I tried using 'Cover Your Tracks' which allows you to check what kind of information is collected from the browser for free

Since the PC configuration and installed fonts are slightly different for each user, it is said to be a '
Cover Your Tracks
https://coveryourtracks.eff.org/
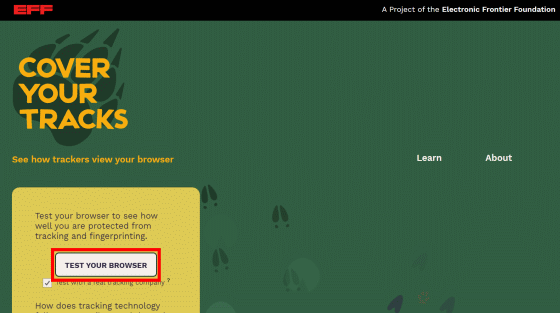
The top screen of Cover Your Tracks looks like this. The logo mark is on the upper left, the test start button is on the lower left, and the link to the page to learn about fingerprints and the link to how to use Cover Your Tracks are displayed on the right. In addition, Cover Your Tracks is an update of Panopticlick that allows you to see how much your browser is protected from tracking, which was previously published by the Electronic Frontier Foundation , and you can know more about fingerprints than Panopticlick. You can do it. Click 'TEST YOUR BROWSER' immediately to see how many fingerprints are collected in your browser.
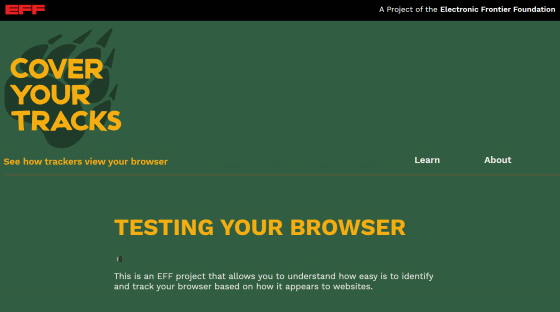
When you click 'TEST YOUR BROWSER', 'TESTING YOUR BROWSER' will be displayed as shown below. Wait for a while until the test is completed.
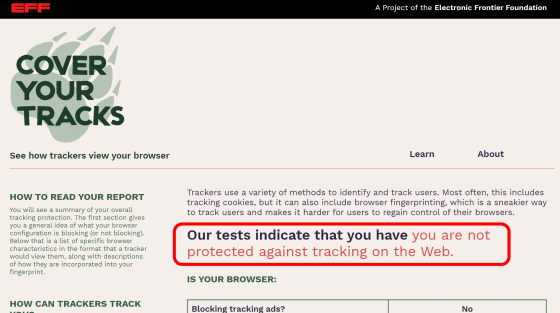
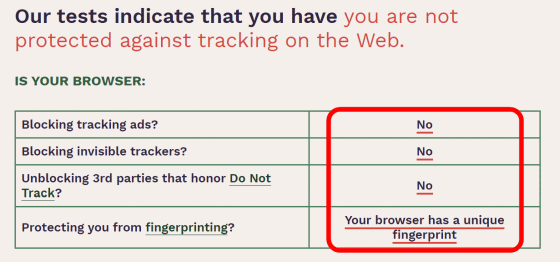
The results will be displayed when the test is complete. This time I tested it with Microsoft Edge version 87.0.664.41 without adding any extensions, but the red frame shows 'You are not protected from tracking on the web'. It was.
Scroll down to see detailed results. From top to bottom, 'Is the browser blocking tracking ads?' 'Is the browser blocking invisible trackers?' 'The browser is a third-party with Do Not Track. It says 'Unblocking 3rd parties that honor Do Not Track?' And 'Protecting you from fingerprinting?', All of which are 'not done' in Microsoft Edge. '(No)' or 'Your browser has a unique fingerprint' is displayed.
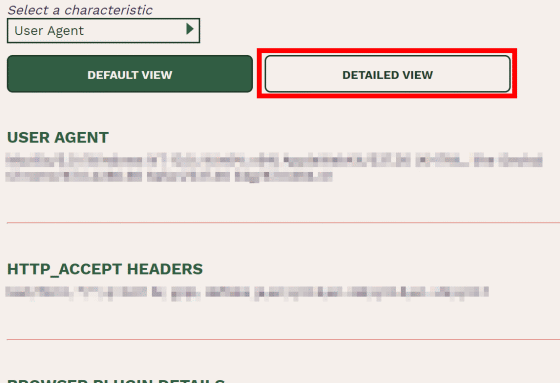
You can see the collected information by scrolling further down. By default, only the name and content of the fingerprint is displayed, so click 'DETAI LED VIEW' to see more detailed information.
Now, the contents and features of each information are displayed.
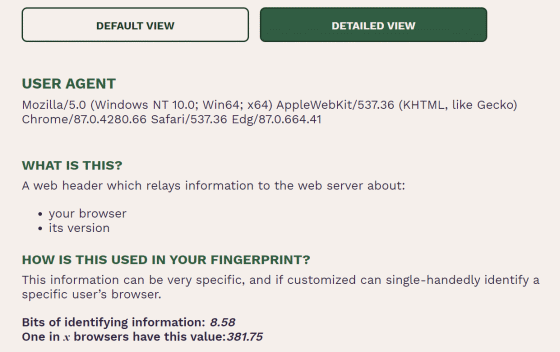
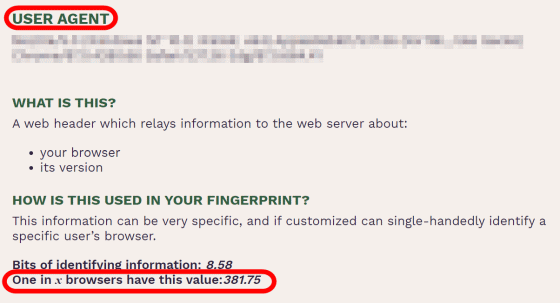
Let's look at each information in order from the top. First of all, 'USER AGENT'. The user agent
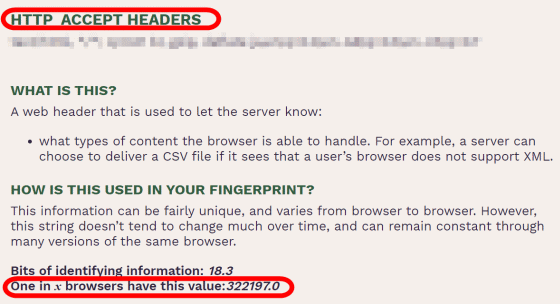
'HTTP
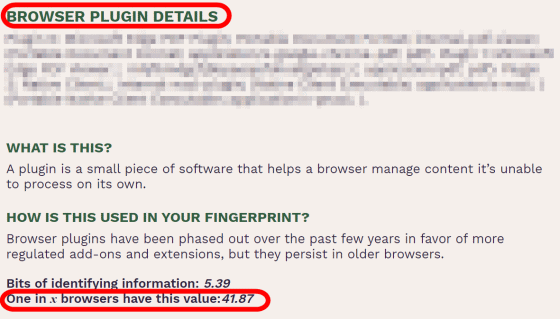
Next is 'Plug-in installed in the browser (BROWSER PLUGIN DETAILS)'. This time, I didn't put any extensions in Microsoft Edge, so the number was relatively low at '41.87'. If you have installed some extensions yourself, it will be easier to identify you personally.
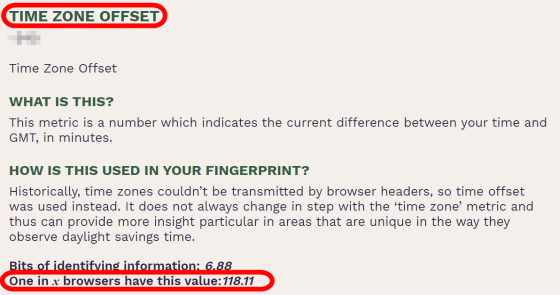
'TIME ZONE OFFSET' is a value that represents the time difference between the international standard time and the user's PC. By knowing this value, it is possible not only to infer which country the browser user is in, but also to infer a more detailed position in areas with daylight saving time.
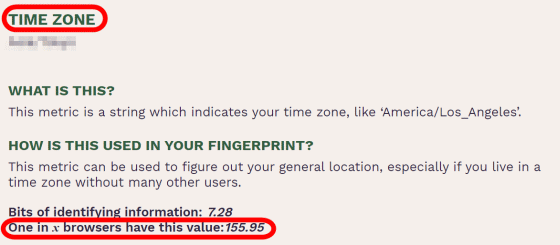
'TIME ZONE' is a character string that represents the time zone of a user such as Asia / Tokyo.
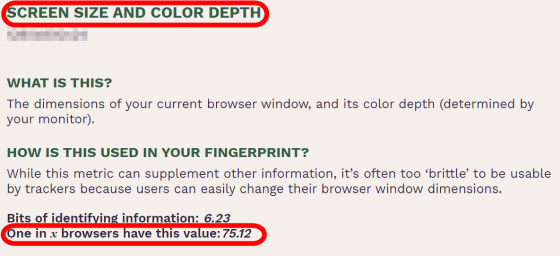
'SCREEN SIZE AND COLOR DEPTH' is information that varies depending on the user's display. Since this value changes when the browser window size changes, it is rarely used to identify the user.
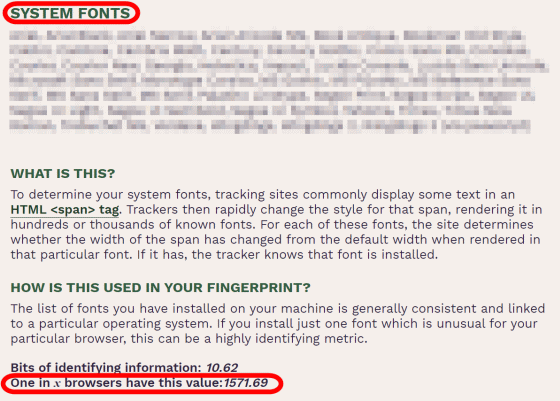
As the name implies, 'SYSTEM FONTS' is information about fonts installed on the user's system. It's not a lot of information if you don't have any new fonts installed, but if you have some unusual fonts installed, this information can be a great clue to identify an individual.
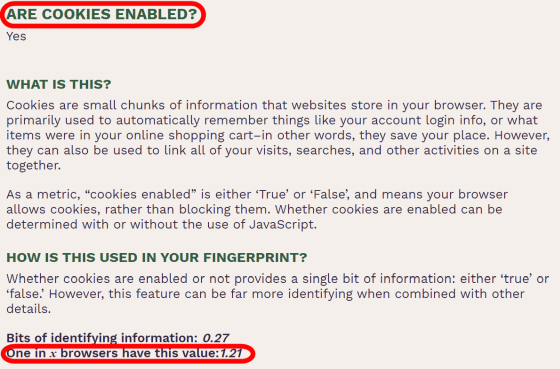
The information 'whether cookies are valid or invalid (ARE COOKIES ENABLED?)' Does not seem to be worth it by itself, but it can be used in combination with some information to help identify an individual.
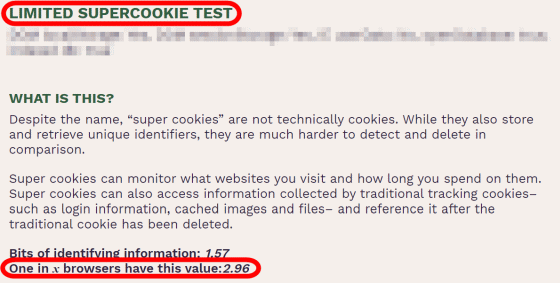
'HASH OF CANVAS FINGER PRINT' is a hash value generated by using the 'canvas' element of HTML5, and this value depends on the graphic board installed in the PC, OS, installed fonts, etc. to change. Therefore, this information is very useful for identifying individuals.
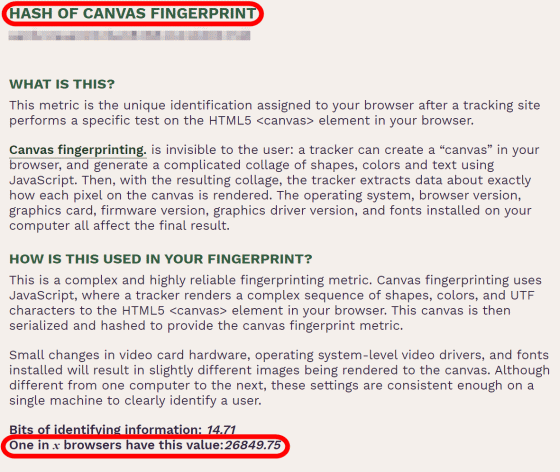
Like the 'canvas hash value', the 'WebGL hash value (HASH OF WEBGL FINGER PRINT)' is a value that changes depending on the PC configuration, and is useful information for identifying an individual.
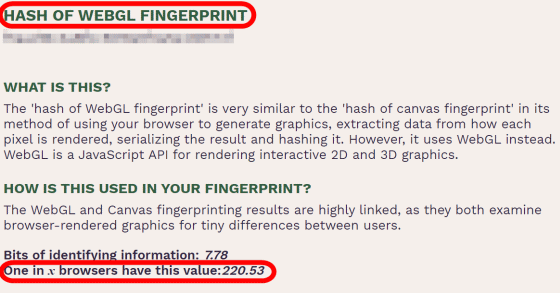
'WEBGL VENDOR & RENDERER' is the information that the browser conveys to the server when drawing graphics using WebGL, and the value varies depending on the graphic board used by the user.
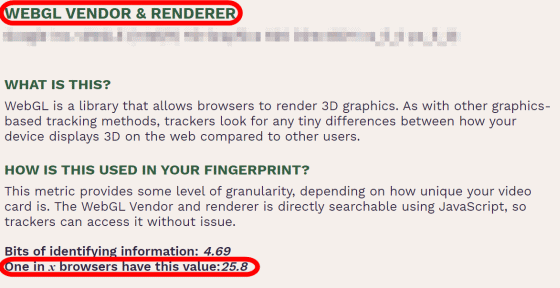
'DNT HEADER ENABLED?' Is the header that the browser sends to the server. The DNT header is either unset or set to '1', but it is very rare for the DNT header to be set to '1' and if it is set to '1' It may identify an individual.
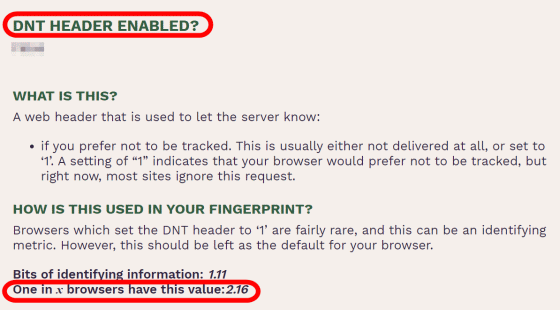
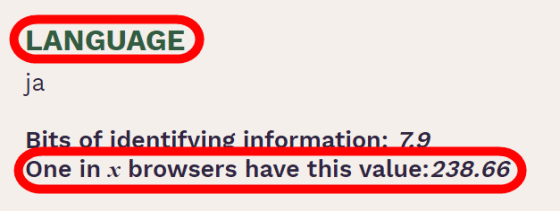
'Language (LANGUAGE)' represents the language setting of the browser.
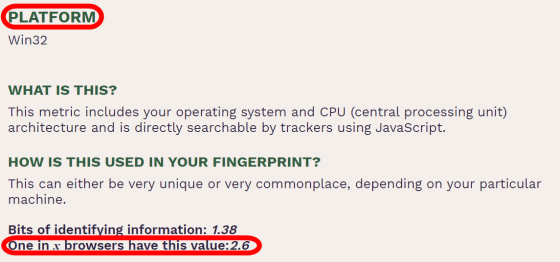
'Platform' indicates the OS used by the user, and if you are using a rare OS, it can be information that identifies an individual.
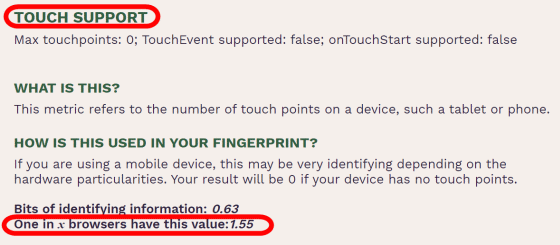
'Touch SUPPORT' indicates the number of touch points supported by the terminal used by the user. This time, the value is 0 because a PC that does not support touch operation is used, but it can be an element that identifies an individual when accessed with a smartphone or tablet with a special number of touch points.
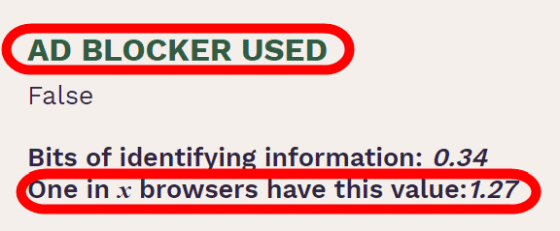
Information that can be answered 'yes' or 'no', such as 'Are you using ad blocking (AD BLOCKER USED)', may not seem very valuable at first glance, but it can be combined with a lot of information to personalize an individual. It leads to identification.
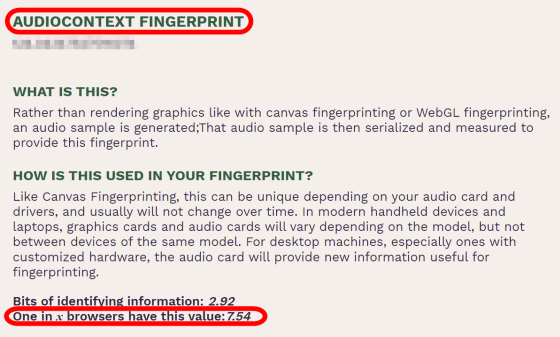
The 'AUDIO CONTEXT FINGER PRINT' is information that can be collected when generating audio, and like the 'canvas hash value' and 'WebGL hash value', it has different values depending on the PC configuration.
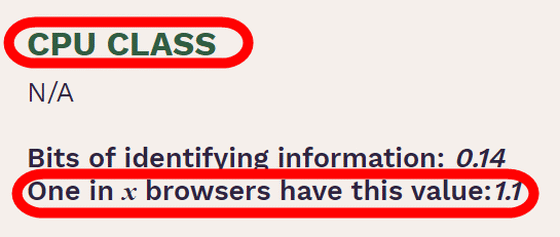
'CPU CLASS' is a fingerprint to get the name of the CPU used by the user, but in this test it was displayed as 'Not applicable (N / A)'.
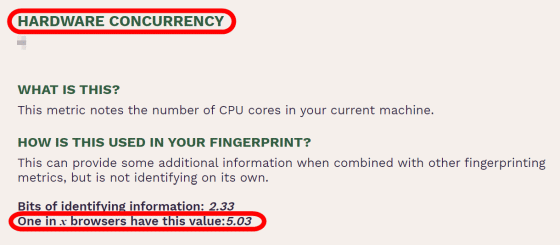
'Hardware Concurrency (HARDWARE CONCURRENCY)' is information that represents the number of threads of the CPU used by the user.
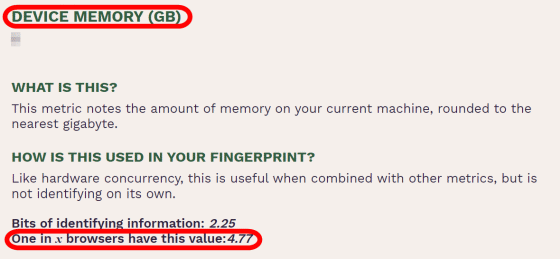
'Device memory (DEVICE MEMORY (GB))' indicates the amount of memory installed in the device used by the user.
In this way, various information is collected and individuals are identified just by accessing the website, but in order to prevent the collection of fingerprints, the Electronic Frontier Foundation installs add-ons that interfere with tracking such as
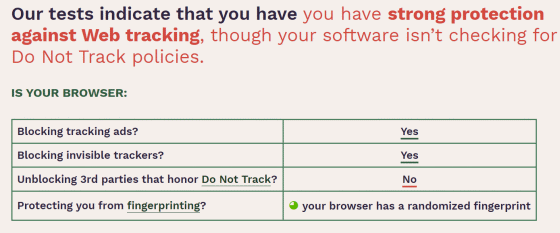
The image below shows the result of running the Cover Your Tracks fingerprint test on Brave. Not only was we able to block tracking ads and invisible trackers, but we were also able to randomize fingerprints. Brave is recommended for people who want a quick way to avoid tracking, as it allows you to randomize your fingerprints just by installing them without any configuration.
Related Posts:
in Review, Web Application, Security, Posted by log1o_hf