It turns out that a hacker impersonated a PHP developer and put a backdoor in the source code

It turns out that someone broke into
php.internals: Changes to Git commit workflow
https://news-web.php.net/php.internals/113838
PHP's Git server hacked to add backdoors to PHP source code
https://www.bleepingcomputer.com/news/security/phps-git-server-hacked-to-add-backdoors-to-php-source-code/
Hackers backdoor PHP source code after internal repo hack | The Record by Recorded Future
https://therecord.media/hackers-backdoor-php-source-code-after-internal-repo-hack/
Hackers backdoor PHP source code after breaching internal git server | Ars Technica
https://arstechnica.com/gadgets/2021/03/hackers-backdoor-php-source-code-after-breaching-internal-git-server/
Nikita Popov, one of the developers of PHP, announced on March 28, 2021 that malicious source code had been inserted into PHP. In it, Popov said, 'Yesterday, under the names of Ladov and I, two malicious commits were pushed to the Git repository in php-src . I'm investigating what exactly happened, but all Evidence shows that there was an intrusion into the git.php.net server. '
Actually, the exchange when malicious code is found in the PHP repository is as follows. The source code has been modified by Mr. Radov under the guise of correcting a typo, but Mr. Radov is not involved.
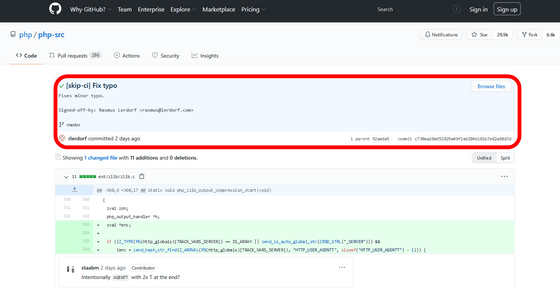
The existence of the backdoor was
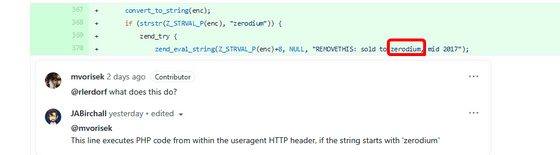
Zerodium is the name of an American information security company that buys vulnerabilities from hackers and security researchers. Zerodium CEO Chaouki Bekrar said on Twitter: 'Obviously we have nothing to do with this one. Perhaps someone found a bug or exploit and tried to sell it, but who? I didn't even try to buy it, so I guess I was angry. '
Cheers to the troll who put 'Zerodium' in today's PHP git compromised commits. Obviously, we have nothing to do with this.
— Chaouki Bekrar (@cBekrar) March 29, 2021
Likely, the researcher (s) who found this bug / exploit tried to sell it to many entities but none wanted to buy this crap, so they burned it for fun ????
Following the security breach, the PHP development team decided that the internal Git server was no longer reliable and decided to transfer source code control to GitHub. This will push future PHP changes directly to GitHub.
Popov told Bleeping Computer, an IT news site, 'I'm checking the repository to see if there are any modifications other than the two commits that the problem was found this time,' and the impact of this unauthorized access. He expressed his intention to continue the investigation on.
In addition, it is said that this problem was found on the development branch of PHP 8.1 scheduled to be released at the end of 2021. The Record by Recorded Future from overseas media said, ' Statistics surveys show that PHP is used by about 80% of all websites on the Internet, but most PHP servers patch and run the latest software versions. It is probable that this incident affected only a small number of systems because of the delay, 'he said, saying that the extent of the impact would be minimal.
Related Posts: