A backdoor that allows voyeurism and eavesdropping is discovered in a smartwatch for children made in China

We found a
Exposing covert surveillance backdoors in children's smartwatches | mnemonic
https://www.mnemonic.no/blog/exposing-backdoor-consumer-products
Undocumented backdoor that covertly takes snapshots found in kids' smartwatch | Ars Technica
https://arstechnica.com/information-technology/2020/10/a-watch-designed-exclusively-for-kids-has-an-undocumented-spying-backdoor/
Xplora X4 is a smartwatch that supports 4G, 3G, and 2G connections and can operate independently with Android. In addition to taking pictures with a 2-megapixel camera and making voice and video calls, it also has a location information sharing function for parents to watch over their children because it supports GPS.
X4 – Xplora
https://myxplora.co.uk/products/xplora-4
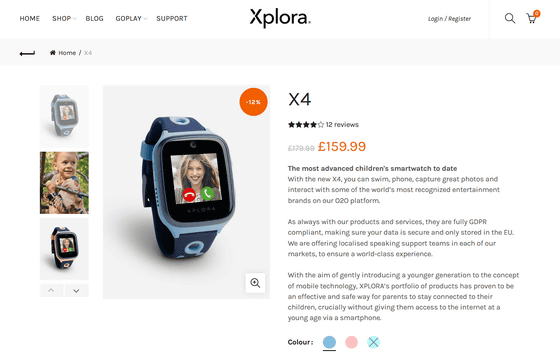
In this Xplora X4, we found a backdoor that can forcibly acquire real-time location information, photos, sounds, etc. from a remote location. According to Harrison Sand and Erlend Leiknes of Norwegian security firm mnemonic, Xplore X4 is activated by sending an encrypted text message, 'REMOTE_SNAPSHOT (remote snapshot)' and 'SEND_SMS_LOCATION (send location by SMS)'. ) ”Can be executed. Sand et al. Reported that by running 'REMOTE_SNAPSHOT', they confirmed that the photo was taken immediately and automatically sent to Xplora's server while the display was off.
A study by Sand et al. Found that Xplora X4 has a number of applications installed by Chinese security company Qihoo 360. In addition, Qihoo 360 sells smartwatches with almost the same functions as Xplora X4 for the domestic market, and it turned out that the company name of 'Qihoo 360' is left as it is in the terms of use of Xplora. It was.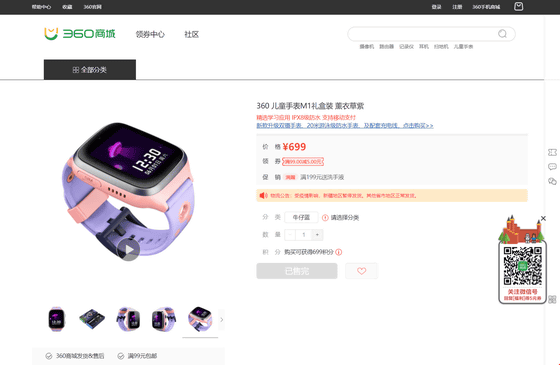
From this, Sand et al. Believe that the Xplora X4 in question was developed and manufactured by Qihoo 360 in China, and that Xplora is responsible for sales outside China. Qihoo 360 is a company that was added to the United States Department of Commerce's export sanctions list in June 2020 because it 'contrary to US security interests.'
According to Sand, the phone number assigned to the Xplora X4 and the per-device encryption key are required to execute commands from the backdoor. An Xplora spokeswoman said, 'At least the phone number cannot be known by Xplora.' 'Even if an attacker pokes the backdoor in question and forcibly takes a picture, the data will be accessible to a third party. In addition to being saved on the AWS server that cannot be done, all logs are saved when an employee accesses the server. ' Regarding the existence of the backdoor in question, he said, 'It is a remnant of the remote photography function that was planned to be implemented in the'SOS emergency button'for children, and it was not completely removed from the firmware.'
Related Posts: