"Plagiarism checker" which can judge whether the report is copy-paste Can compare multiple files such as desktop version, Word · PDF

Published in November 2013Copy-judgment site "Plagiarism checker"If you put a sentence on the input form on the site, it will search and check if it is copypee. The desktop version was released, but here is a function that allows you to read Word documents and PDF files and compare them.
【FREE】 Desktop version Plagiarism checker: Check the presence or absence of Copy on file basis
http://plagiarism.strud.net/desktop.html

In order to use the desktop version, first click on the link "this page" in the "Download" section in the middle of the page ... ...
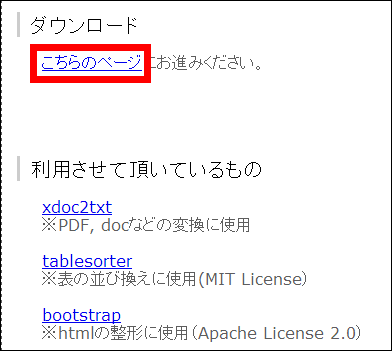
Download either "HC_desktop.lzh" or "HC_desktop.zip" on the download page. The contents are the same.
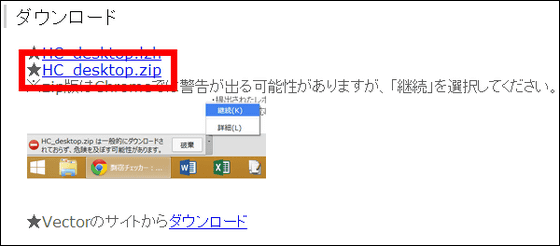
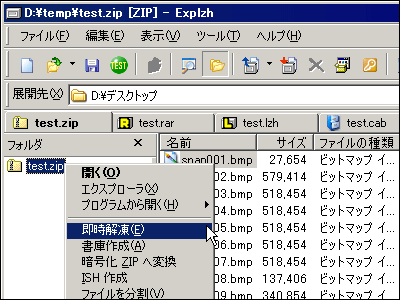
Download the downloaded fileExplzhExtract with software such as.

The contents of the folder look like this. "Hyousetsu Checker.exeIt's the main body so let's start it ....
Since the notice screen is displayed, click "execution mode".
First of all, let's check whether it is plagiarism using a web search about a single file. The paper used for checking is a paper by Mr. Tetsushi Nakamoto(PDF file)Bit coin: P2P electronic money system"is.

In the second half of the paper "11. Calculation", the following text is available.
Consider a scenario where an attacker tries to create a fake chain at a faster speed than a legitimate chain. Even if you succeed it,
You will not be able to manipulate the system freely, such as creating an inn from scratch or stealing coins that have not been owned by the attacker himself
Yes. The node also refuses payment with invalid transactions and blocks containing invalid transactions. An attacker can write his own transaction record
It is only to try to recover the recently paid amount by switching.
We insert several reading points here and change the polyphonic words to polite words and prepare them as samples and save them in a text file.
Consider a scenario where an attacker tries to create a fake chain at a faster speed than a legitimate chain.
Even if you succeed in it, you will not be able to manipulate the system freely, such as creating coins from scratch or stealing coins that have not been owned by attackers themselves.
This is because the node rejects payments using invalid transactions as well as blocks containing invalid transactions.
The only thing that an attacker can do is rewrite your own transaction record, trying to recover the recently paid amount.
To check plagiarism, click "Open file" ... ...
Select the file you want to check, in this case "New text document", click "Open".
After confirming that the file is added to the list, set the mode field to "Search the Web" and click "Execute".
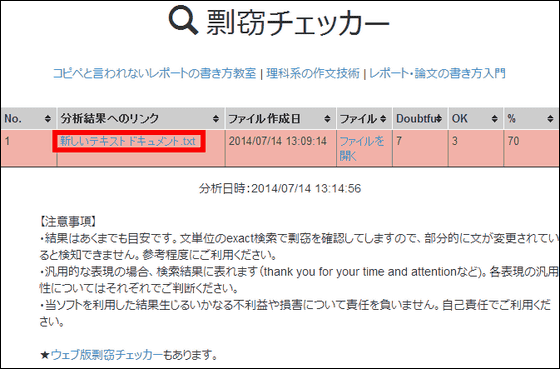
When the check is over, the results are displayed on the browser like this. In this case, the match rate is as high as 70%, and the background of the frame is red due to plagiarism. To see detailed analysis results click on the file name in the "link to analysis result" column.
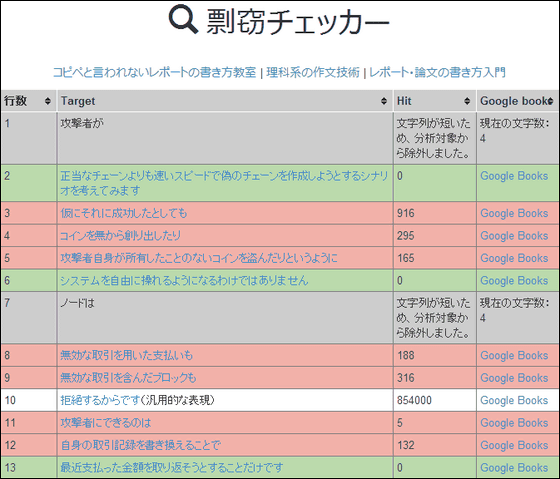
Then you can see the result of checking whether each line is plagiarism or not. Two rows of "an attacker" and "node" are too short to be excluded from the target, and one line is omitted as a generic expression. Of the remaining 10 lines, 3 lines did not hit the search because they changed their endings, but it was judged as plagiarism because the rest hit.
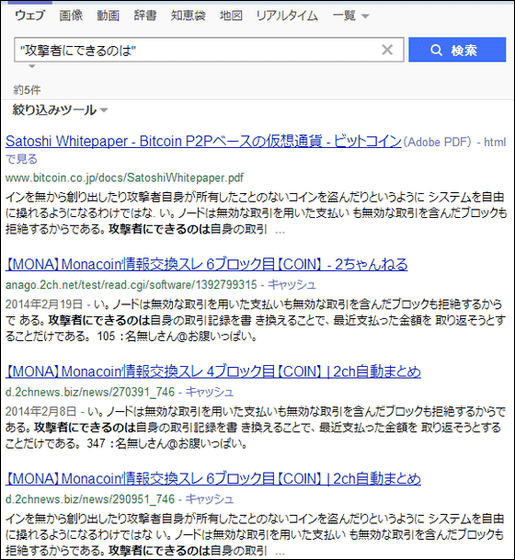
Specifically, looking at the search result of the phrase "the attacker can do for him" who had few hits, the original paper was displayed in the first case, and the other results were also quoted from this paper did.
Similarly, "File comparison" checking whether copying has been done with multiple files is a unique feature of the desktop version. By selecting multiple files in this way, selecting the "compare between files" mode, selecting the character code of the file and clicking "execute" ...
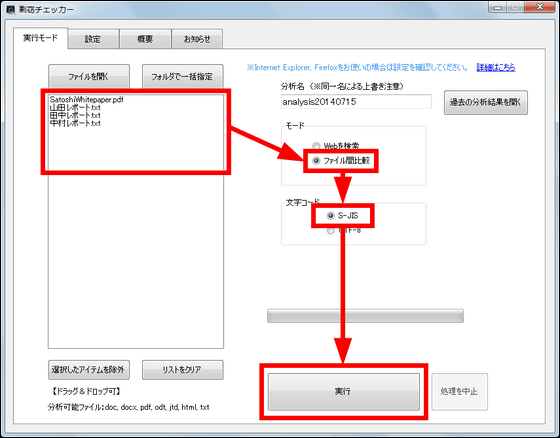
It searches for overlapping parts in each file. This time, three people issued a report that copied the "overview" part of the paper by three people.
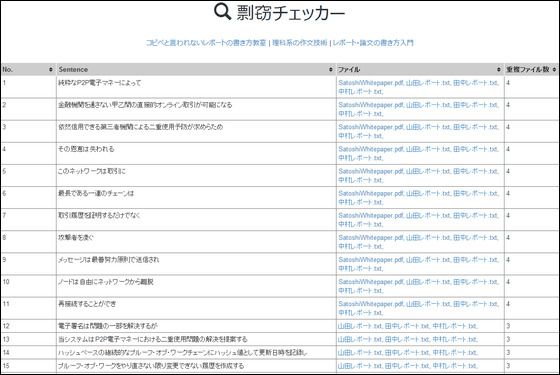
If the position of the reading point is changed or the ending point is changed to be interpreted as a different sentence from the original, the overlap becomes 0. Misuse us is strictly prohibited.
By the way the setting items are like this.
Files that can be analyzed in desktop version are Word document (.doc ·. Docx), PDF file (.pdf), OpenDocument text (.odt), Ichitaro document (.jtd), HTML file (.html), text file (. TXT). It is included in the checkerXdoc2txtSince it extracts the text part, it is possible to check even if you do not have the source software such as Word or Ichitaro installed.
Related Posts: