"Macro virus" targeted at Mac appeared, steal personal information using Word's automated macro

ByHome thods
"We wrested over ten years ago"Macro virusHowever, in 2017 years, Macro virus that aimed at Apple's macOS was discovered.
New Attack, Old Tricks
https://objective-see.com/blog/blog_0x17.html
Mac malware discovered in Microsoft Word document with auto-running macro
http://appleinsider.com/articles/17/02/09/mac-malware-discovered-in-microsoft-word-document-with-auto-running-macro
Develop Mac security tools "Objective-SeeFound that a Word file named "U.S. Allies and Rivals Digest Trump 's Victory - Carnegie Endowment for International Peace" tried to download malicious data using an automatically operating macro.
However, when opening a Word file, there are also an option to open or open a file with the macro enabled or disabled, and an option to not open it, so if you choose options such as "Do not open" or "Disable macro", it infects malware It is not.
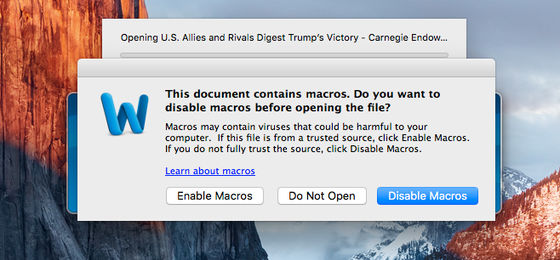
If you open a file with macros enabled, the Python script will be executed automatically and you will have two levels ofpayloaddownload. Then, before decrypting and running the payload, it is a network monitoring toolLittle SnitchIt seems to first check if it is running. The Python script itself is an open sourceEmPyreThe thing of the project is almost diverted as it is.

However, since it is currently inaccessible to the payload file that is downloaded when the macro is executed, it was unknown what kind of damage the Mac users were supposed to be caused by executing the macro. However, by analyzing the code of the EmPyre project, Objective - See is guessing what happened with the two - stage payload download.
According to Objective-See, the Mac will automatically reboot with a two-stage payload download and try to run multiple EmPyre modules. This "multiple EmPyre modules" contains various options for attackers to steal information from the Mac,Keylogger, Key chain dump, monitor clipboard, shoot screenshots, access to iMessage, access to webcams, and more.

ByMarkus Petritz
Security researcher Patrick Woodle, a software development company working at Synack, commented, "This malware is not particularly state-of-the-art." The reason is that "To open the Word file and still have the macro enabled" to infect it.
Virus that misuses macros in the first placeMacro virus"Itself is a relatively old attack method, and in the past such methods have become popular in some cases. As a representative example thereof, "MelissaThere are such things asViruses prevalent in 1999is. However, since these macro viruses have targeted so far not Mac but Windows, in that sense it may be said that it is new malware in that sense.
The word file containing malware is "MacDownloaderIt seems that it came to be seen at the same time as the malware that Iranian hacker seems to have created. This "MacDownloader" was created to attack the American defense industry and human rights defense members, it infects from fake Flash update displayed on a fake aerospace website. However, it is unknown whether the Word file containing malware was created by the same Iranian hacker as the MacDownloader producer.
Related Posts:
in Security, Posted by logu_ii