SQL injection vulnerability in PostgreSQL went undiscovered for over nine years and was used to break into the US Treasury Department

On December 30, 2024, a 'Chinese government-sponsored advanced persistent threat actor'
breached a system managing confidential data for the U.S. Treasury Department
. It was discovered that the intrusion used a SQL injection vulnerability that had existed in PostgreSQL for more than nine years but had gone unnoticed, as software engineer Nick Agliano wrote in an article.Hidden Messages in Emojis and Hacking the US Treasury
https://slamdunksoftware.substack.com/p/hidden-messages-in-emojis-and-hacking
SQL injection
is a well-known attack method that appears at the beginning of many security textbooks. SQL injection allows an attacker to rewrite SQL statements, which can have a significant impact on a system.Despite the fact that SQL injection is a well-known and highly impactful attack and is therefore highly guarded against, it is 'absolutely surprising' that a vulnerability allowing SQL injection had been lurking in PostgreSQL, a large open source project that is closely watched by many developers, for about 10 years.
SQL injection occurs when user-supplied input is not escaped properly when it is inserted into an SQL statement. Since single quotes (') are used to delimit string literals, proper handling is important in preventing attacks.
The compromised US Treasury Department system used PHP's
pg_escape_string method
to sanitize user input into a safe form. pg_escape_string internally calls PQescapeStringInternal, which actually performs the escaping process, and PQescapeStringInternal uses the pg_utf_mblen function to check the length of multibyte Unicode characters during the escaping process.In this attack, the character code used was 'C027' in hexadecimal and '11000000 00100111' in binary. This character is determined to be a '2-byte character' according to the specifications of multi-byte Unicode characters because the first three bits are '110'. After that, when the remaining bits representing the character are read, the character code is '27' in hexadecimal, and since '27' is the character code representing a single quote, a single quote was inserted and the SQL injection was successful.
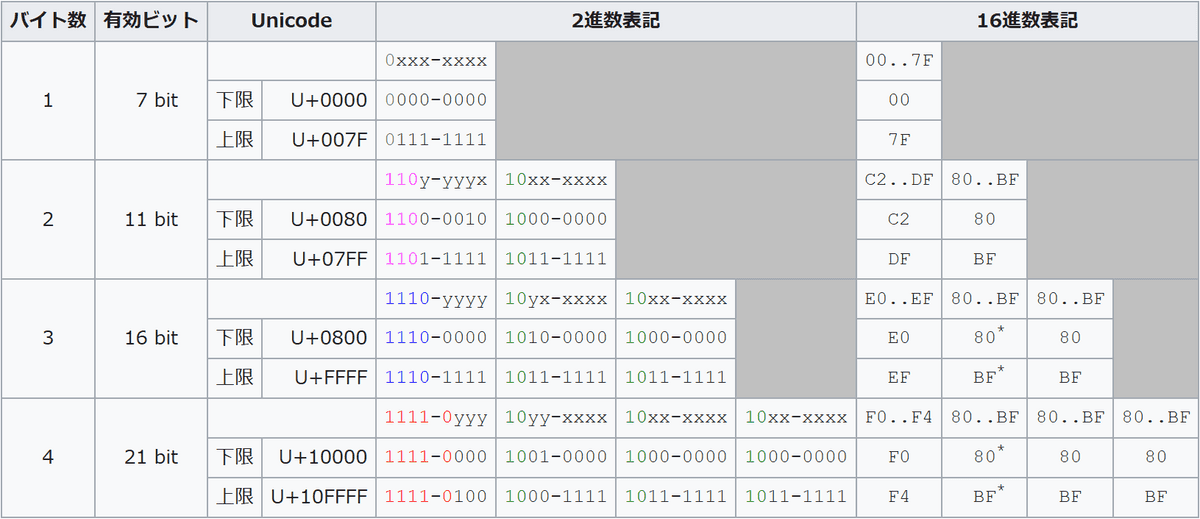
Although a plain ''' is escaped, adding a bit to the beginning to make it a two-byte character makes it possible to skip the escape process.
The SQL injection allowed the attacker to freely use psql, an interactive interface that comes with PostgreSQL, and to not only access the database but also enter arbitrary system commands via psql.
This vulnerability was
fixed on February 11, 2025
.Related Posts:







