Malware ``SourMint'' that steals personal information of iPhone users and replaces advertisements displayed

Security company
SourMint: malicious code, ad fraud, and data leak in iOS | Snyk
https://snyk.io/blog/sourmint-malicious-code-ad-fraud-and-data-leak-in-ios/
iOS ad developer kit reportedly steals click revenue, harvests user data | Appleinsider
https://appleinsider.com/articles/20/08/24/ios-ad-developer-kit-reportedly-steals-click-revenue-harvests-user-data
According to Snyk, 'SourMint' was discovered in China's mobile ad platform provider Mintegral's iOS advertising SDK in July 2019. SourMint logs URL-based requests made through apps that use the Advertising SDK, records user activity, and may steal personally identifiable information and other sensitive information. SourMint also points out that user fraudulently reports ad clicks by users, stealing potential revenue from competing ad networks, app developers, and ad publishers, Snyk noted.
The following movie is a movie demonstrating how SourMint, a malware installed in the advertising SDK Mintegral, actually steals information.
A demonstration of the SourMint Malicuous SDK from Mintegral-YouTube
According to Snyk, Mintegral's advertising SDK has been downloaded over 300 million times a month and is used by over 1200 iOS apps. By using this ad SDK, developers can easily embed ads in apps without coding, and monetize apps easily. In addition, Mintegral provides free advertising SDK not only for iOS but also for Android, but it was only the iOS version of the SDK that the existence of malware was revealed at the time of article creation.
According to Snyk, there is a malicious feature that waits for users who use apps that use SourMint's advertising SDK to tap ads that do not belong to Mintegral's ad network. When a user taps an ad, the SDK takes over the process of displaying the ad and presents the Mintegral ad to the user.
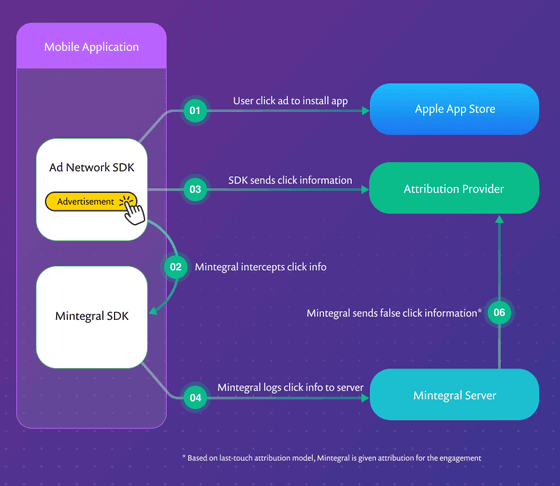
'Interestingly, Mintegral's advertising SDK seems to be designed to prevent researchers from discovering the true behavior behind the app, and it includes a lot of anti-debug protection,' Snyk writes. .. It seems that the malicious code has a specific routine to determine if the smartphone is rooted, and if evidence is found that it is being monitored, the SDK modifies its behavior to hide the malicious behavior. That. This behavior seems to prevent malicious behavior in the Advertising SDK from getting caught in Apple's app review process.
SourMint also captures all URL-based requests made within your app using Mintegral's Advertising SDK, so you can see not only the requested URL, but the authentication token and other sensitive information, as well as your app's code. It is possible to steal things that help identify user patterns, as well as device identifiers ( IDFAs ), IMEIs, etc., that are generated with unique random numbers used to identify devices.
In addition, Apple is in consultation with the security researcher of Snyk, and advertising SDK of Mintegral is not information is obtained that has had a real harm to the user says you have. Apple announced an update focused on privacy and security in iOS 14 in the second half of 2020, which explains that one of the reasons is that ``third party SDK may incorporate malicious functions''. ..
Related Posts:






