On the actual analysis speed of "Pyrit" to break through WPA / WPA 2-PSK in wireless LAN and self-defense measures

A method of trying all kinds of passwords by brute force is called "Brute force attackIt is said,Free open source software which finds passwords by analyzing WPA / WPA 2 - PSK of wireless LAN with GPU at ultra high speed "Pyrit"The method adopted by that is exactly the brute force attack itself. Therefore, it is not a bug of the wireless LAN encryption mechanism bugs and security holes, but in a sense meaning that if time goes by, it will be able to break through at some point "a powerful attack".
So how fast will it actually take? In the year 2008, there was an entry mentioned on the official blog of "Pyrit" about the anxious point.
The twilight of Wi-Fi Protected Access(Meaning like even the beginning of the twilight of wireless LAN security)
http://pyrit.wordpress.com/the-twilight-of-wi-fi-protected-access/
First of all, for the general public, unless there is a strong reason to do so, there is a tendency to use the easiest and cheapest thing for passwords, for example, in the case of MySpace which was the world's largest social network until Facebook was pulled out , It was said that it was necessary to enter a single letter without fail, and it seems that most of the accounts which had been broken by 34,000 had only added "1" to existing English words.
Likewise, in the case of WPA / WPA 2 - PSK, it is the strength until "the kind of password is set" is passed through as it is, and the combination of PMK (Pairwise Master Key) By calculating in advance, it will be possible to break through from a few minutes to several weeks. If it is a password that can break through in just a few minutes, the attacker would think to attack, and conversely if it takes several weeks, the possibility of thinking realistically and giving up the attack is high.
For example, NIST (National Institute of Standards and TechnologyIn the document created byDiscussion on the quality of passwordsAccording to it, "For example, if the user considers an 8-character password by himself, the entropy (extent of randomness) falls within the range of 18 to 30 bits depending on how it is selected "This is equivalent to two words randomly selected from randomly chosen three bytes or five randomly chosen upper case alphabetical letters or randomly selected 4000 words", "This entropy Is much lower than the level normally considered safe as an encryption key. "
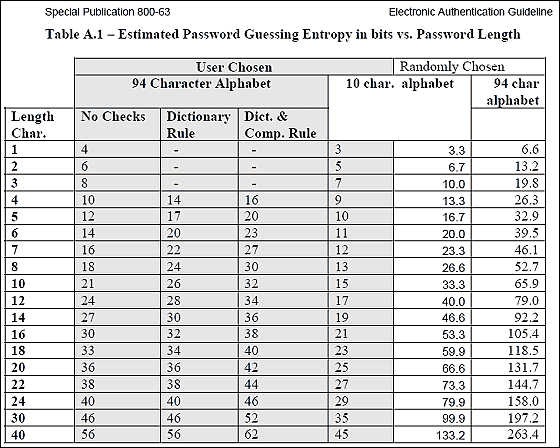
In short, if you have an 8-character password and 32-bit randomness, it will take about 3 billion roundtrips to break through with a 50% chance , Unless you are careful about security, you can not get this strength.
In the original machine power where the WPA / WPA 2 of the wireless LAN was made, it can only totally hit less than 100 times per second, theoretically it will take about 2 years in the case of WPA-PSK to break at a probability of 50% It was supposed to be. On the other hand, in the case of "Pyrit" using this GPU, by raising the speed up to about 100 times that assumed at that timeShorten the time to break through with a 50% chance from 2 days to 3 dayscan do.
Actually 30 placesESSIDIn order to break through all the wireless LAN with a probability of 50% assuming that the access point of the wireless LAN by existence, in the conventional machine (PC with the price of about $ 800 = about 65,000 yen), 30 It takes about 28 years to calculate total of 90 billion times at 30 places, it takes about 28 years and within 7 days if you can prepare a machine costing 1.2 million dollars (about 97.6 million yen) You can break through. However, once this master key is broken in the same wireless LAN with ESSID, this key is shared with each ESSID of the same name, so you can re-break through the broken master key.
For example, in the above calculation example,
ESSID "linksys": 17 places
ESSID "NETGEAR": 7 places
ESSID "default": 3 places
ESSID "wlan": 2 places
ESSID "WiFI": 1 place
In this case, if the total number of "linksys" is more than 30, the remaining 16 ESSIDs "linksys" will also be used by spending.
By using a single GPU, "Pyrit"CUDAFor a computer with $ 1,300 (equivalent to about 105,000 yen) available, the size of HDD required for 15 billion calculations is 600 GB ($ 3,000 for 2008 price = about 240,000 yen, if nowAbout 5680 yen at 640 GB), And this time can be reduced to 2 weeks or so. It is possible to shorten it to the cost of 1/800 at the speed of 1300 times or more the computing speed of the PC which WPA which was the security of wireless LAN was supposed at the beginning. To make the probability of breakthrough from 50% to 99% this cost six times this is needed. Nevertheless it is still about 20,000 dollars (about 1.62 million yen), once thinking that it was necessary to do the same thing, 8 million dollars (about 650 million yen) was necessary, considerably realistic There is a crisis right in front of me right now.
In addition, the above calculations are essentially "2008", and as of the year 2011 when three years passed since then the power of the machine has further increased.
The author of "Pyrit" warns about this in an entry meaning "three years ago" "the beginning of the twilight of wireless LAN security", and due to the evolution of the hardware of the personal computer, until now the theoretical "unexpected" The crisis, which was only a momentum, is now changing to a crisis there. Not "WEP is OK because it is not WEP!" But "WPA / WPA 2 is not safe unless you have properly set your password"about it.
The author of "Pyrit" is the official blog "About"This software" Pyrit "does not encourage or support breaching the security of people using wireless LAN, but it is the main incentive to recognize and discuss such technologies to the last , And we are doing. Therefore, this "Pyrit" is provided free of charge as open source so that anyone can study.
Also, there is already software for Windows that uses GPU at a fee to break through wireless LAN WPA / WPA 2-PSK at ultra high speed brute force.
Elcomsoft Wireless Security Auditor
http://www.elcomsoft.com/ewsa.html

The price is about 50,000 yen for Standard Edition and about 159,000 yen for Professional Edition. Professional Edition can use up to 32 CPUs and up to 8 GPUs can be used simultaneously .
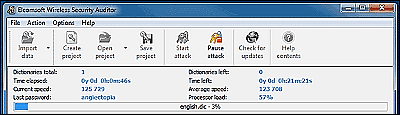
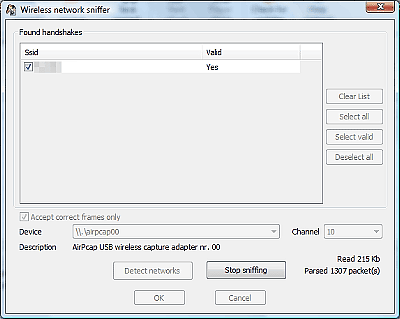
So, how to defend yourself, this means that you simply set the password with a high entropy (degree of randomness) to the maximum length, not a short number of characters. No matter how long a password it is, it is useless that "Maximum length 63 letters are all" 1 ". In the blog below I will explain how to make such a random password specifically.
Hidekiy blog: [crypto] How to protect wireless LAN network from attack by Pyrit
http://blog.hidekiy.com/2011/07/crypto-pyritlan.html

The SSID stealth function and the MAC address limited connection function can be ignored since they have no meaning except for the mood like countermeasures. In WPA 2 - PSK (Personal), the only biggest resistance measure is made only by setting a sufficiently strong pre - shared key (PSK).
How to make such a key is affordable, if you execute the openssl command attached to OpenSSL with the rand option, you can get a character string made from a cryptographically secure random number derived from the OS random number generator I will.
$ Openssl rand - base 64 100
PyPTFpJyRrj94 + AzhVKqs4ipUbZXJ7 / RCefcAbk9mEiPr8H78tsVjUaLDOvT1OmP
QYkZGqdGfc2Ng0UmCZFFE4FgYuphU9uTb5hXzV5FM6vmbfi8cMmKC6aoCzDx7h01
KuFi 9 g ==
The output is binary string by default, so I added the -base64 option and encoded it with Base64. If you use this as the preshared key's ASCII specification maximum length of 63 characters, it will be 6 bits * 63 = 378 bits, which is sufficient strength.
Caution
The pseudo random number that can be created with the rand () function of C language has no clutter of random type (long 64 bit) or more, so you should not use keys derived from it.
Conclusion
Do not use weak keys that are divided by brute force by dictionary or combination generation. As a matter of operation of the encryption key, unless the function of the encryption itself is demonstrated, protection is done much weaker than the design, and it loses the attack. In the next specification of WPA 2, the wireless LAN router should refuse to use a short key of 20 characters or less as a preshared key.
Also, more realistic calculations are done on the above blog, the time it takes to examine all the 8 letters of the alphabet lowercase letters is 2.4 days,If you examine half, the possibility to find the key will be 50%, so you can break it by an average of 1.2 daysIt is said.
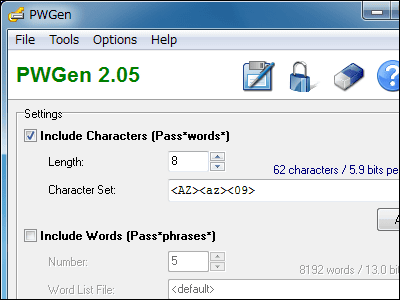
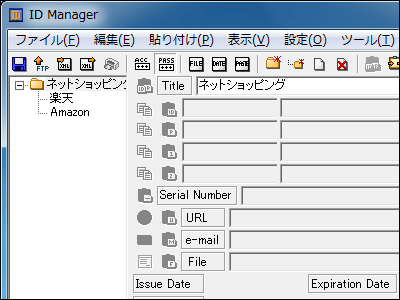
Therefore, instead of at least "password I thought", the password made up of a randomly generated combination of alphanumeric characters is used as the minimum line (password generation special software "PWGen"And record a combination of ID and password"ID Manager"Password generation function, etc.), and if possible, you should generate and use a password with a very high degree of randomness as described above.
"PWGen" free software which can generate a large amount of passwords and pass phrases suitable for the condition by easy operation
"ID Manager" free software that can manage easily the troublesome ID and password that troubles the head at once
If the password of the wireless LAN is long, input may be extremely troublesome, but it is clearly said that it is a problem of "accustomed".
In addition, breaking the wireless LAN password itself has no legal penalty and if it intrudes illegally into the password protected network, "Act on Prohibition of Unauthorized Access Act"(There is an opinion that analysis of the password itself is a crime if it is a purpose of plagiarism in violation of Article 109 of the Radio Law, but as a practical matterThe opinion of the Ministry of Internal Affairs and CommunicationsIn fact, it becomes the direction of Article 59 of the Radio Law, and since it is known only by the eventually executed action whether or not the password was deciphered for use for unlawful access from the beginning, the actually analyzed password is used for unauthorized access It is true that it can only be judged by whether it is or not). Therefore, regarding the use of "Pyrit" demonstration demonstration that breaks through the experimental wireless LAN set by oneself for those who do not know the meaning of confirming the strength of their wireless LAN or strengthening the wireless LAN password Let's use it only for security research / enlightenment / discussion such as doing.
Also, even if you do not have a PC with a powerful GPU at hand, you can use a cloud environment like Amazon EC 2, if you can communicate from anywhere anytime, you can afford a machine with powerful GPU reasonably Because it can borrow and use at a price, it is not a convenient belief that it is not possible to carry around with a machine equipped with a high-performance GPU as a realistic crisis , It is the most reliable countermeasure to immediately improve the security of my wireless LAN.
Related Posts: