A malware attack that avoids automatic detection appears by requesting 'CAPTCHA'
To evade detection, hackers are requiring targets to complete CAPTCHAs | Ars Technica
https://arstechnica.com/information-technology/2020/06/to-evade-detection-hackers-are-requiring-targets-to-complete-captchas/
Microsoft warned against using CAPTCHA to bypass automatic malware detection. The victim first accesses the landing page where CAPTCHA is implemented by accessing the URL described in the email or opening the attached Excel file. Then, by unlocking CAPTCHA, it downloads the Trojan horse 'GraceWire' that steals confidential information such as passwords.
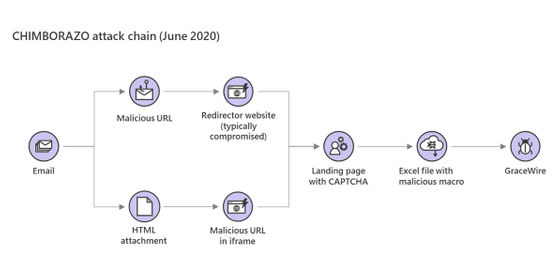
This method requires the victim to unzip CAPTCHA in order to download the malicious file. However, by implementing CAPTCHA, it is possible to avoid mechanical 'automatic detection' implemented by security companies and browsers themselves.
According to Microsoft, the attacker is a hacker group called 'CHIMBORAZO'.
CHIMBORAZO, The Group Behind Dudear Campaigns That Deploy The Info-Stealing Trojan GraceWire, Evolved Their Methods Once Again In Constant Pursuit Of Detection Evasion. The Group Is Now Using Websites With CAPTCHA To Avoid Automated Analysis. Pic.Twitter.Com/Kz3cdwYDd7
— Microsoft Security Intelligence (@MsftSecIntel) June 17, 2020
According to Jérôme Segura, head of threat intelligence at cybersecurity firm Malwarebytes, malware attacks using CAPTCHAs are rare, but precedents exist. In December 2019, a similar technique was reported to request Google's reCAPTCHA- like CAPTCHA.
papiladesigninc[.]com identified as an Emotet Epoch 2 site is also hosting a @canadapostcorp #Phishing page. Delivering a .vbs dropper (detection 2/60) after completing a fake Google #reCAPTCHA #danabot https://t.co/ 3V75Dnlpms pic.twitter.com/tdpdvmOm8E
— V1rgul3 (@Secu0133) December 22, 2019
“Regularly changing attack routines is one way attackers can outsmart defenders,” said Ars Technica, an IT news site. Attack groups could change attack vectors again in the coming months. Yes, we must be vigilant to prevent all attacks.”
Related Posts:
in Security, Posted by darkhorse_log