Reverse engineering reveals how the 'restart on inactivity' feature in iOS 18.1 works

iOS 18.1, officially released on October 28, 2024, includes
Reverse Engineering iOS 18 Inactivity Reboot
https://naehrdine.blogspot.com/2024/11/reverse-engineering-ios-18-inactivity.html
The restart on inactivity feature is a security feature that automatically restarts your iPhone if it is not unlocked for 72 hours, i.e. 3 days. The main purpose of this feature is to prevent data extraction and unauthorized access from a stolen iPhone.

According to Jiska, the security status of an iPhone is significantly different before and after the first unlocking after rebooting it.
Before the first unlock, Face ID and Touch ID will not work and you will need to enter a passcode. In addition, Wi-Fi passwords are also encrypted, so you will not be able to connect to Wi-Fi. Furthermore, if the SIM is not PIN-locked, you will be able to connect to the cellular network, but contact names will not be displayed when you receive a call, and you will receive message notifications but they will not be previewed.
However, after the first unlock, the system will still have access to certain keys, Wi-Fi will remain connected even when the lock screen is displayed, message notifications will be previewed, and contact information will be available.
However, there are security weaknesses after the initial unlock. For example, if a vulnerability is discovered that allows an attacker to bypass the lock screen, the attacker may be able to access the decrypted data. Especially if physical access is available, more avenues are available to an attacker, such as USB connections, wireless communication, or direct attacks on the hardware.
For law enforcement agencies, data obtained from an iPhone after the first unlock is extremely valuable in an investigation. Therefore, law enforcement agencies often store seized iPhones in an isolated state from the Internet without turning them off in order to ensure time until exploits become available and time required for legal procedures such as obtaining a warrant. However, with the implementation of the reboot on inactivity feature, if a law enforcement agency leaves an iPhone alone for more than three days, it will automatically reboot and return to the state before the first unlock, making it extremely difficult to extract internal data.
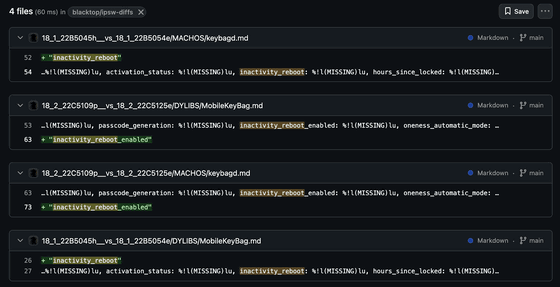
Normally, Apple does not completely conceal new features, but rather leaves them as debug strings, so Jiska first searched for the word 'reboot' using
Further investigation revealed that this string was seen in iOS 18.1 and iOS 18.2, with the latter changing from 'inactivity_reboot' to 'inactivity_reboot_enabled,' suggesting some change in functionality.
To see how the inactivity restart feature actually works, especially how long it takes to restart, Jiska conducted a time-lapse test using a test device updated to iOS 18.2 beta 2. As a result, as you can see in the movie below, it was confirmed that the device automatically restarted after 72 hours. According to Jiska, this restart occurred regardless of whether the device was connected to Wi-Fi or not.
Jiska said further analysis has revealed how the restart on inactivity feature works.
First, the Secure Enclave Processor (SEP) inside the iPhone measures the time since the last unlock. If this time exceeds a threshold of 72 hours, the SEP sends a notification to the AppleSEPKeyStore kernel module. The kernel module then notifies the user space of the need to reboot, and SpringBoard gracefully terminates all user space processes. This ensures a safe reboot without data loss.
According to Jiska, the AppleSEPKeyStore kernel module has a built-in safety mechanism that is designed to trigger a kernel panic if the iPhone remains powered on after a reboot is required, which he speculates is a defense against tampering with the reboot on inactivity feature.
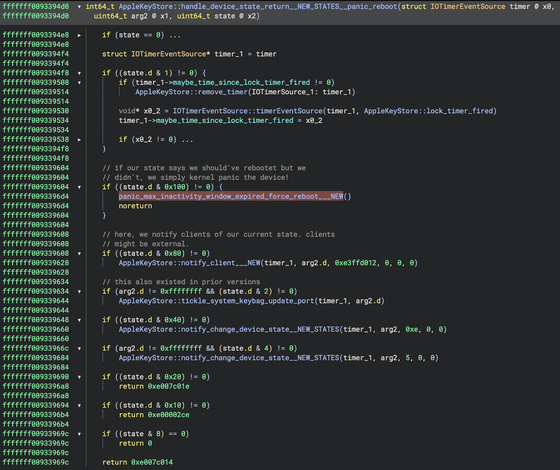
Additionally, the AppleSEPKeyStore kernel module writes an NVRAM variable called “aks-inactivity.” After reboot, keybagd reads this variable and sends analytics data to Apple, including how long it has been since the iPhone was last unlocked.
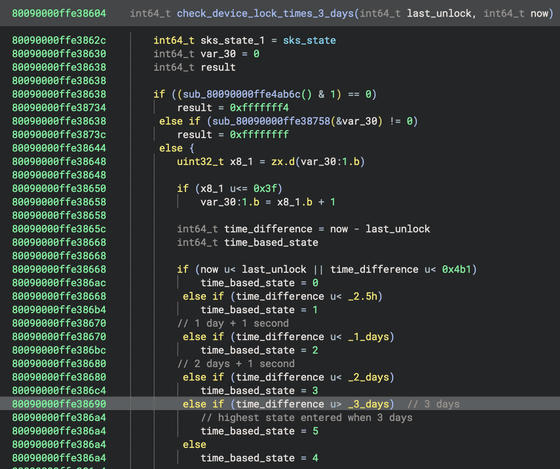
Jiska analyzed the SEP and found that the time value of 72 hours (259,200 seconds) was not found in the SEP firmware, but was implemented in a split form by compiler optimizations.
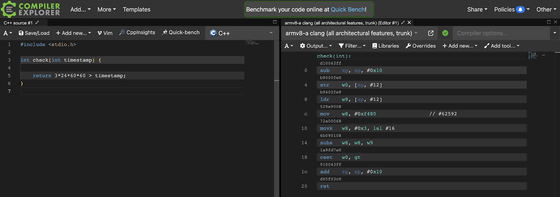
Furthermore, analysis of the SEP firmware revealed that an application called “sks” had the ability to compare multiple time values – 2.5 hours, 1 day, 2 days, and 3 days – and send a message to a kernel extension based on the result.
'SEP is involved in all unlock operations and has robust protection against attacks on the main kernel, making it an ideal foundation for security features,' Jiska said. 'This protects the reboot on inactivity feature even in the event of a kernel-level attack.'
While many media outlets have reported on the inactivity restart feature as a way to limit law enforcement activities, Jiska points out that it also has an important security improvement aspect against device theft. Thieves will not have the funds or legal means to unlock the iPhone within three days of obtaining it, making it much more difficult to access the data inside. Meanwhile, law enforcement agencies can extract data within 72 hours by working closely with forensic investigation companies. Jiska evaluated that the inactivity restart feature significantly improves the privacy and security of ordinary users, since criminals are effectively unable to access bank account information and other valuable data stored on the iPhone, while law enforcement agencies can conduct legitimate investigations within time constraints.
Related Posts:
in Video, Software, Smartphone, Security, Posted by log1i_yk