Darcula, a service that provides phishing tools that target iPhone users via iMessage, has appeared

Darcula , which is an illegal service called
Out of the shadows - 'darcula' iMessage and RCS smishing attacks target USPS and global postal services | Netcraft
https://www.netcraft.com/blog/darcula-smishing-attacks-target-usps-and-global-postal-services/
New Darcula phishing service targets iPhone users via iMessage
https://www.bleepingcomputer.com/news/security/new-darcula-phishing-service-targets-iphone-users-via-imessage/
One of the features of Darcula is that it uses rich communication services (RCS) such as Google Messages and iMessage to approach targets instead of SMS to send phishing messages. Even if it is confirmed, Darcula targets a variety of services and organizations, including the postal service, finance, government, tax departments, telecommunications companies, airlines, and public utilities.
Darcula is a PhaaS that was first documented in the summer of 2023 by Oshri Kalfon, a security researcher working at the cybersecurity company Netcraft . Darcula has been attracting attention in the cybercrime field in recent years, and has 'caused several notable incidents,' security media Bleeping Computer pointed out.
Cyberattacks using Darcula include a message-based phishing scam against both Apple and Android devices in the United Kingdom in 2023, as well as a parcel scam impersonating the United States Postal Service .

Unlike traditional phishing scams, Darcula leverages modern technologies such as JavaScript, React, Docker, and Harbor, allowing attackers to continually update and add new features without having to reinstall Darcula. It will be possible to do so.
Darcula has over 200 templates impersonating brands and organizations from over 100 countries, and BleepingComputer says, 'The landing pages are high quality and use the correct local language, logos and content.' did.
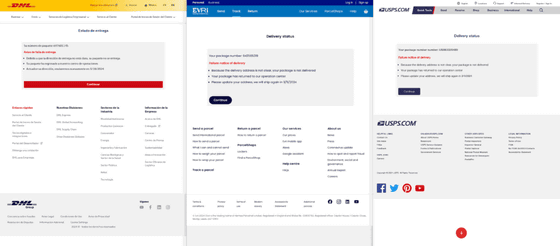
Attackers using Darcula select the brand/organization to impersonate and select the corresponding phishing site template. Next, run the setup script to install the management dashboard directly into your Docker environment.
Darcula uses Harbor, an open source container registry, to host Docker images, and the phishing site is developed using React.
According to security researchers, Darcula uses top-level domains such as .top and .com to host domains registered for phishing, about one-third of which are registered by Cloudflare. Supported.
The 20,000 domains used by Darcula are mapped to 11,000 IP addresses, and according to Netcraft, ``120 new domains are added every day.''

Darcula uses RCS to send phishing site URLs to targets because RCS supports end-to-end encryption and is recognized as a 'secure messaging service.' Even with end-to-end encryption, messages cannot be blocked based on message content. In other words, no amount of RCS can prevent messages that invite you to commit phishing scams.
Netcraft points out that because SMS attempts to suppress the occurrence of cybercrime by blocking messages from suspicious sources, ``PhaaS is likely to migrate to alternative protocols such as RCS and iMessage.''
To combat these cyberattacks, Apple has blocked accounts that send large numbers of messages to multiple recipients, and Google has introduced restrictions that prevent rooted Android devices from sending and receiving RCS messages. .
Heads up: Users are reporting that the Google Messages app won't let them send or receive RCS messages if the OS is rooted or hasn't passed GMS certification (like most custom ROMs).
— Mishaal Rahman (@MishaalRahman) February 29, 2024
It seems that Google Messages has implemented Play Integrity API attestation checks, so be aware… pic.twitter.com/IwEKJQ0Z2v
However, attackers are attempting to circumvent this restriction by creating multiple Apple IDs and sending messages to a small number of people.
In addition, iMessage has a safety feature that makes the URL contained in the message available only if you reply to the message. In order to circumvent this safety feature, Darcula users seem to send messages such as 'Reply Y' or 'Reply 1' to recipients. When the user replies to this, the URL in the message becomes available.
Netcraft recommends 'watch out for inaccurate grammar, misspellings, overly attractive offers, and urgent calls to action.'
Related Posts: