Google succeeds in breaking the hash function "SHA-1", and the method will be released after 90 days
A cryptographic hash function used in TLS / SSL, OpenPGP, etc.SHA-1To break Google, the NetherlandsCWI studyIt succeeded. As SHA - 1, which had been pointed out as "possibly being broken in theory", has actually been broken, it seems that shifting to a safer hash algorithm has become essential.
Google Online Security Blog: Announcing the first SHA 1 collision
https://security.googleblog.com/2017/02/announcing-first-sha1-collision.html
SHAttered
http://shattered.io/
It was CWI and Google that succeeded in breaking "SHA-1". He said that he succeeded after two years of research.

The technical idea of SHA - 1 put into practical use about 20 years ago is to use a general hash function as a technology to secure the authenticity of digital data. It is "hash value" that can convert the digital data with the hash function and you can not restore the digital data from the hash value. It has the feature that it can be converted from data to hash value only in one direction and the hash value becomes unique value depending on data. Therefore, by checking that the hash values are consistent, it is possible to detect that the data has been tampered with or replaced during the data transmission process.
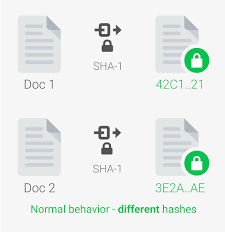
When Doc 1 and Doc 2 have different contents (different data), the hash values converted by SHA-1 are different eigenvalues. The technical feature of a hash algorithm such as SHA - 1 is that the hash value takes only one eigenvalue.
However, in 2005, researchers reported that the same SHA-1 hash value can be calculated from different data, and in 2012 the paper which Marc Stevens outlined the theoretical approach "(PDF file)Cryptanalysis of MD5 & SHA-1It has been pointed out that SHA-1 has vulnerability, such as announcing. This attack is called "SHA-1 collision" attack, which greatly shakes the reliability of SHA-1.
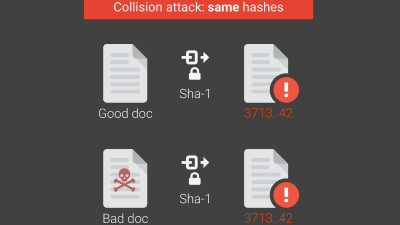
Using the SHA-1 conflict, you can return the same hash value by calculating the hash function on SHA-1 from the special processed "bad doc 1" and "bad doc 2". In other words, different data that returns the same hash value can be created, so it is possible to alter the contents during data transfer or replace them with another data.

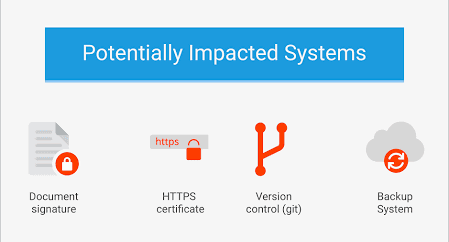
If the SHA-1 conflict is exploited, the technology that has confirmed the authenticity of data using SHA-1, such as digital signature, SSL, git version control system, backup system, can not maintain data identity I will. Since the existence of this SHA-1 conflict is called out, there is a call for a transition to a hash algorithm such as SHA-256 which is more secure, for example, Google used SHA-1 in the browser Google Chrome in 2014 We have advanced countermeasures such as terminating support for certificates.
Although the possibility of the theoretical system breakthrough was screamed, in the present situation that contents using SHA - 1 are still in the world, Google and CWI are the first in the world to actually cause SHA - 1 collision . In addition, Google has published two PDF data that were modified to use SHA-1 collision, so that anyone can check SHA-1 conflicts.
A document in which one is called "SHAttered" in blue. If you click the image, the PDF file will be displayed.

Another document is red and "SHAttered". The hash value for calculating these two PDF files with the SHA-1 hash function will be the same.

According to Google, calculations necessary for SHA-1 collision can be made using high expert knowledge and Google cloud infrastructure. In order to show how huge the computational complexity is, it is necessary to calculate over 900 Kyo times in all, if you do it with CPU in the first phase, it will be 6500 years, the second phase will be 110 years It expresses it to take.

GoogleVulnerability disclosure policyAs stated, "I will release the code to use SHA-1 collision attack 90 days later". Therefore, after 90 days, everyone can see the contents of the SHA-1 collision attack, so that the transition to a safe method is forcibly pushed forward by all contents using SHA-1 It is a prospect. Google hopes that the industry will be convinced that shifting to a safer way like SHA - 256 is an urgent matter as a way to actually break through SHA - 1 will be made public. " I'm giving a comment.

Related Posts: