Reported that TikTok's Android application had a ``vulnerability that accounts can be hijacked with one tap''

A security research team at Microsoft 365 Defender has reported that it has discovered a high-severity vulnerability in the TikTok Android application. With this vulnerability, an attacker could compromise a victim's account and send unsolicited messages or upload videos with a single tap on a malicious URL. is.
Vulnerability in TikTok Android app could lead to one-click account hijacking - Microsoft Security Blog
Microsoft found TikTok Android flaw that let hackers hijack accounts
https://www.bleepingcomputer.com/news/security/microsoft-found-tiktok-android-flaw-that-let-hackers-hijack-accounts/
There are two types of TikTok Android apps: the package 'com.ss.android.ugc.trill' for East and Southeast Asia and the package 'com.zhiliaoapp.musically' for other countries. The security research team says that this vulnerability affects both types.
According to the security research team, this vulnerability is due to `` WebView '' that allows Android to display web content without using a browser. By loading unreliable web content with this WebView, it seems that it is possible to leak data, destroy data, and execute arbitrary code using JavaScript.
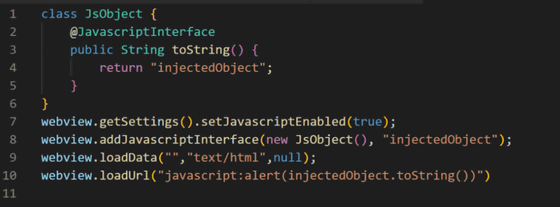
An exploit that exploits this vulnerability will allow an attacker to arbitrarily obtain a user's authentication token, or to obtain or change the user's TikTok account data.
Microsoft notified TikTok of this issue in February 2022, identified this vulnerability as CVE-2022-28799 , and released a corresponding fix. Therefore, the vulnerability in question has been fixed at the time of article creation. The security research team also states that there is no evidence that CVE-2022-28799 has been exploited.
'From a programming perspective, a compromised JavaScript interface could allow an attacker to execute arbitrary code using the app's identity and privileges,' said the security research team. There are risks involved, and we encourage the developer community to be aware of the risks and take extra precautions to protect WebView.'
In addition, the security research team calls on users to pay attention to the following four points to protect themselves from exploitation of these vulnerabilities.
Don't tap links from untrusted sources.
- Keep your device and installed apps up to date.
- Do not install apps from untrusted sources.
・Immediately report to the vendor if abnormal behavior of the app is confirmed, such as settings being changed without permission.
Related Posts:
in Software, Smartphone, Security, Posted by log1i_yk







