A method to steal the encryption key by video shooting the power LED of the device is demonstrated

Many electronic devices have LEDs to indicate whether they have power. Hacker Ben Nassy and others have revealed a video-based cryptanalysis method that can restore the encryption key of the device by shooting a video of this LED.
Video-Based Cryptoanalysis
Hackers can steal cryptographic keys by video-recording power LEDs 60 feet away | Ars Technica
https://arstechnica.com/information-technology/2023/06/hackers-can-steal-cryptographic-keys-by-video-recording-connected-power-leds-60-feet-away/
Below is a movie that briefly explains what this method is.
Video-Based Cryptanalysis-YouTube
The amount of power consumed when a device performs processing that uses the CPU is not always constant.
Changes in power consumption appear as a slight flicker of the power LED.
Also, the LEDs of other devices connected to the device will flicker.
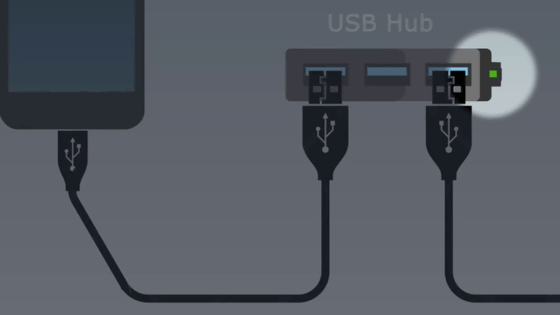
Nassy et al. developed a method of photographing the flickering of this LED with a smartphone camera or security camera.
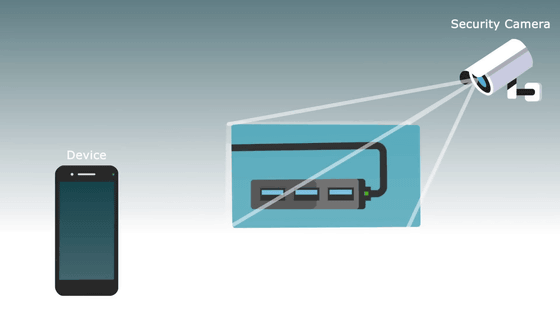
This allows the attacker to obtain the secret encryption key that the device uses for encryption and decryption.

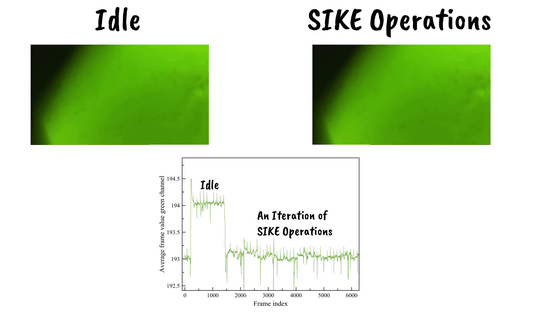
As a method, we magnify the captured image of the power LED and use the rolling shutter to read the color.
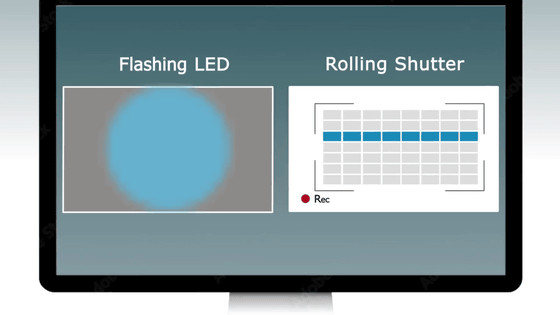
Identify the start and end points of cryptographic operations by capturing subtle changes in LED color from frame to frame.
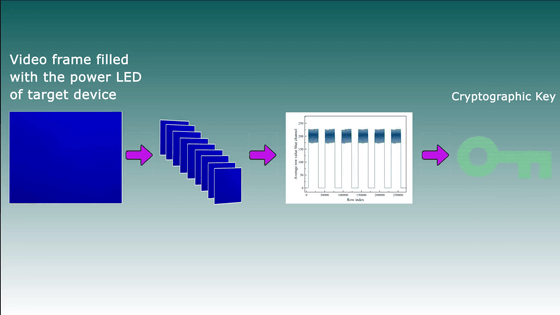
Specifically, the 378-bit encryption key for the Galaxy S8 was obtained by photographing the LED of the speaker connected to the same USB hub that charges the Samsung Galaxy S8 with the camera of the iPhone 13 Pro Max. It was said that it was done.
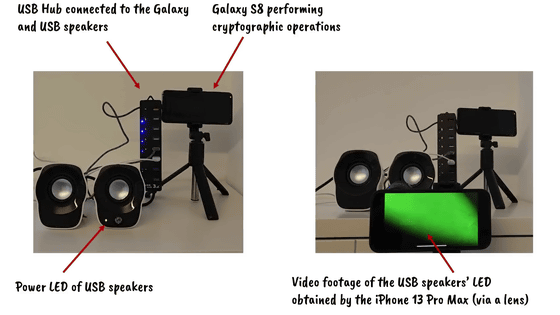
The difference in LED color was so great that it could not be seen with the naked eye, but there was a subtle difference in the RGB values.
Also, in the case of a smart card reader, a 256-bit ECDSA key was obtained by photographing the LED with a network camera from a distance of 16m and analyzing the image.
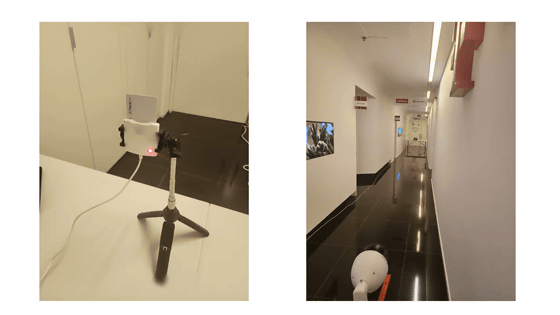
According to Nassy et al., this vulnerability is not a power LED but a cryptographic library problem, but the power LED provides a visual infrastructure for exploitation.
It seems that the way to prevent the attack demonstrated this time is to use the latest cryptographic library.
Related Posts: