Windows password can be broken in about 6 to 6 hours if 25 GPUs are used, and is a method capable of collecting 350 billion as many rounds per second?
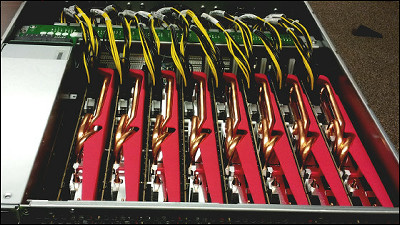
A system of cracking using a GPU cluster which can break Windows passcode used in a general company within 6 hours, was developedArs TechnicaIt reports.
25-GPU cluster cracks every standard Windows password in 6 hours | Ars Technica
http://arstechnica.com/security/2012/12/25-gpu-cluster-cracks-every-standard-windows-password-in-6-hours/"
It was CEO of Stricture Consulting Group that developed this systemJeremi M GosneyMr. and was held in Oslo, NorwayPasswords ^ 12 conferenceI announced the details in.
Mr. Gosney's slide (PDF file)There is no doubt that a machine with high computing power is required for cracking the password, so it is quite powerful even with one GPU, but it is much better if there are a lot.
However, attempting to strengthen one computer to obtain powerful machine power will also hit the constraints imposed by the motherboard, BIOS, and driver. Therefore, he seems to decide to use virtualization technology to handle multiple machines like one machine.

So, you can treat multiple remote GPUs as if they are localOpen CLWe are using the system to build.

The real thing of the machine he made is as follows.
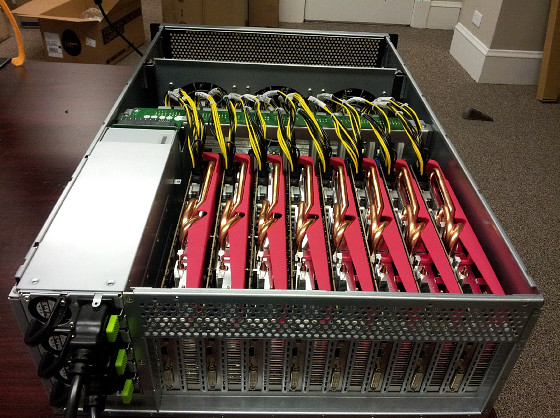
I used them side-by-side in a rack like this.

This system consists of five servers and has 25 AMD Radeon graphics cards. Using the Linux-based OpenCL cluster platform, it is possible to behave as if multiple graphics cards are running on a single computer. Also, what is running on the system is free password-cracking software optimized for GPU computing "Ocl-Hashcat PlusFor various password algorithmsBrute force attack(Brute force attack) andDictionary attackYou can get on.
The back side of the rack looks like this.

This system can input (guess) 350 thousand different passwords per second, and seems to be able to break Windows passcode used in common companies with almost unprecedented speed. As a result, Microsoft has adopted it from Windows Server 2003NTLMIt is possible to break through in 6 hours if you start a brute force attack that includes upper case letters, lower case letters, numbers, and symbols. Also, it seems that the LM algorithm used by many companies to maintain compatibility with older versions of Windows will break through in just 6 minutes.
I saw the machine up.

According to Mr. Gosney, "With this system all the things that you can do with Hashcat are all possible as well, and you can run it at tremendous speed." He used to build a system with four "AMD Radeon HD 6990" machines that can provide about 88 billion inputs (guesses) per second to NTLM, but this time the new model is 4 times faster It is becoming.
So although the development of GPU computing has improved the speed of password cracking offline, there was a limit in performance because of limitations on GPUs that can be used on a single computer. However, by using VCL virtualization, it became possible to use countless GPUs, so a breakthrough was opened for further cracking speed up.
· Added 2015/12/16
"OclHashcat" and "Hashcat" which inherited the function of "ocl-Hashcat Plus" that appeared in this article have been made open source.
Hashcat Is Now Open-Source - Phoronix
http://www.phoronix.com/scan.php?page=news_item&px=Hashcat-Open-Source
Details and download of software is from the following.
Hashcat - advanced password recovery
https://hashcat.net/hashcat/

OclHashcat - advanced password recovery
https://hashcat.net/oclhashcat/

Related Posts:
in Hardware, Posted by darkhorse_log