Introducing 'Blacksmith', a tool that can break through the security of almost all memory

Research teams at the ETH Zurich, Amsterdam Institute of Technology, and Qualcomm have announced that they have succeeded in identifying a method that can disable security measures for
Blacksmith – Computer Security Group
https://comsec.ethz.ch/research/dram/blacksmith/
New Rowhammer technique bypasses existing DDR4 memory defenses
https://www.bleepingcomputer.com/news/security/new-rowhammer-technique-bypasses-existing-ddr4-memory-defenses/
Rowhammer defenses in RAM chips can still be defeated • The Register
https://www.theregister.com/2021/11/15/rowhammer_blacksmith_memory/
DDR4 memory protections are broken wide open by new Rowhammer technique | Ars Technica
https://arstechnica.com/gadgets/2021/11/ddr4-memory-is-even-more-susceptible-to-rowhammer-attacks-than-anyone-thought/
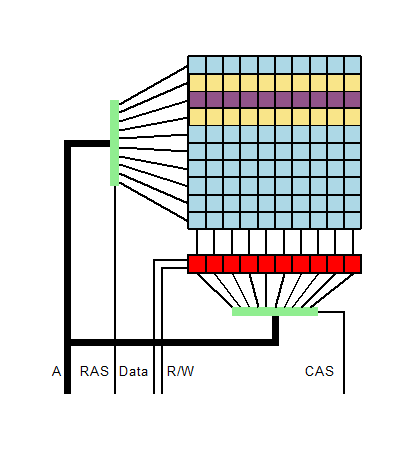
Discovered in 2014, the ' row hammer ' rewrites the contents of surrounding rows when a specific row of cells in memory is accessed intensively, which causes problems such as privilege escalation. It is a defect to do.
by
For row hammer, memory makers have developed a security function called 'Target Row Refresh (TRR)' and implemented it in memory such as DDR4. This is a technology to prevent the occurrence of row hammer by detecting the row targeted by row hammer and refreshing the data of the rows around it.
COMSEC, a security research group at the ETH Zurich, who was verifying this security function, focused on a method called 'TR Respass' that avoids TRR by accessing memory in a complicated pattern. We have developed 'Blacksmith', a fuzzing tool that has the ability to determine patterns that effectively disable TRR.
When the research team ran Blacksmith for 12 hours on 40 randomly selected DDR4 memories, row hammer occurred on all the memories tested. The memory tested includes memory from Samsung, Micron, and SK Hynix, which has a total market share of 94% in the memory market, and memory from three more companies whose brand names are hidden. Was there.
From this result, the research team confirmed that 'the memory maker's claim that row hammer has been dealt with is wrong and leads to a false sense of security. All current measures are against row hammer. It is inadequate and has been shown to make it easier for attackers to break into the system than previously expected. '
In order to allow memory makers and others to verify this problem, the research team will publish Blacksmith on GitHub, and other than memory makers such as memory makers Samsung, Micron, SK Hynix, AMD, Google, Intel, Microsoft, Oracle, etc. Reported the research results to the IT company of.
At the time of writing the article, the row hammer method discovered this time cannot be used without an actual machine, and it is considered that it is not an imminent threat to general Internet users. However, due to the difficulty of hardware-based countermeasures, the severity of this vulnerability, registered as CVE-2021-42114, was rated 9 out of 10.
Bleeping Computer, an IT news site, said, 'The DDR5 memory that has begun to hit the market uses a system called' refresh management 'instead of TRR, so row hammer does not seem to be a problem. But I'm still not sure if it's really safe. '
Related Posts: