It turns out that more than 2.8 million Android smartphones are using Chinese firmware with root kit

Popular in the United States such as BLUIncludes an application that sends cheap Android smartphones without the permission of sending personal data such as user's call history and text to Chinese serversIt became clear that, furthermore, no longerRoot kitIt turned out that the program to be called was put in many smart phones.
Vulnerability Note VU # 624539 - Ragentek Android OTA update mechanism vulnerable to MITM attack
https://www.kb.cert.org/vuls/id/624539
Powerful backdoor / rootkit found preinstalled on 3 million Android phones | Ars Technica
http://arstechnica.com/security/2016/11/powerful-backdoorrootkit-found-preinstalled-on-3-million-android-phones/
Security survey company BitSight revealed that there are 2.8 million terminals on Chinese Android smartphones that use firmware that includes a rootkit that can run software freely after acquiring root authority. This firmware was manufactured by Ragentek of China, and in the United States a lot of such devices are sold as inexpensive Android smartphones.
According to BitSight and its subsidiary Anubis Networks, Ragentek's firmware attempts to run software with root privileges, bypassing the security protection features included in the Android OS,Man-in-the-middle attackIt is said that it contains the dangers of being used for.
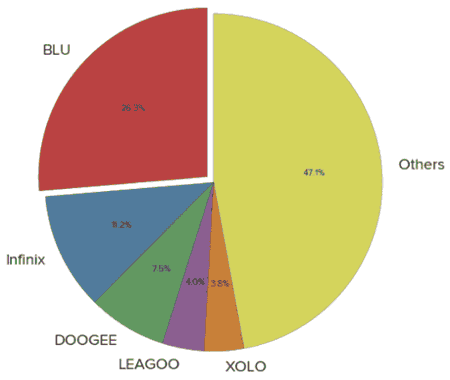
BitSight also discloses the breakdown of manufacturers of more than 2.8 million handsets, and the largest proportion of 26% is the terminal of the American company BLU. Then it is 11% of Infinix, 8% of DOOGEE, 4% of LEAGO and XOLO.
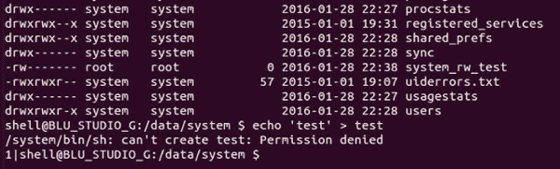
BitSight has purchased a BLU "Studio G" smartphone at Best Buy and succeeded in installing an application named system_rw_test using the backdoor included in the terminal, which means that the problematic route It is confirmed that the terminal with the kit is sold.
According to BitSight's survey, the number of vulnerable terminals is the largest in the United States as a result of indexing from the target terminal's IP address. Also, BitSight's security researchers have tweeted that they are checking connections such as healthcare, government agencies and banks.
@ Dangoodin001We're seeing lots of connections coming from all sorts of sectors, including healthcare, government and banking. Scary stuff.
- João Gouveia (@ jgouv)November 18, 2016
By checking whether it is communicating with the following domain related to Ragentek firmware, BitSight says it can check whether there is vulnerability or not.
"Oyag [.] Lhzbdvm [.] Com"
"Oyag [.] Prugskh [.] Net"
"Oyag [.] Prugskh [.] Com"
We already know that Ragentek firmware is used for 2.8 million terminals even by just the already found out, and it is expected that the number of target terminals will increase in future surveys. In addition, this time only the terminal circulating in the United States to the last, it is thought that the Ragentek firmware is used for many more terminals globally.
Related Posts:
in Hardware, Software, Smartphone, Security, Posted by darkhorse_log