What is the danger posed by the "second OS" hidden in all smartphones?

ByJon Fingas
The OS (operating system) which is the key to the operation of the smartphone is the OS for iOS, Android, Windows 8, BlackBerry OS and PDAPalm OSthere is ........., ........., etc. There is a hidden "second OS" in such OS, and there is a fear that a smartphone may be operated from a malicious personOSNewsWe are calling attention.
The second operating system hiding in every mobile phone
http://www.osnews.com/story/27416/The_second_operating_system_hiding_in_every_mobile_phone
According to OSNews, in addition to iOS and other operation systems, all smartphones and other devices with mobile communication functions in the communication band such as 3G or LTE are equipped with RTOSReal time operation system) Is built in, and it is said that it is practically executed by two OSs.
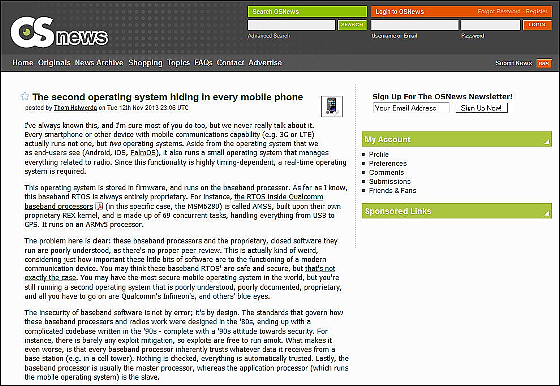
The RTOS is stored in the firmware and runs on the baseband processor. For example, it is used for Apple productsQualcommRTOS inside the baseband processor ofAMSSWhat is called. One problem with this RTOS is that most RTOS are exclusive brand equipment.

ByLinux Tag
The baseband processor standard was designed in the 1980's, and in the 1990's a complicated code base was completed. After that, the baseband processor is used as a second OS for almost all mobile devices without proper mutual evaluation and sufficient understanding in the closed state of monopolistic brand.
ByJames Cridland
The baseband processor can be dangerous because it automatically and unconditionally receives all data received from the mobile base station etc. Normally, the baseband processor is treated as a "master processor" and the "application processor" running the mobile OS automatically also automatically trusts data from all base stations. Therefore, all smartphones have a second OS that runs on the ARM processor.

ByMorton Lin
University of LuxembourgSecurity researcher Ralph Philippe Weinmann conducted a retrograde analysis of Qualcomm and Infineon's baseband processor software and found that an attacker could execute code remotely. According to this discovery,Hayes command set(Command language for modem designed in 1981), you can attach smartphone's auto answer function to users without knowing it.

ByValerie
Also, the mobile base station is managed by the main career of the country and it is safe to some extent. However, as a fact, the price of the base station continues to decline, sometimes sold on eBay, and there are also base stations that are made from open source. By targeting such a base station it is also possible to activate microphones, cameras and send messages such as phone and SMS.

ByMonkeyc.net
Baseband processors are faced with many problems, but at the moment there are only a few people who are aware of them better or worse. In the baseband implementation,GSMWriting one would be horribly long,UMTS,HSDPAYou need to add. Although it is extremely difficult to solve the problem of the baseband processor, OSNews concludes that mobile phone companies are about to develop secure baseband processors and related software.
Related Posts:
in Mobile, Posted by darkhorse_log







