Toyota admits data leak after attack by ransomware group Medusa

Toyota confirms breach after Medusa ransomware threatens to leak data
https://www.bleepingcomputer.com/news/security/toyota-confirms-breach-after-medusa-ransomware-threatens-to-leak-data/
Toyota recovering from cyberattack on its financial services division
https://therecord.media/toyota-cyberattack-financial-services-divison
Medusa ransomware gang claims data breach of Toyota Financial Services in Germany - Cyber Daily
https://www.cyberdaily.au/security/9832-medusa-ransomware-gang-claims-data-breach-of-toyota-financial-services-in-germany
Toyota Financial Services is a global company that provides financial services in 90% of the markets where Toyota sells cars.
In the early morning hours of November 16, 2023 local time, the ransomware group Medusa updated the list of victims of the group's cyber attacks on the dark web and added Toyota Financial Services. Medusa is holding data stolen from Toyota Financial Services hostage and demanding a ransom of $8 million (about 1.2 billion yen). Medusa has set up a 10-day ransom payment period for Toyota Financial Services, and also offers an option to extend the payment deadline by one day for $10,000 (approximately 1.5 million yen).
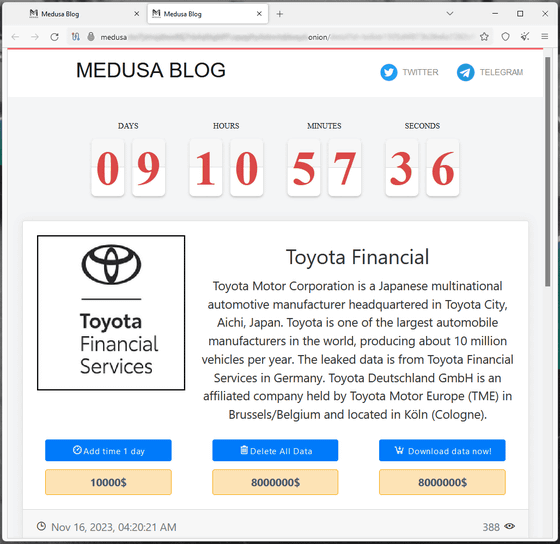
To prove that it stole data from Toyota Financial Services, Medusa used the company's financial documents, spreadsheets, purchase invoices, hashed account passwords, clear-text user IDs and passwords, contracts, and passports. We publish sample data such as scans, internal organization charts, financial performance reports, and employee email addresses. Medusa also released a text file containing the file tree structure of data stolen from Toyota Financial Services.
The majority of the documents released are in German, indicating that the hackers gained access to systems that service Toyota's operations in Central Europe.
When security media Bleeping Computer asked Toyota for comment on the ransomware attack, a spokesperson said, ``Toyota Financial Services Europe and Africa recently confirmed unauthorized access to systems at a limited number of locations. is investigating this fraud, taking certain systems offline and beginning to work with law enforcement to reduce risk. At this time, this incident is limited to Toyota Financial Services in Europe and Africa. ” was the answer. Regarding the status of the system affected by the ransomware attack, a spokesperson said, ``Work is already underway to restore the system to normal operation.''

In addition, security analyst Kevin Beaumont said that Toyota Financial Services' German office has a Citrix Gateway endpoint exposed to the internet, which has not been updated since August 2023 and has serious vulnerabilities. It points out that it remains vulnerable to certain Citrix Bleeds .
https://t.co/vV3COH9UHV pic.twitter.com/GuCN9W0nIo
— Kevin Beaumont (@GossiTheDog) November 16, 2023
Related Posts:
in Security, Posted by logu_ii







