Google pointed out that “sites that exploit the vulnerability of iPhone have stolen personal information for two years”

by
Google's cyber security research team “ Project Zero ” reports that it has discovered a number of malicious websites that can secretly hack iPhones.
Project Zero: Implant Teardown
https://googleprojectzero.blogspot.com/2019/08/implant-teardown.html
Project Zero: A very deep dive into iOS Exploit chains found in the wild
https://googleprojectzero.blogspot.com/2019/08/a-very-deep-dive-into-ios-exploit.html
Malicious websites were used to secretly hack into iPhones for years, says Google | TechCrunch
https://techcrunch.com/2019/08/29/google-iphone-secretly-hacked/
In 2019, a threat analysis group (TAG) within Google's Project Zero discovered several websites that were hacked by malicious attackers. These websites seemed to have indiscriminately performed “ watering hole attacks ” against site visitors using the zero-day vulnerability that existed in the iPhone.
A group of hacked websites indiscriminately attacks visitors, and by accessing these sites, the exploit server attacks the device, and if the attack is successful, malware is installed to monitor the device. The The hacked site seems to have been accessed by thousands of users a week.

by
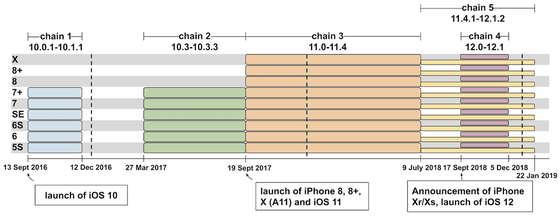
According to TAG, the attack on the hacked site is attacking almost all versions of iOS from iOS 10 (released in September 2016) to iOS 12.1.2, and it is an Apple genuine web browser There were 14 vulnerabilities in total: 7 vulnerabilities related to Safari, 5 vulnerabilities related to the kernel, and vulnerabilities bypassing the 2 sandboxes . TAG says, “This attack suggests the existence of a hacking group that continues to hack iPhone users in a particular community and has been attacked for at least two years.” .
TAG has identified vulnerabilities exploited by malicious hacked websites and reported them to Apple's software development team. It seems that these vulnerabilities existed in code that did not work properly, code that skipped QA , code that was rarely tested or reviewed before implementation. The attacker obtained the root privileges of the terminal using multiple vulnerabilities and was able to install malicious applications etc. secretly.
Malicious hacked websites seem to have attacked users' terminals mainly using 5 types of exploits. The vertical axis of the following graph shows the attacked terminal, the horizontal axis shows the iOS version and exploit type that were attacked, and the horizontal axis shows the attack The time when it was passed is shown.
According to Project Zero's analysis, exploits used by malicious hacked websites were also used to steal photos and messages on user devices and track location information in near real time. The exploit was also able to access the area where user passwords are stored.
The zero-day vulnerability used by malicious websites that were hacked seems to have been fixed by iOS 12.1.4 delivered on February 7, 2019.
Apple has increased the reward paid to security researchers who discovered vulnerabilities that can gain root privileges to $ 1 million (about 110 million yen). The new bounty program is scheduled to take effect in late 2019. Since Project Zero has discovered multiple vulnerabilities in the exploit chain, Google is eligible to receive a bounty worth several hundred million yen.
Related Posts:
in Software, Smartphone, Security, Posted by logu_ii