A person who created a macro pad that can complete the troublesome ``one-time password input for two-factor authentication'' in an instant appears

2FA_Sidecar | Hackaday.io
https://hackaday.io/project/191580-2fasidecar
Hackaday Prize 2023: Sleek Macro Pad Makes 2FA A Little Easier | Hackaday
https://hackaday.com/2023/06/20/hackaday-prize-2023-sleek-macro-pad-makes-2fa-a-little-easier/
Anyone who cares about security knows that setting up two-factor authentication is critical to staying safe online. However, you may also find it annoying to check your generated one-time password via SMS, mailbox, or dedicated physical token every time you log into your account or perform an important operation.
Therefore, Matt Perkins, a hardware enthusiast living in Australia, created his own macro pad ' 2FA Sidecar ' that allows you to enter a one-time password for two-factor authentication with a single key press. “I developed this device because I spend a lot of time opening my phone, entering codes, and switching security levels in different parts of the network that I manage in my day job,” Perkins said. says.
You can see what kind of device 2FA Sidecar is by watching the following video.
2FA Sidecar-YouTube
2FA Sidecar looks like this. The elongated device has a small LCD display on the left edge and five keys attached to the right side of it.

The name of the five registered services and the current one-time password are displayed on the liquid crystal display.
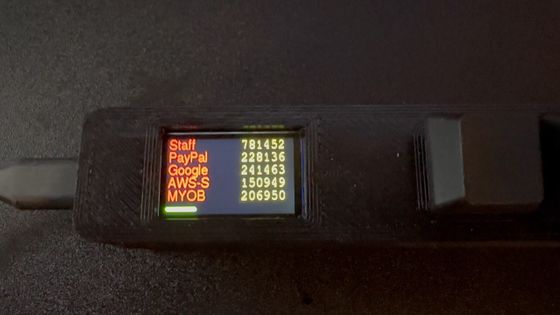
Over time, the displayed one-time password was also updated. 2FA Sidecar supports an authentication technology called

To set up 2FA Sidecar, press the key closest to the LCD within 3 seconds after connecting the device with USB, then press the keys in order until 'Test Pass' is displayed on the LCD.

You will then be able to access the 2FA Sidecar settings configuration form.
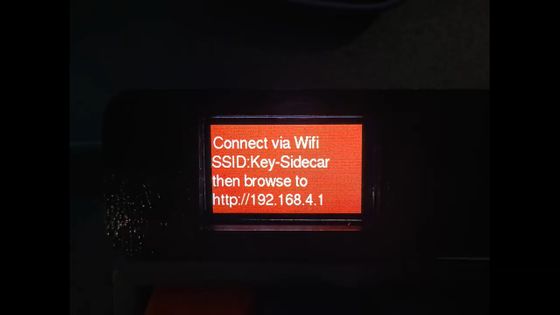
The setting screen looks something like this. There are fields to enter your Wi-Fi password, time zone, service name that uses two-factor authentication, and one-time password salt. You can check the salt of the one-time password associated with your account by decoding the QR code displayed when you set two-factor authentication on the service you want to authenticate. By storing the time zone and salt in 2FA Sidecar, you can always generate a suitable one-time password.

When you restart 2FA Sidecar after completing the settings, it will automatically connect to the local Wi-Fi, recognize the correct time, and start generating a one-time password. In fact, connect the 2FA Sidecar with the completed settings to the device via USB.

Then, I was able to enter the one-time password of the corresponding account at once by pressing the key once. You can also see the numbers displayed on the LCD screen and enter them yourself.

2FA Sidecar can be made by assembling commercially available microcontroller ESP32 and 3D printed parts, and the following GitHub page explains how to make it.
GitHub - mattaperkins/2FA_Sidecar
https://github.com/mattaperkins/2FA_Sidecar
Related Posts: