Should the '.zip' domain, which has begun general registration, be revoked?

In May 2023, Google's domain registry service '
The .zip TLD sucks and it needs to be immediately revoked.
https://financialstatement.zip/

New TLDs: Not Bad, Actually – text/plain
Programmer
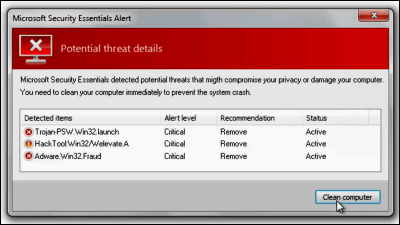
'Financialstatement' is a financial statement, a financial statement, and if a file named 'financialstatement.zip' was attached to an email from an important business partner, some people would open it.
Some Internet services and web applications have a function that automatically links when there is a URL and allows you to move by simply clicking or tapping, but in the case of this domain, ' When you think the file 'financialstatement.zip' opens, you may end up going to 'https://financialstatement.zip/'.
Karen isn't the only one with this kind of worry.
Security expert SwiftOnSecurity pointed out that ``it is used for attacks such as phishing and causes unnecessary confusion.''
Regarding the .zip domains I complained about – I think it's dumb and unnecessarily creates confusion and will leave to various minor phishing schemes/tricks/address-confusion attacks... but it's just going to get forced into being another TLD. uniquely unneeded.
—SwiftOnSecurity (@SwiftOnSecurity) May 12, 2023
And in the first place, the TLD itself 'zip' was sold for fun, saying, 'I tried it because it was originally known as a file extension, and it was made into a domain.' Even if it wasn't fear, he continued that he was worried that it wasn't a good behavior from a manager's point of view.
The only reason there's a .ZIP TLD is because it's funny to confuse people, it markets off the 'this used to just be a file extension and now we changed it because we could.' So even if it's not a uniquely horrific, it's just not a good action of stewardship and that's worrying.
—SwiftOnSecurity (@SwiftOnSecurity) May 12, 2023
While there are concerns about these 'zip' TLDs, Eric Lawrence, creator of the packet capture tool Fiddler and the command line support utility SlickRun , certainly believes that automatic links can't access unintended domains. It is possible, but not a very attractive attack vector.
Also, in response to the opinion that the famous file extension becomes TLD and causes confusion in URLs, I dismissed it as 'the argument is not persuasive.' This is because even before the introduction of the ``zip'' TLD, ``.zip'' could be slipped into a URL component, and the fact that hostnames now end in ``.zip'' is not interesting at all. It is because there is no.
Another area of concern is Google Chrome's omnibox (a search box combined with an address bar). Omnibox uses a certain code to determine whether the given string is a URL or a search request. The first is whether it is a known TLD, and the input 'example.zi' is considered a search request.
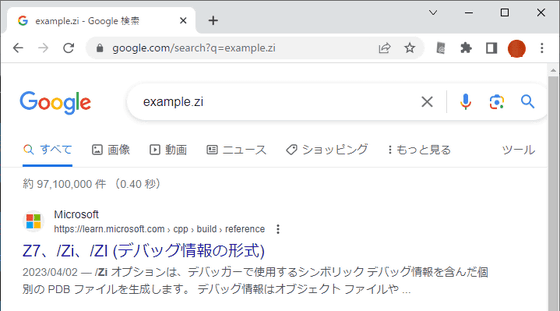
On the other hand, 'example.zip' is interpreted as trying to open 'https://example.zip/'.
To avoid this, it is necessary to explicitly switch the mode by entering '?' at the beginning of the search and entering '//' at the beginning of the URL input. However, regarding the ambiguous behavior of this omnibox, even before the ``zip'' domain, ``.com'', which is also used as an extension for executable files, and the extension for programs written in Perl, the Polish country code Mr. Lawrence points out that it is occurring in '.pl' etc.
Mr. Lawrence, who has a theory that ``new TLDs are not so bad,'' explained that 40 types of TLDs, including ``zip'' and ``mov,'' are excellent in terms of security. For example, with HSTS preloading, these TLDs automatically convert 'http://' to 'https://' when entered. Requiring HTTPS for the entire TLD means that all sites within the TLD are required to have a certificate, which means that security is taken into consideration.
In addition, Mr. Lawrence said that among the opinions of those who express concern, the function itself that automatically links when one of the 1479 TLD strings is included should not be introduced. As an aside, after speaking with autolink library authors, most of them convert 'example.com' to 'http://example.com' instead of the secure 'https://example.com'. Mr. Lawrence indicates that there was a fact that
Related Posts:
in Note, Posted by logc_nt