Freecraft "PDFCrack" which can analyze passwords of PDF files on a global basis even on Windows
I added a password to the PDF file for security, but I do not know what the password was, so it's okay even if I'm at a loss. By using this free software "PDFCrack" you can analyze and correct the correct password by using a dictionary file or by trying password all at once from one end. It is very useful as it is possible to restrict the type of characters and the number of characters, interrupt it halfway and let it continue. The passwords that can be analyzed are owner passwords (passwords that are used for printing / modifying contents and extracting contents as so-called editing authority) and user passwords (passwords for browsing, passwords asked for opening when asked to open) ), And benchmarking is also possible.
Originally it is open source software for Linux, but volunteers also offer versions that run on Windows.
So, this time I tried breaking the password of the PDF file by actually using the version that works on Windows. The procedure is as follows.
PDFCrack
http://pdfcrack.sourceforge.net/
PDFCrack - A Password Recovery Tool for PDF-files (Windows version)
http://blog.rubypdf.com/pdfcrack/
First, download the ZIP file from the above site
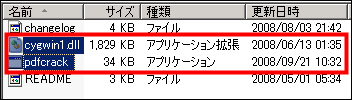
The body necessary for the operation of these two types of files "pdfcrack.exe" and "cygwin1.dll" in the decompressed file. Let's keep it in the same place. This time I decided to copy it directly under D drive.
Next, start the command prompt
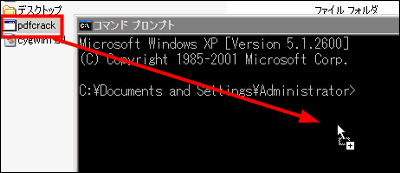
Drag and drop "pdfcrack.exe"
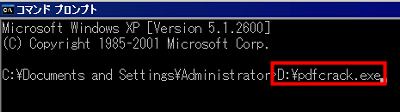
Then it will be input in this way. Next, press the space key once to enter a space.
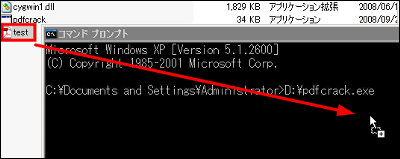
Then drag and drop the PDF file you want to analyze.
Then it becomes like this.
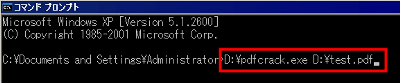
After that, if you press the enter key, it will start analyzing brute force of the user password.
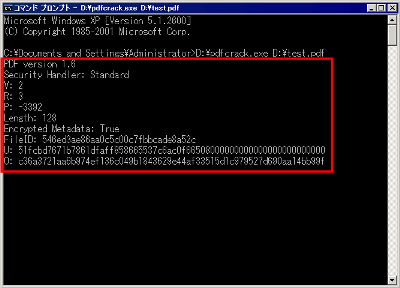
During the analysis, progress is displayed in this way at regular time intervals.
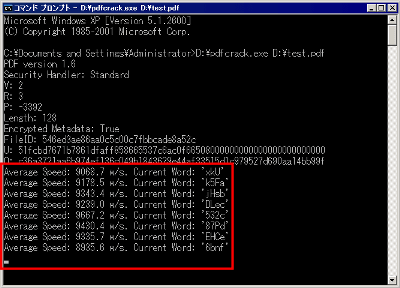
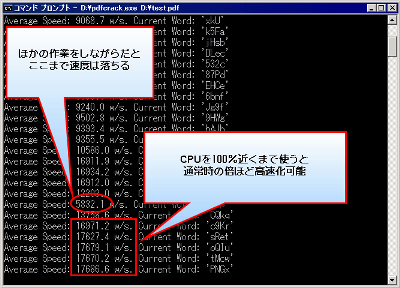
Since analysis is totally proportional to CPU speed, in order to analyze it as quickly as possible, it is effective to terminate other extra software or to raise the priority of CPU with Task Manager.
Therefore, there is a benchmark mode that measures how fast the CPU can analyze. After entering the location of pdfcrack.exe and the name of the PDF file to be analyzed, enter "--bench" and start the measurement.
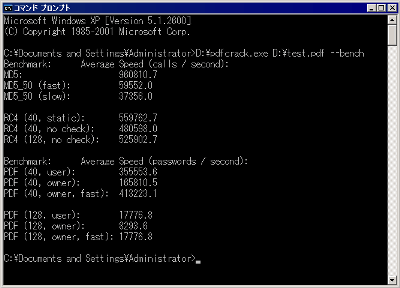
Also, by pressing "Ctrl + C" key during analysis, it can be interrupted and saved as "savedstate.sav". In this case it was saved in "C: \ Documents and Settings \ Administrator".
This is the file that saved its progress.

To start from the continuation, start the measurement by entering the location of pdfcrack.exe, the PDF file name to be analyzed and entering "--loadState =" full path of savedstate.sav "" and running it. This is also easy and easy to drag and drop.
If it is started from a continuation of continuation, such a character string will be displayed at the start of analysis. With this, even if there is only one PC, it is possible to concentrate and analyze only in idle time.
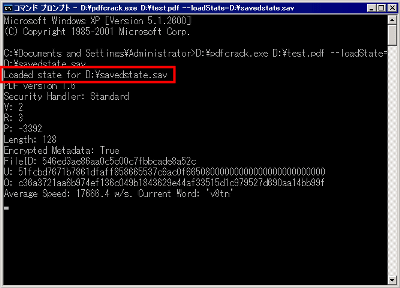
When you find the password it will be displayed like this. By default it will find user passwords.
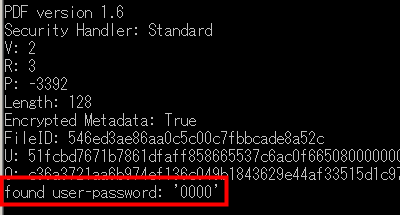
After finding the user password, if you enter the location of pdfcrack.exe and the name of the PDF file to be analyzed and enter "- password =" user password "" and execute it, the speeding up is done and the owner password is also sent at a tremendous speed It will be possible to discover.
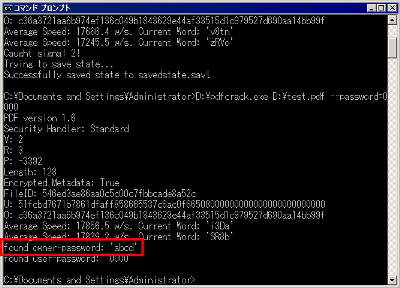
The various commands look like this
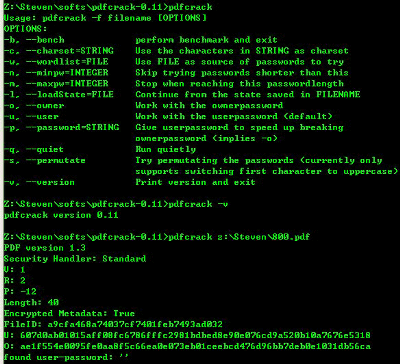
- bench: Benchmark mode
--charset = STRING: By replacing the part of STRING with the character type you want to use, we will perform brute force using only that character type. With "--charset = 0123456789", you will use various numbers from 0 to 9.
--- wordlist = FILE: If you set the FILE part to the full path of the dictionary file, we will make a brute-fight with the words in the dictionary file. Dictionary files are easier if you use it because you are rolling if you look for the net. It is the fastest if it is a combination of frequently used words.
- minpw = INTEGR: If you set the INTEGR part as a number, we skip the combinations below that number of characters. For example, if you know that it is not 4 digits or less, "- minpw = 4" makes it possible to hit the brute force from a combination of five letters.
- maxpw = INTEGR: If INTEGR part is a number, brute force will stop when it reaches that number of characters. For example, to stop analysis at the 12th digit, "--maxpw = 12" is enough.
--loadState = FILE: Start parsing from the continuation using savedstate.sav which is generated when interrupted by Ctrl + C during parsing.
--owner: By default, we will search for user passwords by brute force, but if you specify this we will look for owner password by brute force.
- user: Search user password by brute force.
--password = STRING: By setting the part of STRING to the user password, it becomes possible to dramatically shorten the time to find the owner password.
--quiet: Analyze without displaying progress
--permutate: Convert the first initial letter to uppercase letters when using a dictionary file
--version: Version display
This is perfect if distributed cooperative analysis using multiple PCs between networks, in short, P2P type analysis can be done, but it seems that there is no function so far. However, I felt it was enough to withstand practical use for normal purpose.
Related Posts: