Vulnerability ``AutoSpill'' that can steal credentials by exploiting WebView from Android password manager is discovered

At the security conference '
AutoSpill: Credential Leakage from Mobile Password Managers | Proceedings of the Thirteenth ACM Conference on Data and Application Security and Privacy
https://dl.acm.org/doi/10.1145/3577923.3583658
Your mobile password manager might be exposing your credentials | TechCrunch
https://techcrunch.com/2023/12/06/your-mobile-password-manager-might-be-exposing-your-credentials/
Vulns in Android WebView, Password Managers Can Leak User Credentials
https://www.darkreading.com/cyberattacks-data-breaches/android-vulnerability-leaks-credentials-from-password-managers-
Password managers are used by many PC and smartphone users because they manage IDs and passwords for apps and web services and automatically enter them when needed. However, security researchers at the Hyderabad International University of Information Technology have discovered a vulnerability called AutoSpill that allows users to bypass Android's secure autofill mechanism and steal credentials from mobile password managers.
Android and iOS mobile apps do not always display only the app screen, but may also display web content as needed. Since it is troublesome to leave the app and open the browser each time, many apps have a function called ' WebView ' that allows you to display web pages within the app.
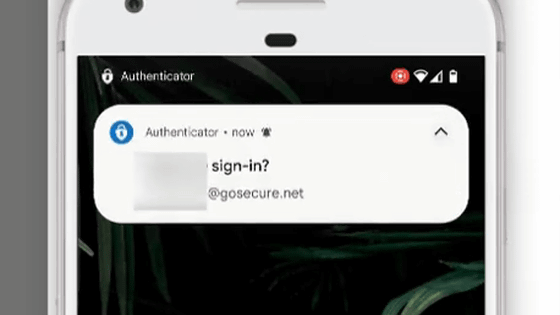
The researchers found that when an Android app uses WebView to open a login page, password managers attempting to autofill credentials can become 'confused' and accidentally expose credentials to the app's native fields. I discovered that there is a sex.
'Suppose you try to log in to your favorite music app on your mobile device and use the 'Log in via Google or Facebook' option,' said Ankit Gangwal of the research team. If a password manager is invoked to autofill credentials, ideally it should only autofill on Google or Facebook pages that are loaded.However, the autofill operation may cause the credentials to be We now know that it can be inadvertently exposed to the base app.'

This vulnerability, named AutoSpill, is particularly serious if the base app is malicious. Gangwal noted, 'Even if it's not phishing, malicious apps that ask you to log in through other sites, such as Google or Facebook, can automatically access sensitive information.'
In fact, the research team tested whether AutoSpill works on the latest Android devices using popular password managers such as 1Password, LastPass, Keeper, and Enpass. As a result, most apps were vulnerable to AutoSpill even when
The research team has already warned Google, which develops Android, and companies developing affected password managers about AutoSpill.

Pedro Canahuati, 1Password's chief technology officer (CTO), claims to technology media TechCrunch that 1Password has identified AutoSpill and is working on a fix. 'While this fix further strengthens our security posture, 1Password's autofill functionality was originally designed to require explicit action from the user. Further protection is provided by preventing credentials from being entered that are intended only for WebViews,' Canahuati said.
Additionally, Alex Cox, director of LastPass' Threat Intelligence, Mitigation, and Escalation team, said that even before the findings of this study were known, LastPass was making in-product updates when an app detected an attempt to exploit an exploit. It claims to have displayed a pop-up warning. 'After analyzing our findings, we added more helpful language to the pop-up,' Cox told TechCrunch.
In addition, the research team is investigating the possibility that an attacker can extract authentication information from the application to WebView, and is also investigating whether AutoSpill can be reproduced on iOS.
Related Posts:
in Smartphone, Security, Posted by log1h_ik