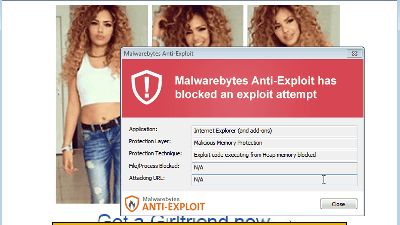
More than 110,000 people watching YouTube are infected with malware, the cause is "advertisement"
ByMBK (Marjie)
Advertisement that users are skipped to websites containing malicious code is oftenRageHowever, it turned out that this kind of advertisement was distributed on YouTube, and it was discovered that about 113,000 people were infected with malware in a month.
YouTube Ads Lead To Exploit Kits, Hit US Victims | Security Intelligence Blog | Trend Micro
http://blog.trendmicro.com/trendlabs-security-intelligence/youtube-ads-lead-to-exploit-kits-hit-us-victims/
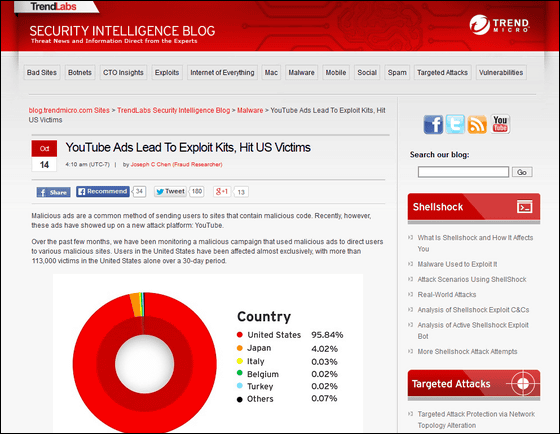
Internet security companiesTrend MicroHas been investigating malicious attacks, in the past few months, to skip users directly from malicious sites to ads. According to this survey, it is clear that about 113,000 users in the United States infected with malware from this malicious attack in 30 days.
This attack started by clicking on the advertisement displayed on YouTube, arrives at the site where malicious code is embedded via two websites, and exploits the vulnerability to infect the PC with malware Let me say that. According to Trend Micro, advertisements distributed on YouTube seem to have been seen by users more than 11 million times by being displayed in popular music video.
ByMBK (Marjie)
According to Trend Micro's survey, advertisements displayed on YouTube do not skip the user directly to malicious code embedded sites, but instead go through two advertisement sites to a malicious website I will. The server for redirecting from the site to other sites is in the Netherlands, and malicious code is embedded in the site which will eventually be opened, and it infects malware from here. In addition, it seems that there is a server in the United States on the website where malicious code is embedded.
An attacker who launched malicious advertisement seems to have used the Polish government's DNS information for reuse. At the moment we do not have detailed information on an attacker and it is known that an attacker succeeded in rewriting DNS information by adding a subdomain from its own server, but for other detailed methods It is still unknown now.
Also, what the attacker used to infect malware is called "Sweet Orange"Exploit kitThis is Java's "CVE-2013-2460", Internet Explorer's"CVE-2013-2551"When"CVE-2014-0322"," Flash "CVE-2014-0515"We exploit four vulnerabilities to attack security vulnerabilities. And the name of the malware that will eventually be infected by the user is "TROJ_KOVTER.SM". It invades the user's PC, sets the file to be inaccessible by arbitrarily encrypting the file or setting the password, and requests money for returning the data so that it can be normally accessedRansomwareIt is one of what is called "CryptoLockerIt seems to be a dangerous thing to launch an elaborate attack like ".
ByPierre Lecourt
However, patches for the vulnerability used by "Sweet Orange" are distributed by Microsoft in May of 2013, so users who are constantly updating the PC's system to the latest state infect this malware It would not have been, Trend Micro mentions.
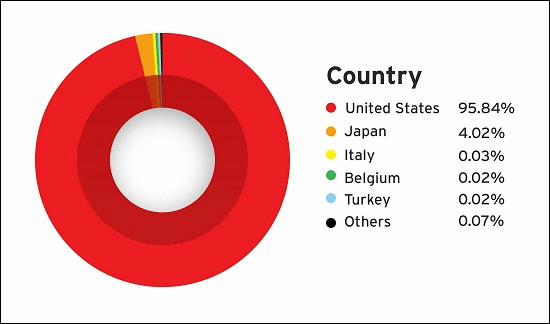
The percentage of users infected with malware due to the malicious advertisement found this time is as follows. Although most of them are US users, it can be said that many Japanese users are also being damaged.
Related Posts:
in Note, Posted by logu_ii