A critical vulnerability in Next.js that has existed for several years has allowed hackers to bypass middleware-based authentication, and Vercel fixed the vulnerability on March 18th.

A critical vulnerability has been discovered in Next.js , an open source web development framework, that could allow an attacker to bypass authentication checks.
Next.js and the corrupt middleware: the authorizing artifact - zhero_web_security
https://zhero-web-sec.github.io/research-and-things/nextjs-and-the-corrupt-middleware
Critical flaw in Next.js lets hackers bypass authorization
https://www.bleepingcomputer.com/news/security/critical-flaw-in-nextjs-lets-hackers-bypass-authorization/
Next.js team fixes vuln that allows auth bypass when middleware is used, revisions documentation recommending this method • DEVCLASS
https://devclass.com/2025/03/24/next-js-team-fixes-vuln-that-allows-authorization-bypass-when-middleware-is-used-hastily-revises-documentation-recommending-this-method/
Next.js and the corrupt middleware: the authorizing artifact
https://simonwillison.net/2025/Mar/23/nextjs-and-the-corrupt-middleware/
Next.js is a React framework for building full-stack web applications, and is so popular that it is downloaded more than 9 million times per week from the package management tool npm . Front-end and full-stack developers use Next.js to build web apps with React, and some of the notable companies using Next.js to build their sites and apps include TikTok, Twitch, Hulu, Netflix, Uber, and Nike.
Next.js versions 14.2.25 and 15.2.3 and earlier had a vulnerability that allowed an attacker to bypass authentication checks in a Next.js application if the authentication checks were performed in the middleware. This vulnerability, CVE-2025-29927, allows an attacker to send requests that reach a destination path without passing critical security checks.
CVE-2025-29927 | Next.js
https://nextjs.org/blog/cve-2025-29927
NVD - CVE-2025-29927
https://nvd.nist.gov/vuln/detail/CVE-2025-29927
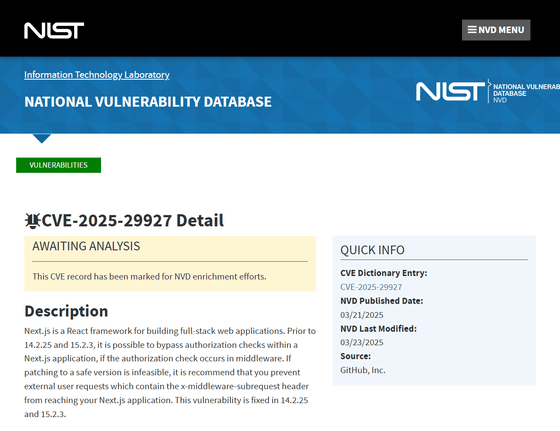
In Next.js, middleware components are executed before requests reach the application routing system, and are responsible for authentication, authorization, logging, error handling, user redirection, geoblocking, rate limiting, etc.
To prevent an infinite loop in which the middleware component itself is re-triggered, Next.js uses a header called 'x-middleware-subrequest' that specifies whether to apply the middleware function. 'x-middleware-subrequest' is retrieved by the ' runMiddleware ' function, which is responsible for processing the incoming request. When 'x-middleware-subrequest' with a specific value is detected, the entire middleware execution chain is bypassed and the request is forwarded to the destination. This means that an attacker can bypass the protection mechanism by manually sending a request with a header with the correct value.
CVE-2025-29927 was discovered by researchers Allam Rachid and Allam Yasser, who said: 'The header and its value act as a universal key that allows us to override rules.'
The Next.js security bulletin states that 'CVE-2025-29927' only affects self-hosted versions using the 'output: standalone' configuration and 'next start'. Next.js apps hosted on Vercel and Nerlify or deployed as static exports are not affected. However, environments where middleware is used for authentication or security checks and validation is not performed later in the application are also affected.
Developers havecommented , 'How could such a vulnerability have been overlooked? It's amazing. Just check if this header exists and ignore the rest of the middleware.' Others have pointed out, 'This really shows how immature the entire JavaScript ecosystem is, and the hype and euphoria around Vercel is making it even more inept.'
To address CVE-2025-29927, Vercel released 15.2.3 as a fixed version of Next.js on March 18, 2025. If you cannot apply this patch, it is recommended that you block external user requests that contain x-middleware-subrequest.
Related Posts:







