A 15-year overlooked vulnerability in Python could affect more than 300,000 open source repositories
A bug in the programming language Python has been rediscovered that was made public in 2007 but never fixed. The impact of this bug, which also leads to arbitrary code execution vulnerabilities, has spread to various projects through coding automation tools, and it has been pointed out that there are more than 350,000 open source repositories to fix.
Tarfile: Exploiting the World With a 15-Year-Old Vulnerability
Tarfile: Exploiting the World With a 15-Year-Old Vulnerability
https://www.trellix.com/en-us/about/newsroom/stories/threat-labs/tarfile-exploiting-the-world.html
The bug in question has been tagged as CVE-2007-4559 and is described as a vulnerability in Python's tarfile module.
The tarfile module is for reading and writing tar format archives containing different files and metadata. Metadata contained in a tar format archive includes various information such as file name, file size, checksum, file owner information, etc., and is represented by the Tarinfo class.
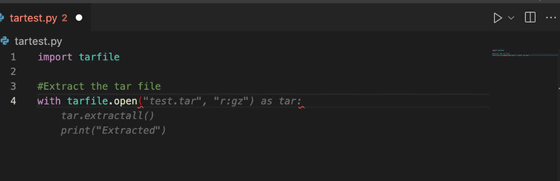
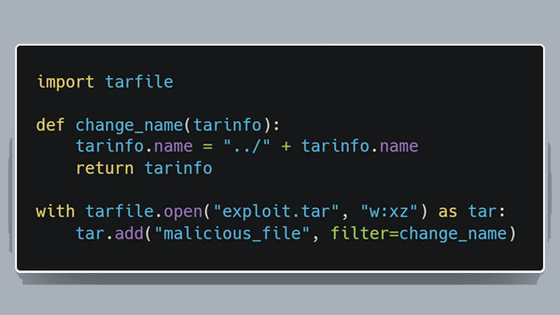
And the tarfile.extract() and tarfile.extractall() functions explicitly rely on the information in the Tarinfo object and combine the path passed to the function with the file name in the Tarinfo object. It is said that this is a vulnerability that allows attackers to perform directory traversal . In other words, a malicious person can access the file system and execute arbitrary code.
This CVE-2007-4559 was reported in August 2007 on the Python development mailing list. However, this vulnerability has never been patched, only warning of the risk in official documentation.
In 2022, the Advanced Research Center at Trellix , an integrated company of security companies McAfee and FireEye , rediscovered CVE-2007-4559 during an investigation into an unrelated vulnerability. Trellix has published a demonstration on YouTube of actually exploiting CVE-2007-4559 in a Windows environment.
Spyder IDE Demo Video-YouTube
Also, the following movie is executed in the Linux environment.
Polemarch Demo Video-YouTube
Trellix researchers scraped 257 repositories likely to be affected by CVE-2007-4559, of which 175 were manually checked and confirmed, 61% of which were tarfile.extract() Or found to contain vulnerable code by tarfile.extractall(). We also checked all the remaining repositories and found that 65% of them contained vulnerable code.
According to Trellix, more than 350,000 repositories are believed to be threatened by this vulnerability, many of which use automated tools such as GitHub Copilot . Automated tools do everything automatically, so they are learning from code in different repositories. If the repository you're learning from contains vulnerable code, it can increase your project's security risk without your knowledge.
Trellix has already created a patch for more than 11,000 projects and is preparing to create a pull request. Researchers expect more than 70,000 projects to be fixed in the coming weeks, but it's unlikely that all projects will be fully fixed, as merge requests must be accepted by maintainers before they can be fixed. I'm trying to deaf
Related Posts:
in Web Service, Video, Security, Posted by log1i_yk