Discovered the presence of 20 types of apps that put malware as unknown to the application on the Google Play store, the reoccurrence of malware "HummingBad" that won in 2016

ByPortal gda
Develop security related softwareCheck PointAccording to Malware that is a derivative of "HummingBad" malware that had inflicted about 300 million yen per month by infecting about 100 million terminals in 2016,HummingWhale"Was spread through the Google Play store. Distribution of the application has already stopped, but if infected with this malware, the virtual machine will be launched inside the terminal, it will continue to generate advertisement revenues illegally, and it will be possible to do an action of appreciating good reputation by reviewing the application without permission It has been made clear.
A Whale of a Tale: HummingBad Returns | Check Point Blog
http://blog.checkpoint.com/2017/01/23/hummingbad-returns/
Virulent Android malware returns, gets> 2 million downloads on Google Play | Ars Technica
http://arstechnica.com/security/2017/01/virulent-android-malware-returns-gets-2-million-downloads-on-google-play/
HummingBad, which Check Point announced its existence in July 2016, infects up to 85 million Android phones and improperly increases the number of accesses to mobile advertisements, thereby generating $ 300,000 (about 30 million It was a malware that raises profits of yen). This malware is installed in the installed terminalRoot kitIt is thought that we had earned income by setting up advertisement fraud or making illegal installing applications.
"HummingBad" made in China that infects 85 million Android terminals and makes 30 million yen a month to raise - GIGAZINE

"HummingWhale" is a new malware that seems to be derived from such HummingBad. The surprising thing about this malware is that code is included in applications that are normally distributed on the Google Play Store like "Whale Camera" below. About 20 kinds of applications are downloaded 2 million to 12 million times respectively, and it is said that it is a mechanism to execute advertisement fraud cleverly by operating a virtual machine in the terminal .
This virtual machine can operate without being noticed by the user of the terminal, it is possible to create a fake ID and access the Google Play Store and give a high evaluation of lies to an application containing malware. Check Point researchers talk about the high level of danger, "users should recognize that they should not trust the app because of high evaluation even in the official app store."
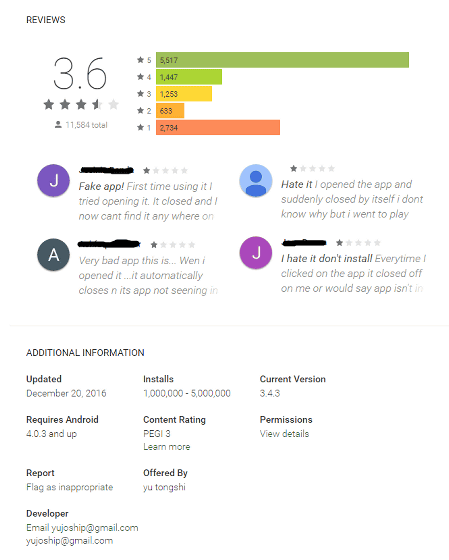
According to Check Point, HummmingWhale uses the extended function "DroidPlugin" developed by a technician based in China based company "Qihoo 360" to run this virtual machine.
Damage is thought to occur mainly in countries other than Japan, Check Point is a diagnostic application for those who want to check infectionOfferdoing. Also, from Lookout other than Check PointSimilar applicationsIt is said that it is provided. In addition, it is possible to confirm the infection by a technically adequate person by confirming that the terminal is connected to the control server at the URL "app.blinkingcamera.com". Because the application with malware installed is named in the form of "com.XXXXXXXXX.camera" like "com.bird.sky.whale.camera", it is also possible to check this way It is one.
Related Posts: