The hacker food chain, where security companies acquire backdoors installed in hacking tools used to install backdoors

Security company watchTowr has identified a backdoor installed in a hacking tool designed to install a backdoor, and revealed that it is collecting and analyzing data within the bounds of the law.
Backdooring Your Backdoors - Another $20 Domain, More Governments
https://labs.watchtowr.com/more-governments-backdoors-in-your-backdoors/

When hackers succeed in breaking into someone else's server by some means, they often install a backdoor to make it easier to use the server in the future. Various
web shells have been developed as tools for installing backdoors, but according to watchTowr, many web shells have backdoors in the web shell itself.
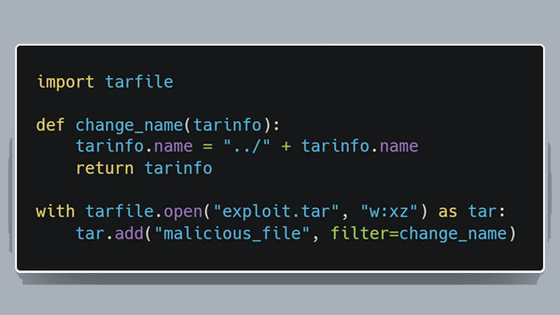
For example, the image below is a web shell called 'r57shell'. r57shell has a mechanism that sends information about itself to rst.void.ru when r57shell is newly installed, so if a hacker goes to the trouble of breaking into a target server and installing r57shell, the administrator of rst.void.ru can use r57shell on that server. In other words, as long as hackers use r57shell, the administrator of rst.void.ru can easily use backdoors on various servers.
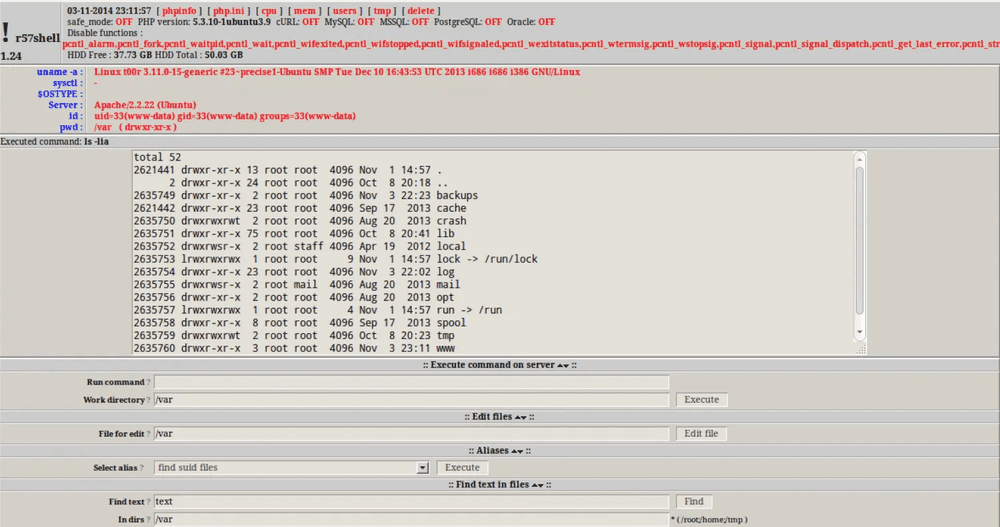
Below is another web shell called 'C99Shell'. Many web shells have a password protection function, so even if the address where the web shell is installed is leaked, if the password is not leaked, others will not be able to use the backdoor. However, C99Shell's password authentication probably intentionally uses vulnerable code, making it possible for not only the hacker who installed C99Shell but also others, such as the creator of C99Shell, to bypass the password authentication.
watchTowr investigated various web shells and identified the domains that were issuing instructions to each web shell. Since more than 40 of the domains were no longer in use, watchTowr acquired the domains and recorded and analyzed their logs. As a result of the analysis, it was stated that backdoors were installed in more than 4,000 servers, three of which were in
the High Court of the Federal Republic of Nigeria .
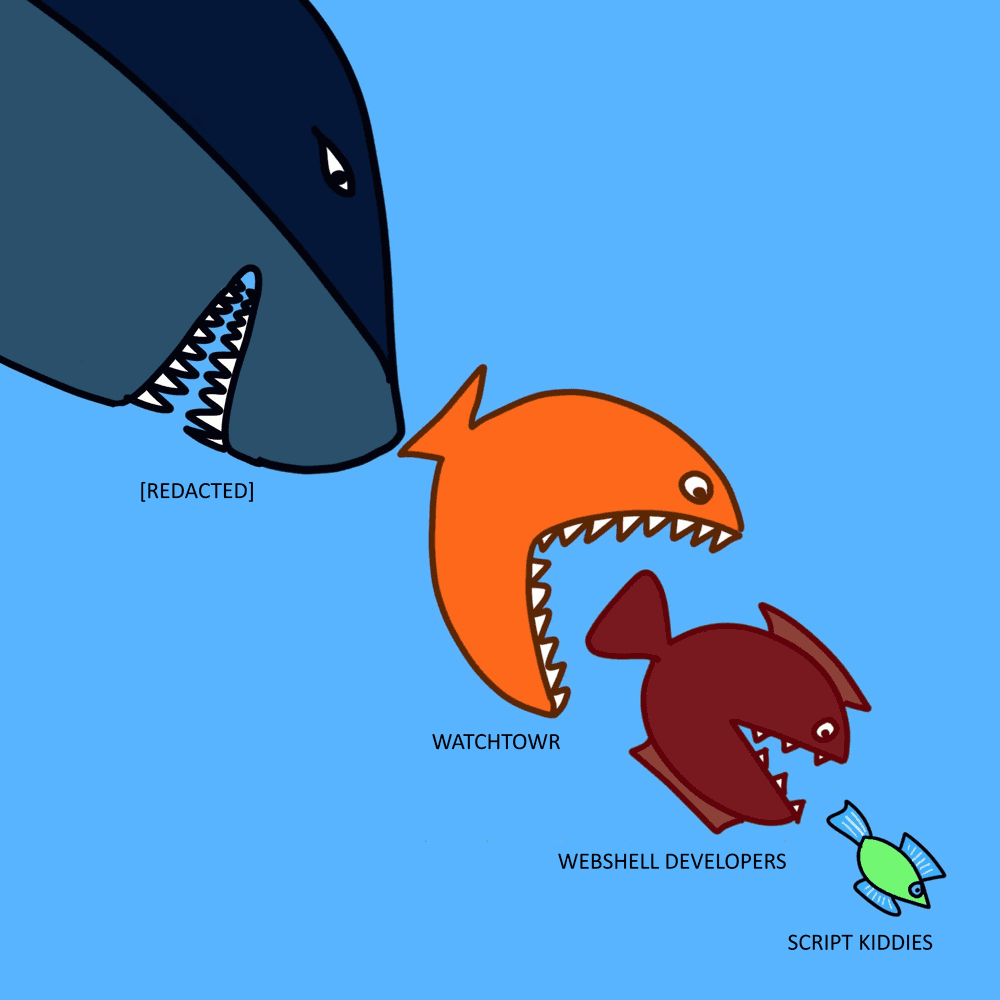
The watchTowr blog also has the following diagram as an illustration. You can see how script kiddies install backdoors to use other people's servers, web shell developers install backdoors in web shells to use other people's backdoors, and the security company watchTowr uses the backdoors in web shells. There is a food chain for hackers too.
Related Posts: