it is released. Ransom ware of the ransom request type that was popular in 2017 "Wanna CryIt is regarded as its representative.
Cyber attack trend is malware that exploited NSA tools infected by over 500,000 PCs - GIGAZINE

The most popular for many cybercriminals is the NSA tool called EternalBlue. On the other hand NSA tools that are only valid for some Windows OSs and do not support the latest Windows were not so popular. This time, RiskSense security researcher Sean Dillon said that NSA tool "EternalChampion"EternalRomance"EternalSynergy"To the Metasploit framework and expanded the scope of the attack.
MS17-010 EternalSynergy / EternalRomance / EternalChampion aux + exploit modules by zerosum 0x0 · Pull Request # 9473 · rapid7 / metasploit-framework · GitHub
https://github.com/rapid7/metasploit-framework/pull/9473
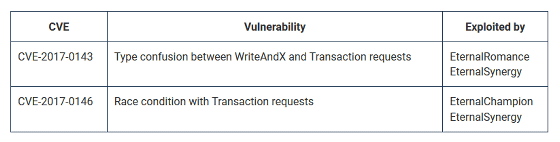
Dillon added the vulnerability "CVE-2017-0143" "CVE-2017-0146". These vulnerabilities are "MS 17-010It is fixed with ", and it will not be damaged if it puts countermeasure patch.
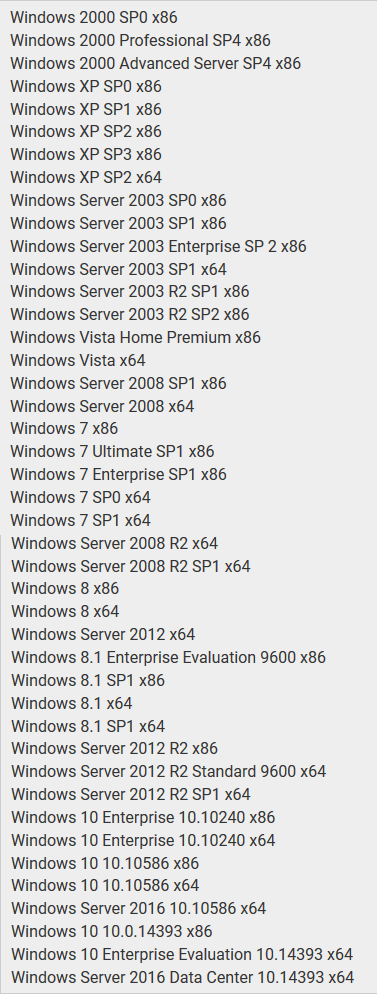
The target Windows is as follows. It is valid for all Windows OSs from Windows 2000 and later, regardless of 32 bits and 64 bits.
The effectiveness of the improved tool has already been verified by several security researchers.
exploit / windows / smb / ms17_010_psexec and auxiliary / admin / smb / ms17_010_command are now surely two of the most vigorously tested modules in all@ MetasploitThanks to everyone who helped! Should land to master branch soon ...pic.twitter.com/NKy8nopF9p
- zǝɹosum 0x0 (@ zerosum 0x0)February 2, 2018
Related Posts: