Security researchers demonstrate how to crack password management application 'LastPass' where data breach occurred

In August 2022, it was
Cracking encrypted Lastpass vaults | Markuta
https://markuta.com/cracking-lastpass-vaults/
LastPass Security Breach UPDATE: What You Need to Know
https://www.secureblink.com/cyber-security-news/last-pass-security-breach-update-what-you-need-to-know
LastPass data breach leaked Vault backups where users store passwords, company and end-user names, billing addresses, email addresses, phone numbers, IP addresses, source code and other intellectual property has been reported to have Mr. Markta prefaces, ``It is unknown what the stolen data is and how it is encrypted,'' while verifying what the attacker can do with the leaked information. did.
Marcta uses a password cracking tool called Hashcat . The gateway to get the data is the LastPass Chrome extension.
Each extension has a unique ID in Chrome, and the Lastpass extension is assigned the ID 'hdokiejnpimakedhajhdlcegeplioahd'. If you access ``chrome-extension://hdokiejnpimakedhajhdlcegeplioahd/vault.html'' from the address bar in Chrome with the Lastpass extension installed, the login page for your Vault will be displayed. ``You can think of this page as a local site that uses HTML and JavaScript in your browser,'' Markta said. Cracking starts here.
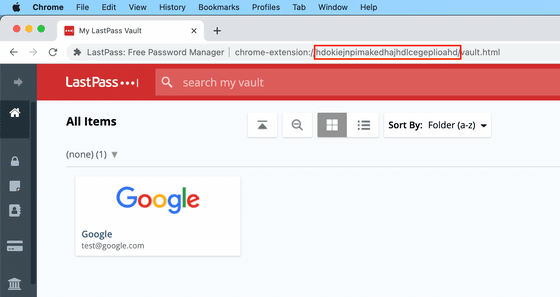
Every extension has its own folder and is stored locally on your system in different locations depending on your OS. On Windows it is '%LocalAppData%\Google\Chrome\User Data\Default\databases\chrome-extension_hdokiejnpimakedhajhdlcegeplioahd_0'.
This folder probably has an SQLite file named '1'. This is where encrypted Vault data is stored and used by the extension. SQLite files can be viewed using tools such as
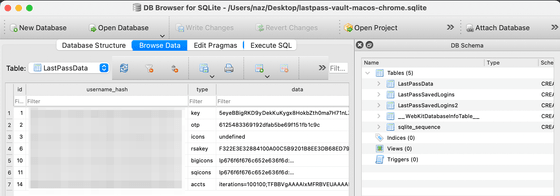
To start cracking Vault passwords using Hashcat, you need three pieces of information: 'Key-Value', 'Iteration count', and 'Account email address'. These should be formatted as 'Key-Value:Iteration count:Email address'.
First, to get the key-value, select where value key in the search column and select the second row in the data column. An example is 'T4vInfZ+6MGDeendq4gvA==' below. This can also be obtained by executing a SQL query. The value you get is base64 encoded, so you can decode it to get the hexadecimal value. When decoded, it becomes '4f8bc89df67ee8c1837847a776ae20bc', which is the key-value.

To get the Iteration count, select where value accts in the search column and search for the first few characters before ';' in the data column. The value obtained is '100100'.
Lastly, the email address is stored in the database as a hashed version, so it should be unknown. But that doesn't matter here, as the aforementioned data breach also exposed email addresses.
Putting all the requirements together, the format would be '4f8bc89df67ee8c1837847a776ae20bc:100100:email address'.
When Mr. Marcta tried to crack the password using the MacBook Air, he succeeded in attacking 1100 times per second and was able to crack the Vault of the account that used a password that could be guessed relatively easily. Although this number of attacks is by no means large, an attacker with an optimized driver can easily reach a speed of about 2 million times per second.
Secure Blink, a security firm that investigated the LastPass issue, said, ``The attacker may have tried to brute force the user's master password and decrypt the exfiltrated copy of the Vault data. With hashing and encryption for protection, even attempting to brute force guess your master password will be difficult, especially for customers who adhere to password best practices.LastPass is the latest in password cracking. 'We regularly test our technology against our own algorithms to improve our cryptographic controls,' he said. said.
Related Posts:
in Security, Posted by log1p_kr