Kaspersky warns that there is a case where money was actually stolen with a ``super sophisticated counterfeit'' of a terminal ``cryptocurrency wallet'' that can manage virtual currency independently

Some people who own virtual currency such as bitcoin own a ``digital wallet terminal'' that independently stores private keys for accessing virtual currency and increases security. There is also Kaspersky, a security company that investigated these terminals, warned that ``there are super-sophisticated fakes with vulnerable specifications from the beginning.''
Review and analysis of fake Trezor cryptowallet | Kaspersky official blog
Some people who work with cryptocurrencies believe that it is safer to store private keys on a single device that they can control, rather than storing them on other network-connected devices. These people have a terminal called a ' cryptocurrency wallet ' and use it for the purpose of managing private keys and improving the security of signatures.
Several types of these terminals are on sale, and Tony Fadell, known as the inventor of the iPod, has just reported that he has developed a cryptocurrency wallet. Mr. Fadell's ' Ledger Stax ' is like this.
Kaspersky, who analyzed such a cryptocurrency wallet, considered a problem with a terminal called '
Kaspersky points out that ``Trezor Model T theoretically has a mechanism to reliably protect the device from attackers.'' Both the box and the main body of this product were sealed with a holographic sticker, and the embedded microcontroller had a 'read protection mode (RDP 2)' turned on to prevent unauthorized reading of the flash memory. . In addition, the bootloader would check the digital signature of the firmware and, if anomalies were detected, display a non-original firmware message and delete all data in the wallet.
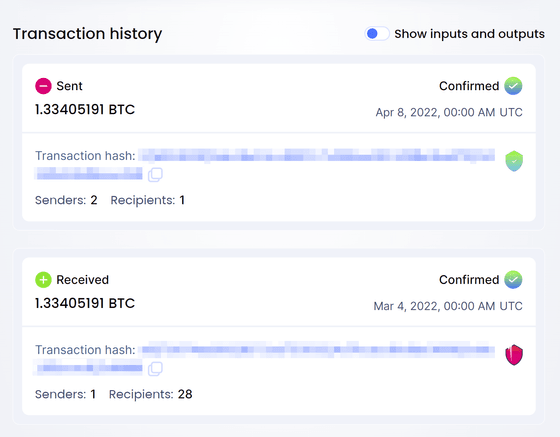
When Kaspersky examined the victim's device, it looked exactly like a genuine device and showed no signs of tampering. The victim purchased the product from a trusted seller through a well-known site, and all the holographic stickers on the box and wallet body were present as usual and undamaged. In practice, everything works fine and the user interface is the same as the original. However, it seems that it turned out to be interesting when investigating in detail keeping in mind the fact that 'there was actual damage'.
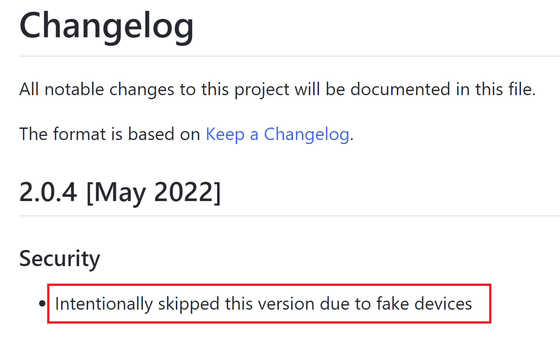
When Kaspersky examined the firmware version of the victim's terminal, it said that '2.0.4' was displayed as the boot loader version. However, this 2.0.4 was never actually released.
Looking at the project change history published by the developer on GitHub, the version is simply written as ``skipped due to fake device''.
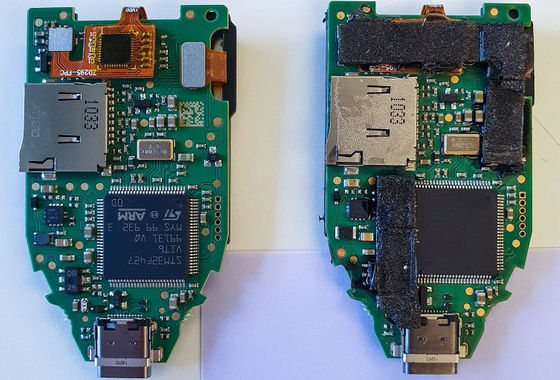
Also, when Kaspersky disassembled the product, it was said that a completely different microcontroller with soldering traces was installed inside. The original (left image) had a product called 'STM32F427', while the counterfeit (right image) has an 'STM32F429' and the microcontroller's read protection mode has been completely removed. rice field.
Cryptocurrency wallets typically contain a private key that allows anyone who knows the key to sign any transaction and spend the money. In the case of this victim, we can speculate that the private key was leaked somewhere.
According to Kaspersky, the bootloader protection mechanism and digital signature check were removed from the victim's device, and the seed value used to set the protection password was also fixed. The attacker had complete control over the device from the beginning, and the damage was inevitable when the victim deposited money into their wallet.

Kaspersky said, “Without special knowledge and experience, it is not easy to distinguish between fake and genuine wallets. It's about choosing a model.In this context, the original Trezor is also not ideal, as there are other brands of wallets with better protective chips and additional protection.'
Related Posts:







