It has been revealed that Android apps containing North Korean spyware 'KoSpy' were distributed on Google Play

Researchers have discovered several Android apps, some of which had passed Google's security review and were distributed on Google Play, that secretly upload users' sensitive information to spies working for the North Korean government.
Lookout Discovers North Korean APT37 Mobile Spyware | Threat Intel
Android apps laced with North Korean spyware found in Google Play - Ars Technica
https://arstechnica.com/security/2025/03/researchers-find-north-korean-spy-apps-hosted-in-google-play/
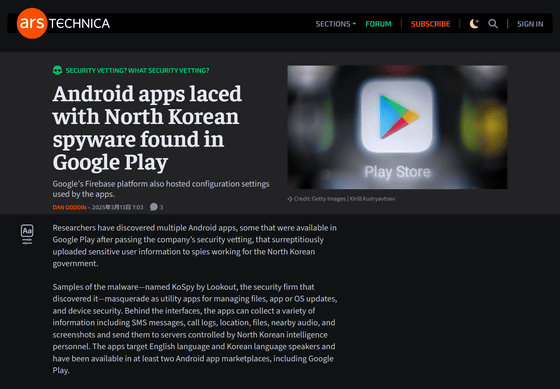
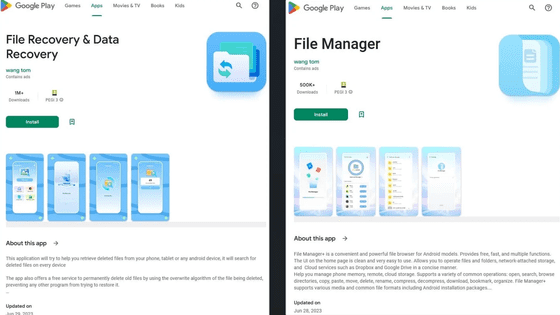
The North Korean spyware discovered by security company Lookout has been named 'KoSpy,' and while disguised as a file manager, phone manager, software update utility, security management utility, etc., it can collect various information such as files, audio, and screenshots on the user's device and secretly send it to a server controlled by North Korean spies.
KoSpy targets English and Korean speaking users and appears to have been distributed not only on Google Play but also on the third-party app marketplace Apkpure. Below is 'File Manager,' one of the KoSpy-containing apps distributed on Google Play.
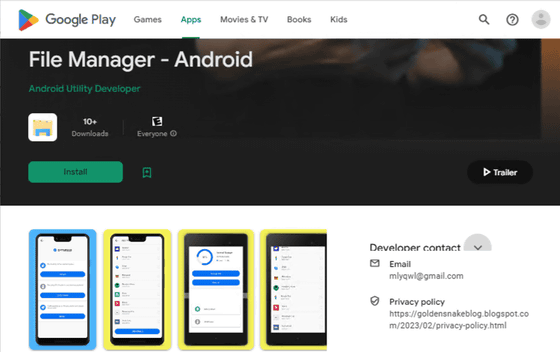
The developer of 'File Manager' has an email address of 'mlyqwl@gmail.com', and the app's privacy policy page is '
However, the IP address hosting the 'File Manager' command and control server has been confirmed to have previously hosted three domains known to have hosted infrastructure that has been used for North Korean espionage operations since at least 2019.

KoSpy apps not hosted on Google Play were found to rely on a two-stage command-and-control server and retrieve configuration settings from a database hosted on Firebase , a web application development platform provided by Google. Google responded by saying it had removed both the apps and the configuration database.
Technology media Ars Technica has reached out to Google for details on exactly how long the KoSpy app was hosted on Google Play, but has not received a response at the time of writing. A Google spokesperson reported that the app was removed before it was available for download from Google Play, but did not respond to Ars Technica's request for data. The spokesperson also noted that Google Play Protect , a security feature offered by Google for Android, 'can detect malicious apps installed on a device, even if they were installed from outside Google Play.'
Related Posts: