How does iPhone 'jailbreak' work?
The act of ``jailbreaking'' is the opposite of ``rooting'' an Android device, and is the act of acquiring system administrator privileges on an iPhone. These are popular among some software enthusiasts, and while they allow you to obtain apps from sources other than the App Store and improve system operation, they also come with increased security risks. Software developer Philip Ten explains how this 'jailbreak' works.
Exploiting the iPhone 4, Part 1: Gaining Entry | Phillip Tennen
https://axleos.com/exploiting-the-iphone-4-part-1-gaining-entry/
Jailbreaking allows you to make various modifications to apps and systems, but there are disadvantages such as the risk that if you fail, you will not be able to start it again, and that you will no longer receive warranty if you execute it.
The first step to jailbreaking is to obtain your device. Mr. Ten will be using iPhone 4 this time.
There are many ways to jailbreak. Mr. Ten initially tried to use Apple's official development environment 'Xcode', but the latest version of Xcode could not modify the old iOS installed in the iPhone 4, and in the end he found a way to exploit the vulnerability of the boot ROM. We are hiring.

Boot ROM vulnerabilities can typically be exploited by writing some code on the host machine that interacts with the device via USB. The iPhone 4 had a publicly known exploit called
Boot ROM is called SecureROM in Apple terminology. SecureROM is the first step in the iOS boot process and bootstraps the next part of the boot process. SecureROM is responsible for ensuring that whatever you load next is trusted and, in other words, runs only the exact image shipped and signed by Apple.
SecureROM loads one of two components depending on the situation. When the device is doing a 'normal' boot from the file system, SecureROM boots a component called the LLB (Low Level Bootloader) from the disk partition on the NOR. Alternatively, if your device is connected to a computer via USB in DFU (Device Firmware Update) mode, you can start the iPhone restore process by sending the iBSS (iBoot Single Stage) bootloader.
Just as SecureROM verifies that LLB or iBSS is trusted, LLB and iBSS must similarly verify that the next thing it loads is trusted. The flow of each stage will roughly look like this. Each stage loads only what it trusts, so the final user-facing code should always be trustworthy.

One of the major differences between each stage is that SecureROM is implicitly trusted. While all other stages can fix vulnerabilities by releasing iOS updates, SecureROM is something that is carved into read-only memory at the time of device manufacture, and the vulnerabilities found in devices manufactured with one version of SecureROM. The vulnerability will remain permanently unfixed. It is this vulnerability that Mr. Ten exploits.
The aforementioned limera1n exploits a vulnerability in the SoC 'A4' installed in the iPhone 4. limera1n is an exploit that can be exploited when connected to a computer in DFU mode. To use this, Mr. Teng utilized a project called Bootrom-Dumper. Bootrom-Dumper gave Teng insight into how to implement limera1n, what code can be included in the payload, and how to read memory from a device over USB.

It was surprising to Teng that not only could data be written to an iOS device via USB, but the device would also respond to read requests. Teng's understanding is that the A4's MMU maps to base 0x84000000 in SRAM, and the host communicating with the DFU device splits and sends the iBSS image by sending USB control packets with request type 0x21 and request ID 1. That you can do it. Additionally, data sent in control packets is copied to SRAM starting at 0x84000000, and as the host sends more packets, it shifts to higher addresses and SecureROM tracks where the next packet should be copied. There are some internal counters that can be cleared, and these counters can be cleared.
Based on this idea, if the host sends a control packet with request type 0xA1 and request ID 2, the device will also respond. The device reads the contents of memory at 0x84000000 and sends it to the host. If you have the ability to run code on the device and can copy whatever you want to 0x84000000, you can take advantage of this system.

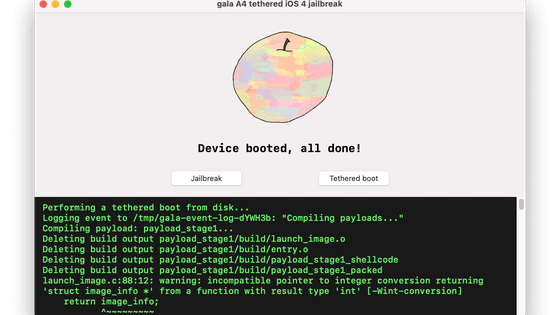
When Mr. Ten wrote his own limera1n implementation based on Bootrom-Dumper and also dumped SecureROM, he was able to successfully achieve his goal and be able to run the code on iPhone 4.

After that, Mr. Ten is building a jailbreak environment 'gala' for iPhone 4. The gala repository is published on GitHub.
GitHub - codyd51/gala: A4 / iOS 4 jailbreak
Related Posts: