The attack tool "EternalBlue" that spreads Ransomware "Wanna Cry" diffuses smoothly

byLaurent Peignault
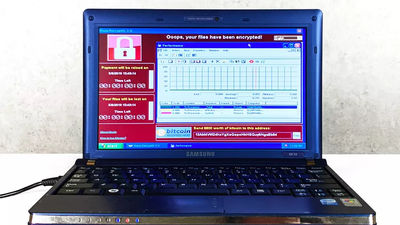
In May 2017,Ran smith wear "Wanna Cry" which requests ransom by encrypting the file of PC is a big fashion worldwideDid. One year since its violence, "Wanna Cry" ceased, but still there are a large number of computers with incomplete patches all over the world and it is a good target for Eternal Blue used for Wanna Cry spreading I will.
One Year After Wanna Cry, Eternal Blue Exploit Is Bigger Than Ever
https://www.bleepingcomputer.com/news/security/one-year-after-wannacry-eternalblue-exploit-is-bigger-than-ever/
One year ago, ESET products stopped Wanna Cry / Wanna Cryptor in its tracks: Here's an update | ESET
https://www.eset.com/us/about/newsroom/corporate-blog/one-year-ago-eset-products-stopped-wannacry-wannacryptor-in-its-tracks-heres-an-update/
EternalBlue was originally developed by the Cyber Department of the National Security Agency of the United States of America (NSA), and it is believed that most of it was stolen by hacker groups. Moreover, it has flowed out multiple times on the net,It is used for spreading of Ransomware "WannaCry", spreading virtual currency mining malware, etc..
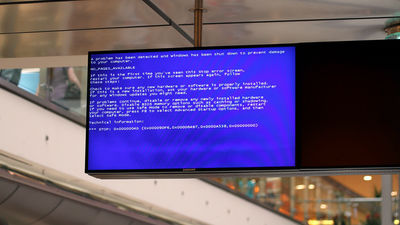
EternalBlue originally only works on Windows 7 and Windows Server 2008, so the damage was limited. OS is on Windows XPCrash on "Blue Screen of Death"Damage of WannaCry did not expand much because it was because of it.
However, after that, improvements were made to break vulnerabilities in Windows 8, Windows Server 2012, and Windows 10, and acquired the ability to infect many computers. Among the malware creators, it became a necessity of hacking.
One of the reasons why EternalBlue survived is that computers that do not properly patch vulnerabilities still exist in the world in millions and are connected to the network. Apparently, the threat of EternalBlue seems to continue for the time being.
Related Posts:
in Security, Posted by logc_nt