The password generated by Kaspersky's password manager turned out to be able to break through the detonation velocity with a brute force attack, why?

Security research company Ledger Donjon had a problem with the program of password manager 'Kaspersky Password Manager (KPM) ' developed by security company Kaspersky, and the generated password was very vulnerable to brute force attacks. Announced that it turned out. A message prompting KPM users to update their password has already been sent, and it is said that the problem has already been fixed at the time of writing the article.
Kaspersky Password Manager: All your passwords are belong to us | Donjon
https://donjon.ledger.com/kaspersky-password-manager/
Kaspersky Password Manager's random password generator was about as random as your wall clock • The Register
https://www.theregister.com/2021/07/06/kaspersky_password_manager/
There are many ways to generate a password, but KPM combines randomly selected letters, numbers, and symbols to generate a password.
For example, if you want to output characters from a set of 10 characters with a random number generation method called GetRandom32, you can write with the following code.
[code] const string charset = '0123456789';
return charset [GetRandom32 ()% 10]; [/ code]
Since the flow is to randomly select a number from 0 to 31 with 'GetRandom32 ()' and return the remainder after dividing by 10 to charset, the probability that 0 and 1 will be returned will be a little higher if this is left as it is. I will. Therefore, it is necessary to modify it so that it ignores the time when 31 and 32 appear in 'GetRandom32 ()'. It is said that a method similar to this is adopted for random generation of passwords in KeePass, a password manager developed in open source.
[code] const string charset = '0123456789';
do {
uGen = GetRandom32 ();
} while (uGen> = 30);
return charset [uGen]; [/ code]
In this way, what is important in random generation is that 'characters are selected from a specified range with a uniform probability.' If the probabilities are biased, the password will inevitably be less secure.
In 2019, Ledger Donjon investigated the password generation features built into KPM. KPM's password generation function creates a 12-character password by default from uppercase letters, lowercase letters, numbers, and special characters. The character set used for the password is customizable and can be set from the password generation UI.
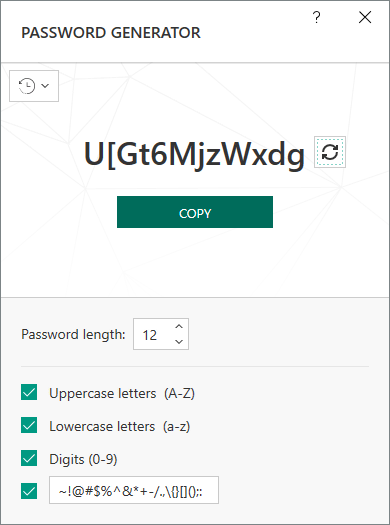
'There are some problems with the password generator included in KPM,' said Ledger Donjon's research team. The most serious problem was that they used a pseudo-random number generator (PRNG) called the 'Mersenne Twister.' And we used the device's system time for that seed value. '
The code for the KPM password generation function is below. The seed is defined as the sum of the lower 32 bits (ft.dwLowDateTime) and the upper 32 bits (ft.dwHighDateTime) of the system time.
[code] std :: string pwlib :: generatePassword (pwdlib :: Policy policy, int seed)
{
if (seed == 0) {
FILETIME ft;
GetSystemTimeAsFileTime (& ft);
seed = ft.dwLowDateTime + ft.dwHighDateTime;
}
auto mtrand = std :: bind (std :: uniform_real_distribution
return generateRandomPassword (policy, mtrand);
} [/ code]
As the name implies, the pseudo-random number generator looks random at first glance, but it calculates the number with a certain algorithm. Then, the seed value is set as the initial state, and if the seed value is the same, the same number is always generated for the pseudo-random number.

The fact that the system time of the PC was used as the seed value for pseudo-random number generation means that the password generated by KPM was the same if the system time was the same.
In addition, on the KPM screen, an animation was adopted in which a large number of character strings flowed when the password was generated. The research team points out that the animation played for more than a second, so the password generation button wasn't pressed within a second, delaying the discovery of the issue.
Converting 2010 to 2021 into seconds, it is approximately 315,619,200 seconds. This means that from 2010 to 2021, there are only 315,619,200 patterns of passwords generated by KPM. According to the research team, a brute force attack on the 1561,919,200 patterns of passwords can be broken through in just a few minutes. Also, considering that the account creation time is narrowed down to some extent, it is highly possible that the account will be broken in seconds.

The research team sent a report and proof of concept to Kaspersky Lab in June 2019 regarding this KPM password generation vulnerability. Kaspersky has assigned the identifier 'CVE-2020-27020 ' to this vulnerability and distributed a patch in October 2020. It also advises users to regenerate their passwords after installing the patch. In addition, Windows version, iOS version, Android version will be affected, and the following versions or earlier will be affected.
-Kaspersky Password Manager for Windows 9.0.2 Patch F
・ Kaspersky Password Manager for Android 9.2.14.872
・ Kaspersky Password Manager for iOS 9.2.14.31
Related Posts:
in Security, Posted by log1i_yk