The existence of a large-scale DDoS attack carried out by making full use of security cameras all over the world revealed

We are developing security related products for the existence of botnet that will set up stronger DDoS attacks over the long term than traditional attacksSucuri SecurityI have found. The amazing thing about this botnet is that it is a security camera with over 25,000 units forming a network.
Large CCTV Botnet Leveraged in DDoS Attacks - Sucuri Blog
https://blog.sucuri.net/2016/06/large-cctv-botnet-leveraged-ddos-attacks.html
It is executed against the web serviceDDoSSucuri's security team investigating details of attacks and so on seems to have done security support for a small jewelry store's website which had been receiving external DDoS attacks for several days. Web site server was under attack under 35,000 HTTP requests per second, but by switching DNS to Sucuri Security one, we succeeded in mitigating DDoS attack immediately I heard he did.
Normally, the talk ends when it succeeds in blocking DDoS attacks, but the cybercriminals who launched attacks were a bit different than usual. After several hours since Sucuri's security team relaxed DDoS attacks, cybercriminals begin sending 50,000 HTTP requests per second to the website's server. This seems to extend for days, Sucuri 's security team says, "Such a long and powerful DDoS attack is not common."
Sucuri's security team has started a survey to find out the mechanism of this attack, as it has encountered a powerful DDoS attack that has never been seen before. As a result, the DDoS attack is a kind of IoT security cameraBotnetIt was discovered that it was done with.

ByNoel Reynolds
It seems this is not the first case of DDoS attacks using IoT devices, but Sucuri's security team has never encountered such a long-term powerful DDoS attack using a security camera only, . In order to analyze where the DDoS attack is being done, Sucuri's security team analyzed the location information of the IP address, and it turned out that the access was done everywhere in the world. Moreover, it seems that it has detected a total of 25,553 unique IP addresses with a few hours of attack.
The top 10 locations of the IP addresses of the security cameras used for the attack are as follows. About 24% is Taiwan, 12% is America, 9% is Indonesia, 8% is Mexico, 6% is Malaysia, 5% is Israel and Italy, 2% is Vietnam, France and Spain.
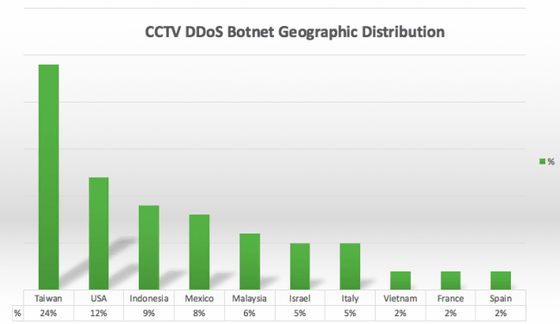
The top 10 locations of security cameras' IP addresses used for attacks accounted for 75% of the total, and the remaining 25% are dispersed in 95 countries and regions. In other words, it means that DDoS attacks using security cameras are being conducted all at once from 105 countries and regions.
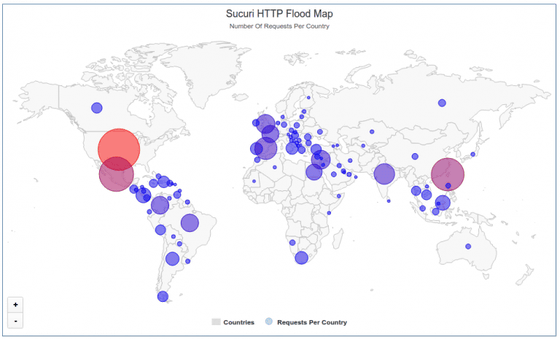
The IP address of the security camera used for the attack is mapped on the world map as follows. The country with a big circle means that there are security cameras used for many DDoS attacks, and you can see that there are small circles in Japan as well.
As we investigated the IP address, it became clear that the security cameras used for DDoS attacks are running on "Cross Web Server" and have a default HTTP page titled "DVR Components" I will. From this information, the Sucuri security team seems to have been able to guess that the IoT botnet used for the DDoS attack was a security camera.
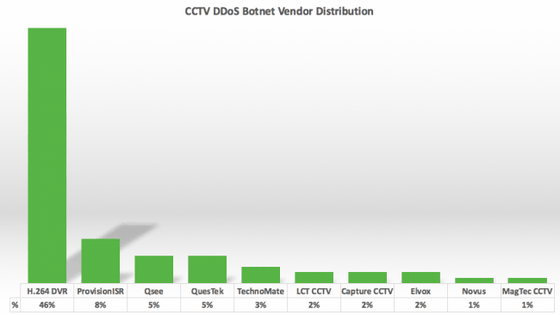
Furthermore, the analysis result of the manufacturer and reseller of the security camera used for the DDoS attack from the IP address is the graph below. The most frequent "H.264 DVR" seems to point to security cameras that do not input manufacturer makers etc as data with default.
DDoS attack is a type of cache bypass attack,Sucuri FirewallIt is possible to relax by using. Servers that can handle as many as 50,000 HTTP requests per second are usually very small, but Sucuri'sAnycastBy optimizing network and stack, the number can be easily relaxed. In addition, it seems that the security camera camouflaged the user agent to make it look like an access from the usual browser, and set an arbitrary referrer.
The most frequently used referrers are the following three.
http://engadget.search.aol.com/search?q=RANDOMKEYWORD
http://www.google.com/?q=RANDOMKEYWORD
http://www.usatoday.com/search/results?q=RANDOMKEYWORD
And the most frequently imitated user agents are the following three.
· Mozilla / 5.0 (Macintosh; Intel Mac OS X 10 _ 7 _ 4) AppleWebKit / 534.57.5 (KHTML, like Gecko) Version / 5.1.7 Safari / 534.57.4
· Mozilla / 5.0 (Windows NT 6.1) AppleWebKit / 536.5 (KHTML, like Gecko) Chrome / 19.0.1084.56 Safari / 536.5
· Mozilla / 4.0 (compatible; MSIE 7.0; Windows NT 5.1; SV 1; .NET CLR 2.0.50727)
In addition, it seems that 5% of the IP address used for the DDoS attack was an IPv6 address.
As a countermeasure against this large-scale DDoS attack, Sucuri's security team recommends "using Sucuri Firewall".
Related Posts:
in Security, Posted by logu_ii