``Security verification code'' charged with malware is found in many GitHub repositories, one in ten malicious repositories

At GitHub, the world's largest code hosting platform, `` proof of
[2210.08374] How security professionals are being attacked: A study of malicious CVE proof of concept exploits in GitHub
https://doi.org/10.48550/arXiv.2210.08374
Thousands of GitHub repositories deliver fake PoC exploits with malware
https://www.bleepingcomputer.com/news/security/thousands-of-github-repositories-deliver-fake-poc-exploits-with-malware/
A research team at the Leiden Institute of Advanced Computer Science in the Netherlands reported that malware was included in a whopping 10.3% of PoC exploits distributed on GitHub in a paper published on the preprint server arXiv. did.
In this study, we investigated 47,313 PoC exploits published between 2017 and 2021 using three techniques. The three methods are 'IP address analysis' that checks the publisher IP that posted the PoC exploit against the public block list, etc., 'binary analysis' that checks the executable file and its hash with VirusTotal , and decodes the obfuscated file. and look up 'Hex and Base64 Parsing'.
The investigation found that 4893 of the 47,313 PoC exploits targeted were malicious repositories. Specifically, of the 358,277 IP addresses analyzed, 150,734 were unique IP addresses, i.e. addresses that were only used once, and 2,864 of them were blacklisted. It was said that it was. In addition, 1522 cases were classified as malicious by VirusTotal, and 1069 cases were registered in AbuseIPDB , a database that posts problematic IP addresses.
Below is a list of blocklists used for checking and the number of matches.
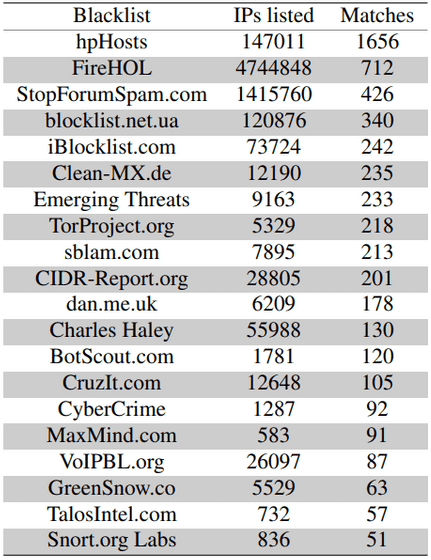
Binary analysis analyzed 6160 executables and identified 2164 malicious samples hosted in 1398 repositories. Most of them were about vulnerabilities found in 2020. The research also found
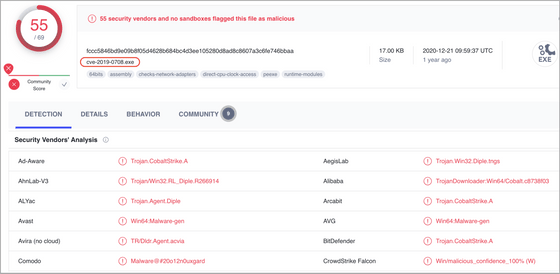
From this point of view, the research team asked people who use GitHub to ``read carefully the code you are trying to run on your own or your customer's network'' and ``if the code is obfuscated and it takes time to analyze it. is a repository whose content has not been verified for safety by taking measures such as putting it in a sandbox environment and checking the network for suspicious traffic, and using a tool like VirusTotal to analyze the binary. I called on you not to blindly trust the
Related Posts:
in Security, Posted by log1l_ks






